Summary
BlackMatter is a ransomware campaign that has been terrorizing Linux users since late 2021. The variation is written in C++ and specifically targets VMWare ESXi servers. VMWare ESXi servers are a common target for ransomware attacks because they maintain the hard drives for numerous virtual machines. Thus, attackers can take out hundreds or thousands of machines by attacking a single server, incentivizing the victim to pay out.
BlackMatter utilizes a combination of remote command-and-control (C2), along with static internal cryptography keys to encrypt files. The gang does not depend on an internet connection to encrypt target files. It also has the capability of leveraging PKI with an embedded public key, allowing for encryption without C2.

Key Indicators of Compromise
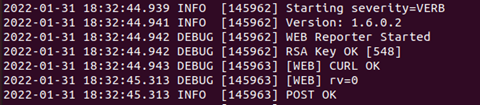
1) /tmp/main.log
The BlackMatter log provides information on the malware version and whether certain steps in the encryption and communication process succeeded.
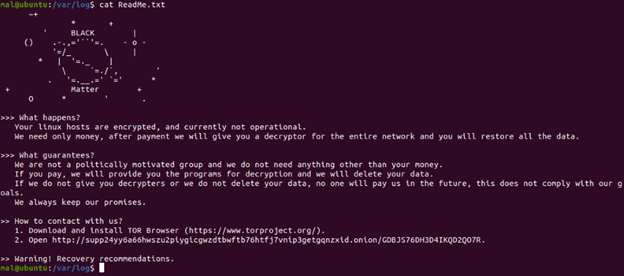
2) ReadMe.txt
The “Readme.txt” file is a ransom note that asks the victim to initiate communications with the Linux ransomware gang. The Linux ransomware gang will subsequently request payment in the form of cryptocurrency in exchange for the keys to decrypt the virtual machine files.
3) .<HEXCHARACTERS> 24 Bytes in Length
The malware places hidden files (dot prefixed) with hexadecimal character names in any directory containing encrypted files. This process allows the malware to identify which directories it has previously encrypted.
The filename is generated using the lesser-known Tiger hash function: https://en.wikipedia.org/wiki/Tiger_hash_function
![]()
4) /tmp/.<UID>
This file is a process ID file (PID file), also using the dot prefix to hide itself. It contains only the PID of BlackMatter’s main thread.
- Note that this file is only 7 bytes long – its name holds more data than the file itself!
![]()
5) Network traffic from the device to mojobiden[.]com – This domain was associated with BlackMatter command and control.
Upon initial execution, BlackMatter performs several preliminary checks on the victim’s system. It seeks to identify what kind of device it is running on, important operating system information, and its privilege level. One critical check is on the presence of the esxcli binary found on ESXi systems.
![]()
If found, BlackMatter uses esxcli to prep the system for an attack by manipulating the firewall. If the /sbin/esxcli program is not found, BlackMatter carries on with the rest of its attack.
BlackMatter then proceeds to catalog files of interest on the victim device. Targeted directories include /var/log and the ESXi specific /vmfs/volumes/. BlackMatter will spawn several threads to check permissions on each identified file, and perform encryption as required.
The images below show an in-progress encryption routine. BlackMatter encrypts the file in portions with AES keys. The AES key itself is encrypted with the embedded public key, therefore securing the symmetric key with an asymmetric key that only the malware author would have access to.
 |
 |
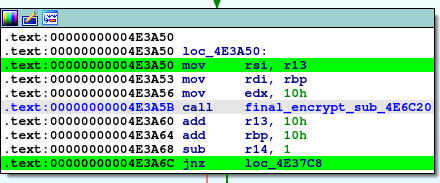
Note that the encryption subroutine is listed below at address 0x4E3A50. Due to indirect function calling, there is no immediately apparent path to this function from BlackMatter’s main function. This indirect usage of the function is an obfuscation technique to make the malware more difficult to reverse engineer.
Once BlackMatter has run its course on the victim’s system and all the available target files have been encrypted, BlackMatter will delete its own binary from disk. BlackMatter uses the “unlink” syscall to delete itself. Once the binary has been deleted from the disk, BlackMatter will exit. It does not attempt to restart the system or show a ransom note. Instead, it relies on the victim to notice the “ReadMe.txt” ransom notes placed adjacent to encrypted files.
How to Protect Yourself
There are several approaches you can take to stop BlackMatter and other similar ransomware threats. Most BlackMatter ransomware attacks take advantage of weak or compromised credentials. Ensuring you have strong passwords on your Linux servers can help defend your systems. You can also try using IOCs to block dangerous hashes and IP addresses. Unfortunately, the BlackMatter Linux ransomware gang is relatively sophisticated. They continuously change the hashes of their malware, and the IP addresses they use for malicious command-and-control. What is a security team to do against sophisticated threat actors like BlackMatter?
We think ZeroLock is the ideal solution for handling ransomware on your Linux servers. ZeroLock uses advanced, proprietary behavioral analysis to detect all forms of ransomware. Because ZeroLock relies on behavior and not hashes, our solution is robust against the techniques threat actors use to adapt their malware. Despite how the BlackMatter Linux ransomware gang modifies their malware hashes or their command-and-control IP addresses, ZeroLock will detect, stop, and automatically remediate the attack.
For more information, contact [email protected].
