Explanation of Cryptojacking
One of the most prevalent threats facing Linux systems today is cryptojacking. This attack occurs when a threat actor infiltrates a target system and re-appropriates resources to mine cryptocurrency for themselves. Because many Linux systems are powerful, well resourced, infrastructure machines with little user interaction, they can make prime targets for cryptojackers. Unfortunately, this means that cryptojacking attacks can go unnoticed for extended periods.
The article below reports on supercomputers used for COVID-19 vaccine research falling victim to cryptojacking. These types of attacks destroy computational capacity, steal the money and power needed to run IT (Information Technology) systems, and are difficult to resolve. The supercomputers referenced in the article were taken offline for weeks, causing significant delays in critical COVID-19 vaccine research. (See the “How to Protect Yourself” section at the end for suggested security mechanisms).
Cryptojacking Case Study: XMRig
XMRig is commonly used as the cryptocurrency “miner” in cryptojacking attacks. It has the capability to mine several different coins using various algorithms but was primarily built to mine Monero (XMR). There are several reasons XMRig is popular with malicious actors.
First, Monero is virtually untraceable by traditional means. Unlike many other cryptocurrencies, Monero coins are fungible, meaning each one is indistinguishable from the others. This quality differs from popular coins such as Bitcoin. Each Bitcoin is unique, making it easier to track. Although we may not know who is associated with each wallet a Bitcoin moves between, we can link together wallets which have held the same coin and trace back transactions. Monero’s fungibility means that it is not traceable in the same way. This encourages threat actors to mine Monero, as it is untraceable and allows them to freely spend their illicit earnings.
Second, XMRig is open source. Attackers have easy access to XMRig source code, including the ability to custom compile and modify XMRig executables with relative ease. This quality makes XMRig very difficult to detect with signature-based methods, because it is easy to modify the underlying executable code.
Third, XMRig uses the RandomX hash algorithm for Monero mining. With RandomX, an average CPU found on any system has a chance of making meaningful contributions to the mining effort. Enabling any Linux system to become a viable target, not just those with powerful GPUs or specialized hardware. (More on RandomX below).
Fourth, XMRig is a legitimate application used by many for personal mining. This can make it difficult to distinguish malicious XMRig instances from nominal system behavior.
RandomX/Monero Overview
RandomX is a mining algorithm designed to be resistant to specially designed machines. It accomplishes this goal by producing random code for each run, which will be executed within a lightweight virtual machine. The output of the random code is used in a hash calculation, and the hash is used to mine Monero. The image below shows the function calls for these events in an XMRig Linux executable.
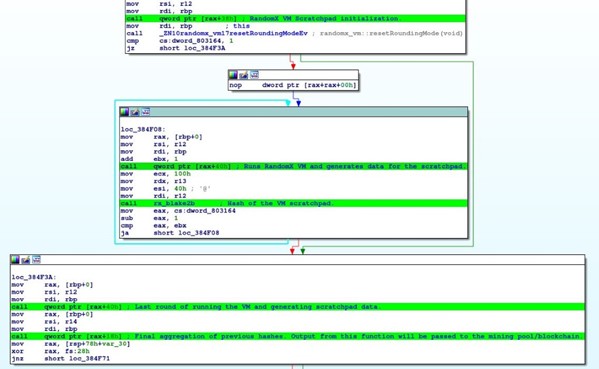
The lack of predictability in this algorithm makes it extremely difficult to build a machine which is significantly superior to others for mining using RandomX. Cryptomining is a competitive endeavor, as a limited amount of any given coin will be mined over a set period. RandomX allows more commonplace devices such as desktop PC’s, laptops, servers, and even smartphones to meaningfully mine Monero. This is in stark contrast to other popular coins such as Bitcoin and Ethereum, whose mining environments are dominated by special, highly efficient machines which have been purpose built for their respective algorithms. This characteristic makes Monero, the RandomX algorithm, and the XMRig miner incredibly attractive to opportunistic attackers. An attacker does not need to target sophisticated cryptomining systems to be able to make a profit.
It is worth noting that the RandomX algorithm was also designed to be botnet resistant. Running the algorithm will leave behind a trace in the CPU registers, which should be reliably detectable. A proof-of-concept program for windows was developed to accomplish this and can be found in the link below. Unfortunately, this detection method has proven ineffective and attackers are still using RandomX in botnets every day.
Implementation for XMRig
Attackers have a wide array of methods by which to access targeted systems. Most attackers do not have endless resources or access to sophisticated research and will instead use common vulnerabilities at the application level. Vulnerabilities commonly exploited include the log4j vulnerability disclosed in 2021. Something as simple as an underprivileged user without an SSH password combined with the recently discovered ‘dirty pipe’ privilege escalation, could lead to an attacker having enough access.
Once an attacker has breached a target system, it is easy to begin mining using XMRig. The XMRig instance will need to be configured with a few options specific to the attacker, including the mining pool they wish to participate in and the address of their Monero wallet.
![]()
These options can be conveniently set using a configuration file. However, most attackers will opt to provide all configuration options as command line arguments as seen above. This practice limits the number of files the attacker moves to the victim system therefore lowering the attacker’s chances of being discovered.
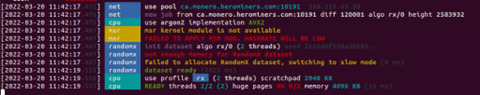
The above image is an example of XMRig output at the command line on a resource limited machine. While this configuration is certainly more user friendly, XMRig can be run as a background process by adding further arguments to the program at the command line.
XMRig will establish communication with the mining pool or blockchain node it was configured to use, receive work from the Monero blockchain, and begin mining with RandomX. XMRig will run indefinitely until it is killed, or the target device is turned off. An attacker may attempt to provide persistence for XMRig on Linux systems by manipulating crontabs, systemd init files, or placing a persistent backdoor.
How to Protect Yourself
One of the best ways to protect yourself from cryptojacking attacks of any kind is to harden your network and prevent intrusion. No network is impenetrable, but most cryptojacking attacks are not highly sophisticated. A hardened network can go a long way to discouraging and preventing breaches. Web proxies, well configured firewalls, and secure authentication practices are critical components of good cybersecurity hygiene.
Even the most hardened system will eventually be vulnerable. In-depth defenses are crucial. Having security mechanisms in place at the network border, on internal traffic, and on individual machines is a huge step toward robust security. Actively watching for signs of cryptojacking in network traffic and in running processes is the only way to know it is happening.
We believe our ZeroLock software is a great option for detecting and preventing cryptojacking. At Vali Cyber, we use innovative machine learning algorithms and filtering mechanisms to track and detect the behavior of cryptomining malware. We can confidently say that we detect cryptojacking with an exceptionally high efficacy rate of 97%. Our high efficacy detection methods are combined with a novel approach to sampling program behavior that results in exceptionally low computational overhead. As a result, ZeroLock typically uses less than 5% of the CPU while protecting your systems from threat actors.
For more information, contact [email protected].
