ZeroLock defends against many kinds of attacks, including ransomware. The Vali Cyber Threat Intelligence team regularly red teams the agent to ensure it responds effectively to sophisticated, evolving threats. The Threat Intelligence team developed a novel ransomware sample with the intent of bypassing ZeroLock’s defenses. This malware was created for the express purpose of research, and it will never leave Vali Cyber systems.
After extensive review of ZeroLock’s capabilities, a hypothetical attack vector was formed. By making use of rarely used Linux system calls, a malware executable might be able to circumnavigate detection by the agent. The system calls in question are “name_to_handle_at” and “open_by_handle_at”. These functions were originally designed for use on user-space file servers over a decade ago, although they continue exist on almost every modern Linux machine. Competent malware developers could be expected to utilize them in an attack if they thought there was benefit to be gained.
Below is a sampling of the code written, using the “name_to_handle_at” and “open_by_handle_at” system calls. The usage of these system calls is the key to this attack vector.
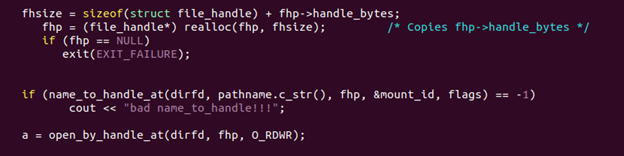
Once the Threat Intelligence team produced the malware, it was tested in a closed system on ubuntu and CentOS hosts, along with a known and detectable ransomware sample as a control. When both samples were run on the test systems, the control was detected each time it attempted to encrypt. The novel malware, however, was able to avoid detection each time and encrypt files on the test systems.
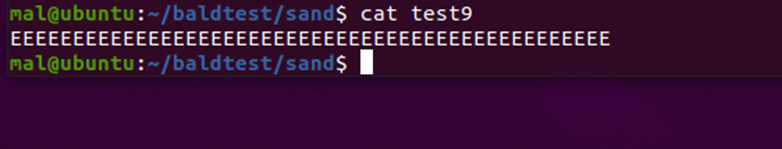
The below screenshot shows the output of a text file filled with the letter ‘E’ repeated before the ransomware is run.
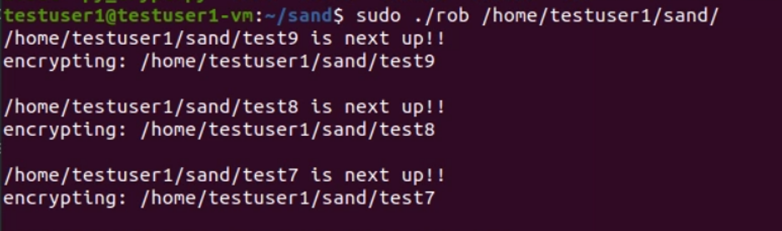
Below is a screenshot of the newly developed ransomware at work, avoiding detection.
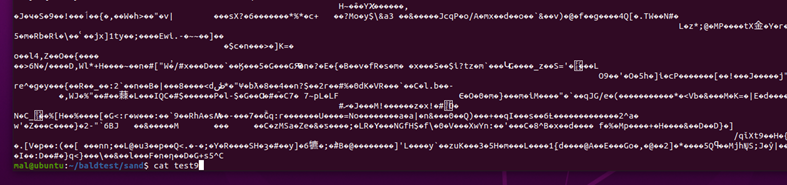
This screenshot shows the same file as above (test9), but after encryption.
We have shown that this ransomware was able to encrypt files on the target machine and does so undetected by ZeroLock. It also goes undetected by major open-source anti-virus distributions, such as ClamAV. The screenshot below shows the result of ClamAV scanning the directory with the ransomware sample. ClamAV does not correctly assess the sample as dangerous.
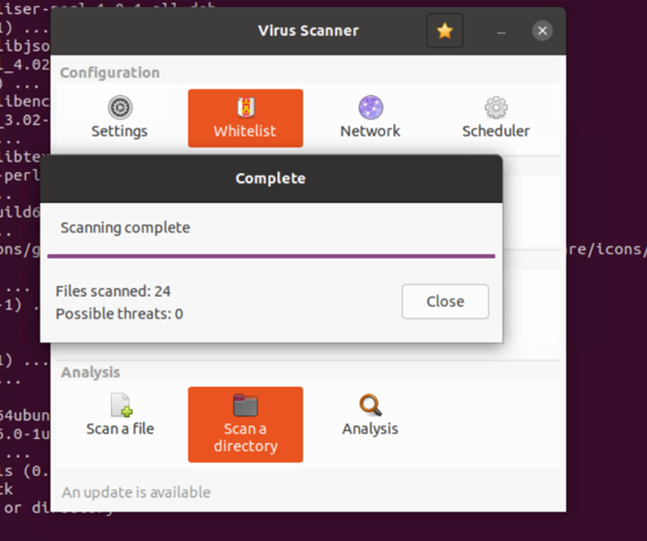
This research has been provided to the ZeroLock development team, and the deficiency has been addressed. New versions of ZeroLock detect these creative ransomware techniques by default. The Vali Cyber Threat Intelligence Team will continue to produce novel malware research to ensure our software is constantly one step ahead of sophisticated threat actors.
For more information, contact [email protected].
