Aliases
|
|
Get Threat Intel and Security Updates Delivered to Your Inbox.
Profiling

Image of convicted Scattered Spider member, Noah “King Bob” Urban.
Demographics: Primarily young operators (assessed ages: 13–25 years old), predominantly fluent/native English speakers.
Structure: Not a fixed “group” but a loose collective of individuals operators.
Expertise: Highly adaptive, “cloud-savvy” attackers, skilled in abusing Identity and Access management (IAM) misconfigurations and MFA bypass techniques rather than traditional perimeter exploits. Has demonstrated a repeatable ability to pivot into VMware ESXi environments, aligning with RaaS partners to deploy ransomware or exfiltrate workloads directly from the hypervisor layer.
Social Engineering: Heavy reliance on vishing, smishing, and SIM swapping.
Motivation
Financial gain via data theft, extortion, and ransomware.
Timeline
2022 – Emergence
- Scattered Spider (UNC3944 / Octo Tempest) appears, targeting telecoms with SIM swaps, MFA fatigue, and SMS phishing.
2023 – Casino Hacks & RaaS Entry
- September: Breaches MGM Resorts (100M) and Caesars Entertainment (Caesars reportedly paid ~$15M).
- Partners with ALPHV/BlackCat to deploy ransomware.
2024 – New RaaS Partnerships
- October: Shifts alliances to RansomHub and Qilin affiliates for deployment-based attacks.
2025 – Retail Hit & Industry Expansion
- February: Breaches Marks & Spencer via DragonForce ransomware, disrupting 1,049 stores and dropping stock ~7%.
- Upgrades phishing kits to target Klaviyo, HubSpot, Pure Storage, Nike, Instacart, and more.
- FBI warns of expanded targeting: airlines, retail, insurance, and IT contractors.
Current Status (Sep 2025)
- Operator Noah “King Bob” Urban sentenced to 10 years for SIM-swap and crypto theft.
- Group remains active, leveraging RattyRAT and DragonForce ransomware against VMware ESXi servers.
Tactics & Techniques
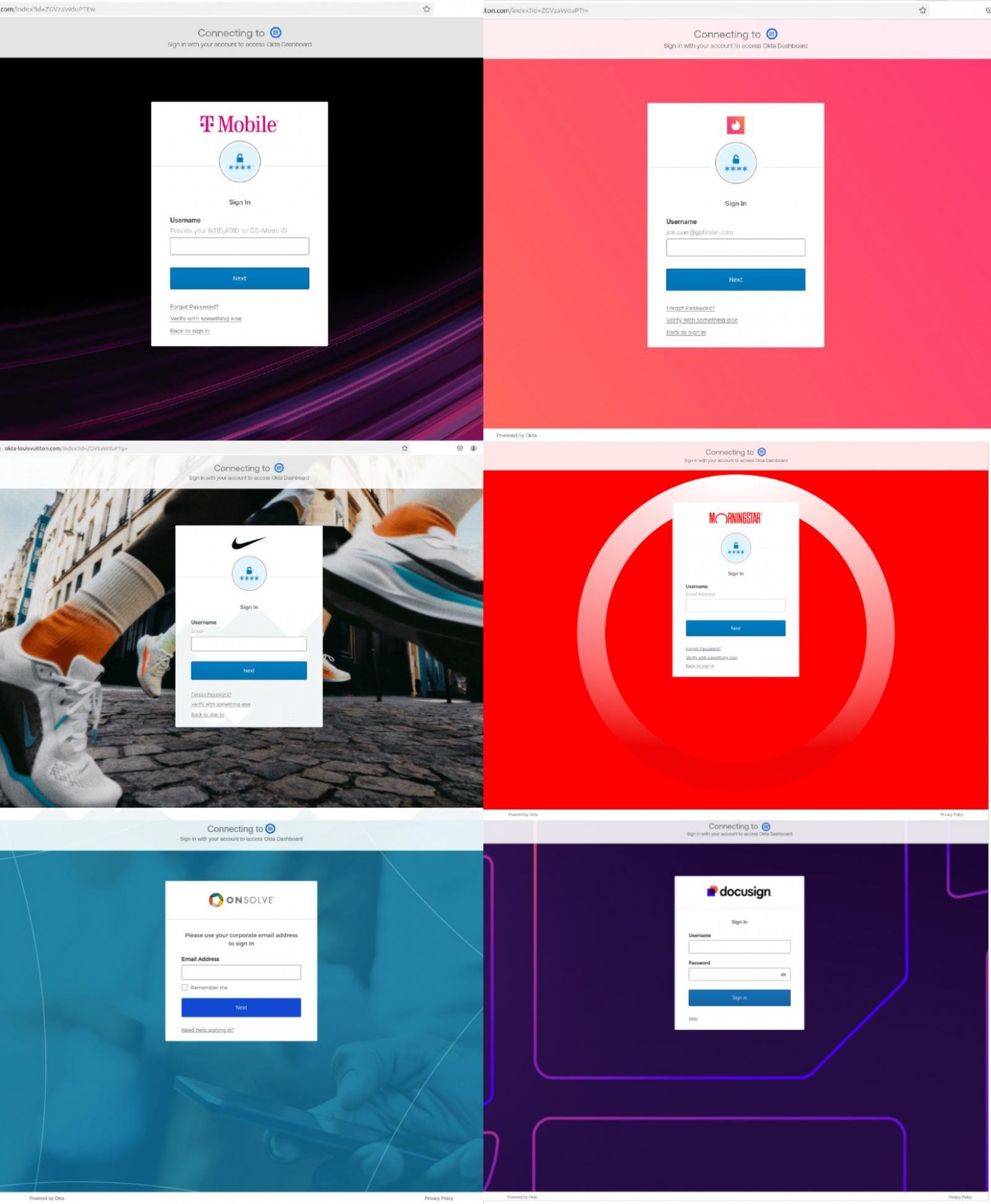
Scattered Spider phishing pages.
Initial Access
- Smishing/Vishing/Phishing (T1566, T1566.002/T1566.004), SIM Swap (T1451), Push Bombing/MFA Fatigue (T1621), AiTM pages via Evilginx (T1557), etc.
Lateral Movement/Privilege Escalation
- Account Takeover (ATO) on IdP platforms (i.e., Entra, Okta, etc.) (T1078.004 / T1133), Domain Admin escalation and credential dumping (T1068 / T1003)
Attack Execution
- Final pivoting into VMWare environment, and deploy ransomware (via RaaS entities) and/or data exfiltration for extortion (T1210 / T1486 / T1041)
Preventative Measures
Defending against Scattered Spider requires both strong identity controls and visibility deeper in the stack:
- Identity and Access Hardening – Enforce phishing-resistant MFA, monitor for SIM-swap attempts, and apply least privilege across cloud IdPs and remote entry points.
- Network Segmentation and Monitoring – Restrict lateral movement opportunities and monitor for abnormal admin tool usage.
- Patch and Configuration Management – Keep IdP, hypervisor, and guest OS environments updated to limit exploitable misconfigurations.
Hypervisor-Layer Defense with ZeroLock®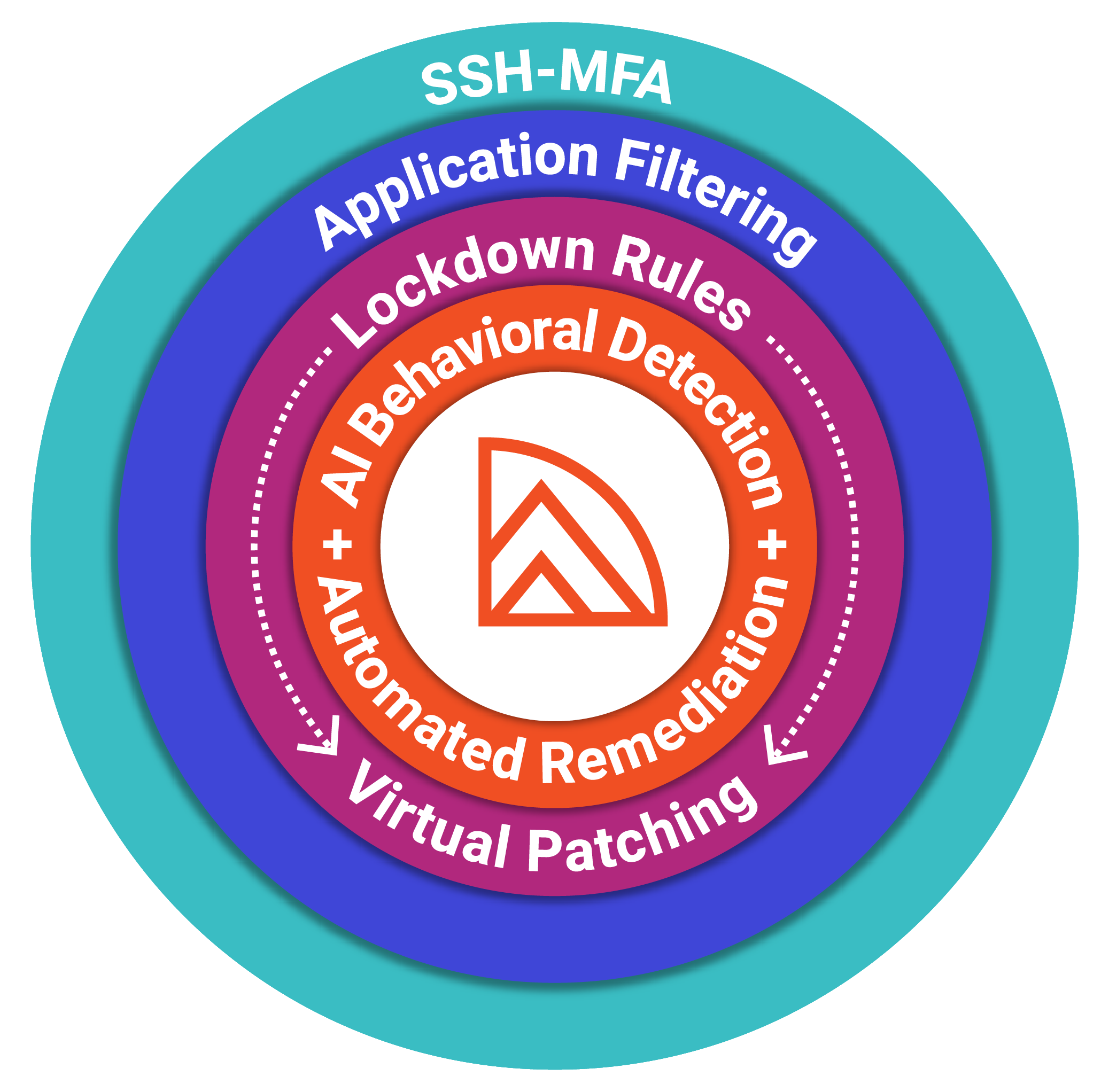
While these controls raise the bar, Scattered Spider’s proven ability to pivot into ESXi environments highlights the need for defenses directly at the hypervisor:
- SSH MFA Enforcement: ZeroLock blocks weak or misconfigured remote entry at the host.
- Lockdown Rules: Prevents unauthorized system changes that enable ransomware staging.
- Application Filtering: Restricts native ESXi utilities from being abused for lateral movement or stealth.
- AI-Behavioral Detection: Surfaces attacker activity before encryption or exfiltration.
Attack Chain Ecosystem
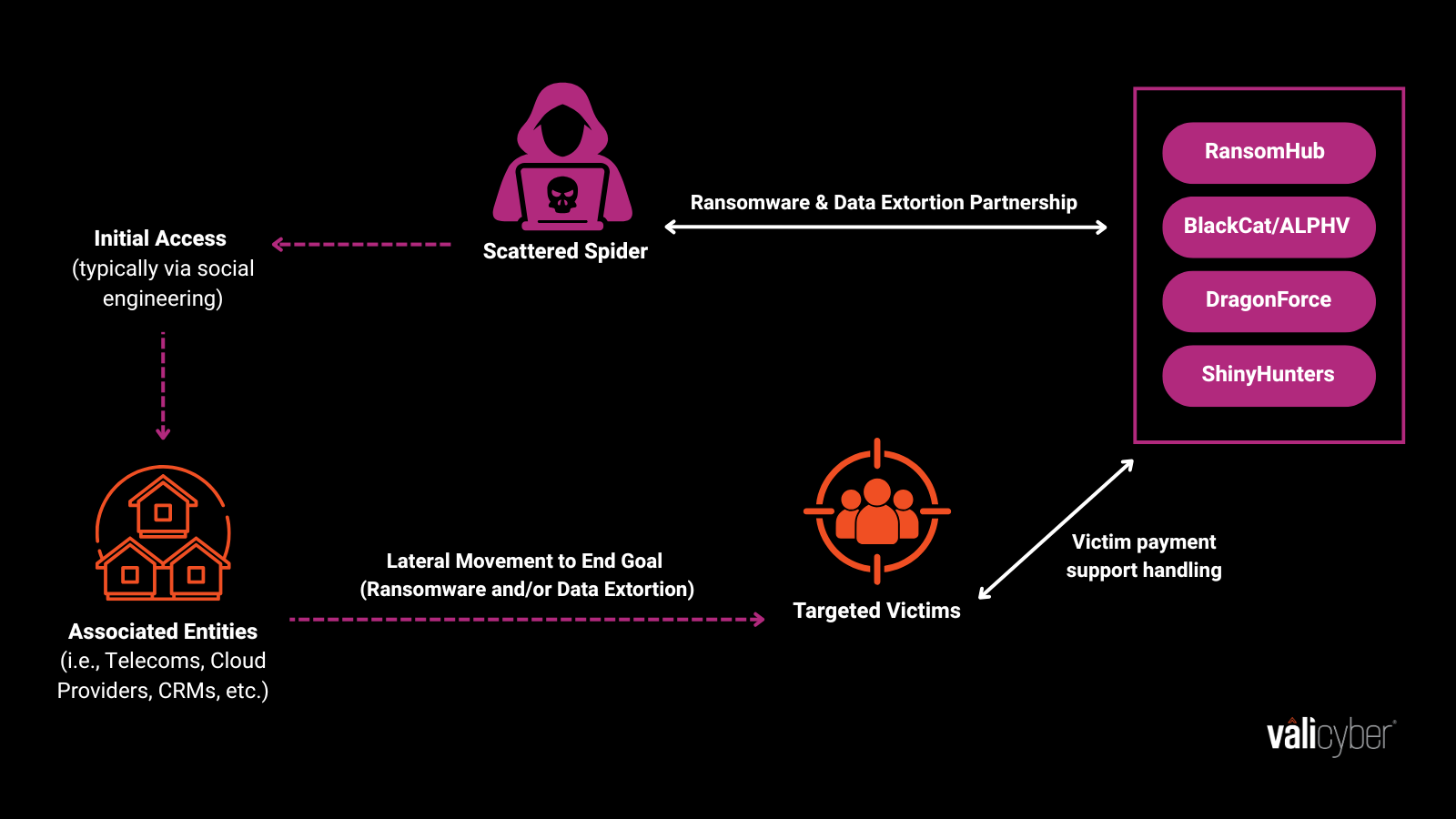
Figure 3: Visual representation of Scattered Spider’s attack chain ecosystem.
References
CISA. (2025, July 29). Scattered Spider. www.cisa.gov. https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-320a
Kelly, P. (2025, June 9). Scattered Spider: Still Hunting for victims in 2025. Silent Push. https://www.silentpush.com/blog/scattered-spider-2025/
Mirage Security – Scattered Spider Attacks: timeline, tactics, and defense tips. (n.d.). https://www.miragesecurity.ai/blog/scattered-spider-a-retrospective
Oluoch, P. (2023, August 17). Scattered Spider: The Modus Operandi. Trellix.com. https://www.trellix.com/blogs/research/scattered-spider-the-modus-operandi/
Parisi, T. (n.d.). Not a SIMulation: CrowdStrike investigations reveal intrusion campaign targeting telco and BPO companies. https://www.crowdstrike.com/en-us/blog/analysis-of-intrusion-campaign-targeting-telecom-and-bpo-companies/
Robb, B. (2025, July 24). Scattered Spider’s expanding web of ransomware attacks. BlackFog. https://www.blackfog.com/scattered-spider-expanding-ransomware-attacks/
Scattered Spider | Cohesity. (2025, July 27). Cohesity. https://www.cohesity.com/blogs/scattered-spider-attack-what-you-need-to-know-about-the-uk-retail-threat/
Scattered Spider: Threat Actor Profile – Cyble. (2025, August 26). Cyble.
Scattered Spider: Three things the news doesn’t tell you. (2025, June 3). BleepingComputer. https://www.bleepingcomputer.com/news/security/scattered-spider-three-things-the-news-doesnt-tell-you/
Shaking up the ransomware game: Introducing Scattered Spider | SANS Institute. (2025, July 7). SANS Institute. https://www.sans.org/blog/shaking-up-ransomware-game-introducing-scattered-spider
U.S. Department of Health and Human Services. (2024). HC3: Threat Actor Profile – Scattered Spider. In HC3: Threat Actor Profile (pp. 1–11) [Report]. https://www.aha.org/system/files/media/file/2024/10/hc3%20tlp%20clear%20threat%20actor%20profile%20scattered%20spider-10-24-2024.pdf
