CLICK THROUGH DEMOS
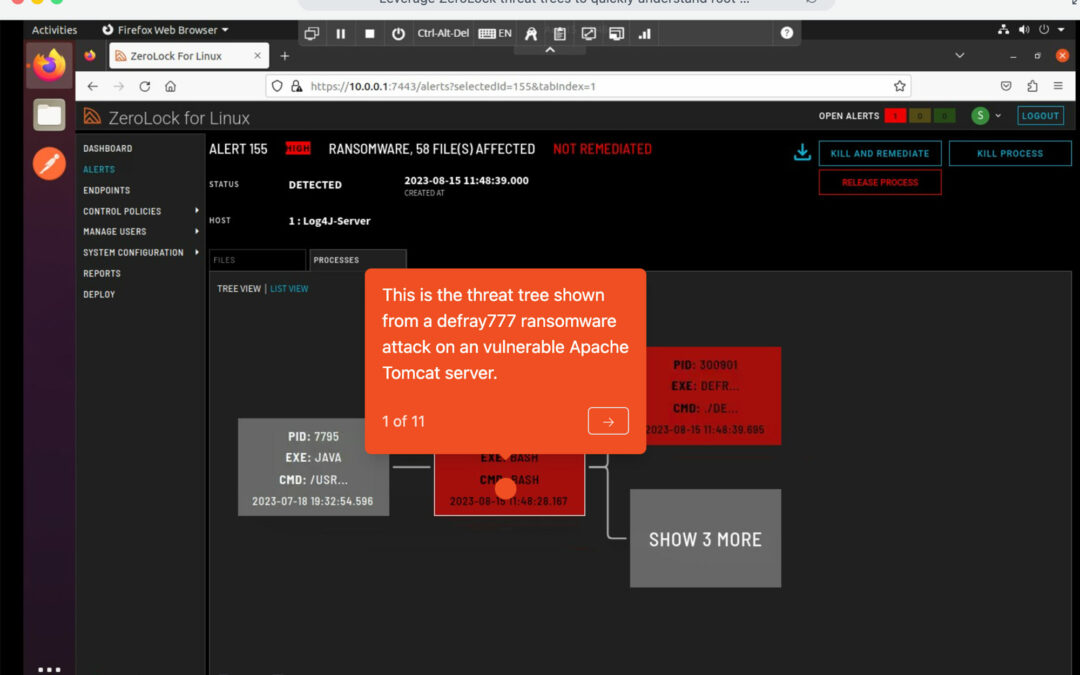
Threat Trees
Leverage ZeroLock® threat trees to quickly understand root causes
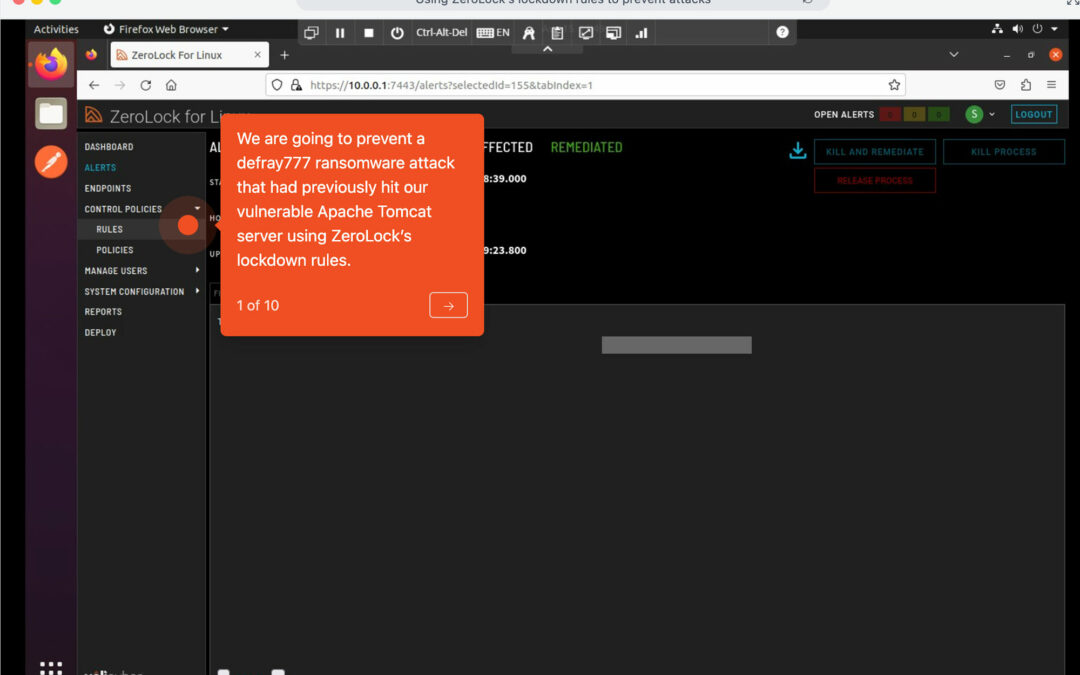
Lockdown
Using ZeroLock® lockdown rules to prevent attacks
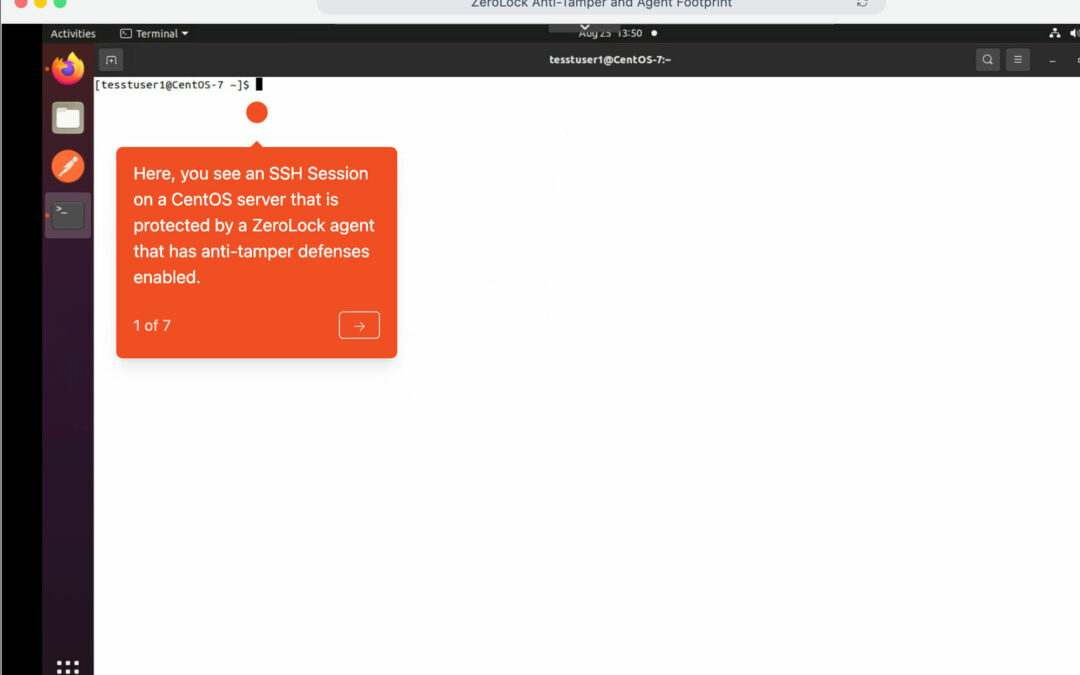
Anti-Tampering
ZeroLock® Anti-Tamper and Agent Footprint
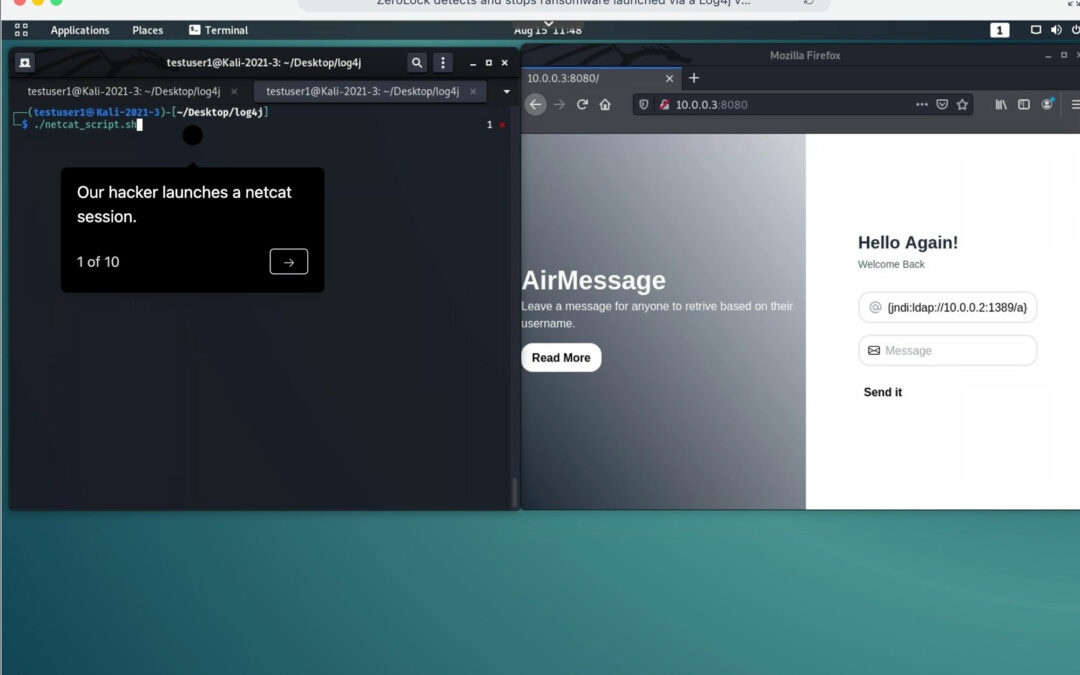
Log4j
ZeroLock® detects and stops ransomware launched via a Log4j vulnerability

SSH-MFA
ZeroLock® prevents unauthorized access with SSH-MFA
