IN THE NEWS

Safeguarding Virtual Infrastructure: Essential Hypervisor Security Controls For Businesses

Dark Web Defense: 19 Tech Experts Share Smart Strategies

Seccomp, eBPF, and the Importance of Kernel System Call Filtering

Securing ESXi Hypervisors: Protecting The Core Of Virtualization

EBPF-Based Security Solutions: Exploring Weaknesses and Mitigation Techniques
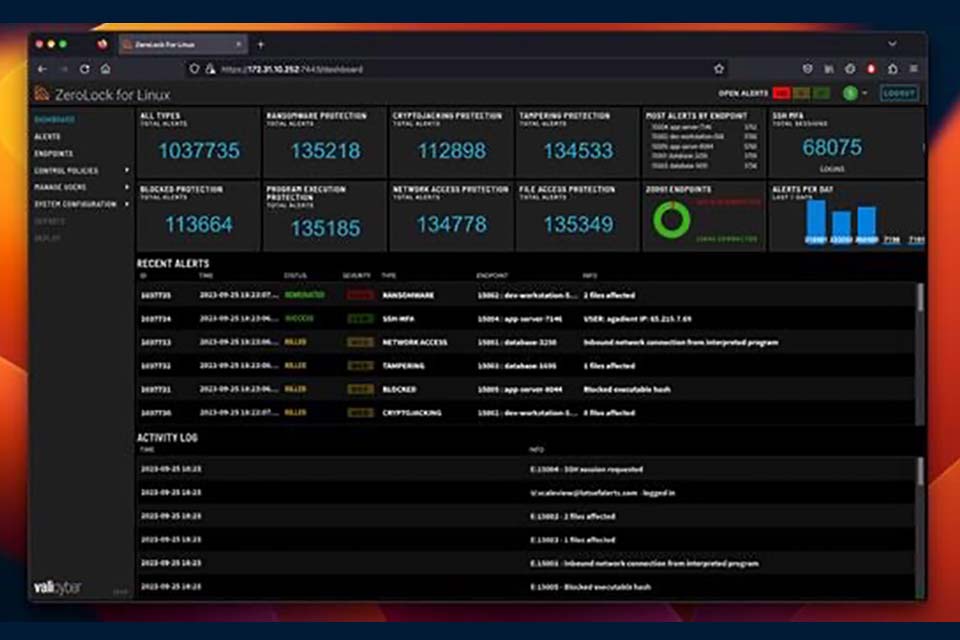
Vali Cyber® Secures $15M in Seed Funding to Revolutionize Linux Cybersecurity

Shifting Runtime Security Left

The Importance Of Runtime Security For Cloud Environments

How To Secure Against WordPress Vulnerabilities with Predictive Analysis Detection & Automated Remediation

The Hidden Costs Of Cybersecurity
Stopping The Growing Ransomware Threat To The NAS Market

