CISOs have spent the last decade hardening endpoints, identities, and cloud workloads. Yet for many organizations, the hypervisor remains dangerously exposed.
Over the past four years, hypervisor-specific ransomware has driven an estimated $1 billion in damage, with VMware ESXi often at the center. Investigations from Unit 42 and Mandiant show a consistent trend: attackers are moving below the OS to evade detection and gain full system control faster.
With vSphere 7.x hitting end-of-support in October 2025 and ESXi-specific ransomware families multiplying fivefold since 2022, 2026 is the year for CISOs to lead the charge in virtualization security.
Modern Threats are Targeting Hypervisors#
Recent analysis from Mandiant and Unit 42 show how attackers are bypassing traditional defenses to go straight for the hypervisor. Mandiant notes that legacy Active Directory trust paths allow a single stolen credential to unlock full control of ESXi and vCenter, creating a direct path to infrastructure-wide compromise.
Similarly, Unit 42 has reported attackers exploiting VMware vulnerabilities to achieve remote code execution and privilege escalation within virtualization environments, with 86% of all 2024 incidents resulting in operational disruption, not just data loss.
Why Virtual Infrastructure is a Blind Spot in Cybersecurity#
Most enterprise defenses are focused on endpoints, applications, and networks, leaving everything beneath the operating system largely out of sight. On top of this, because EDR and XDR agents depend on the guest OS, they can’t operate at the hypervisor level which leaves a dangerous visibility gap.
Ownership of the hypervisor layer often sits between infrastructure and security teams, creating an unintentional governance blind spot: core systems with no runtime monitoring, multifactor authentication enforcement, or consistent patching.
Attackers have learned to exploit this gap for lateral movement and persistence, staying hidden until encryption or shutdown begins, as noted in MITRE’s 2025 addition of ESXi to the ATT&CK framework.
The Real Cost of Hypervisor Breaches#
Once attackers reach the hypervisor, traditional controls become inapplicable. Firewalls protect the perimeter, not the internal east–west pathways attackers use after gaining initial access. From there, techniques like SSH abuse and privilege escalation let adversaries like Scattered Spider move straight to ESXi with little resistance and high impact:
- Marks & Spencer: $402M in lost annual profit and months of downtime
- MGM Resorts: $100M+ in direct losses and a $45M class-action lawsuit
- Co-op Group: $275M in revenue losses and $130M in added operating costs
If your ESXi infrastructure went offline today, would your organization be able to absorb a nine-figure recovery cost?
Preemptive Defense Where It Matters Most#
In the words of Mandiant, “[Scattered Spider’s] playbook requires a fundamental shift in defensive strategy—from EDR-based detection to proactive, infrastructure-centric defense.”
Gartner names this shift toward Preemptive Security a top strategic trend for 2026, and ZeroLock® embodies that shift.
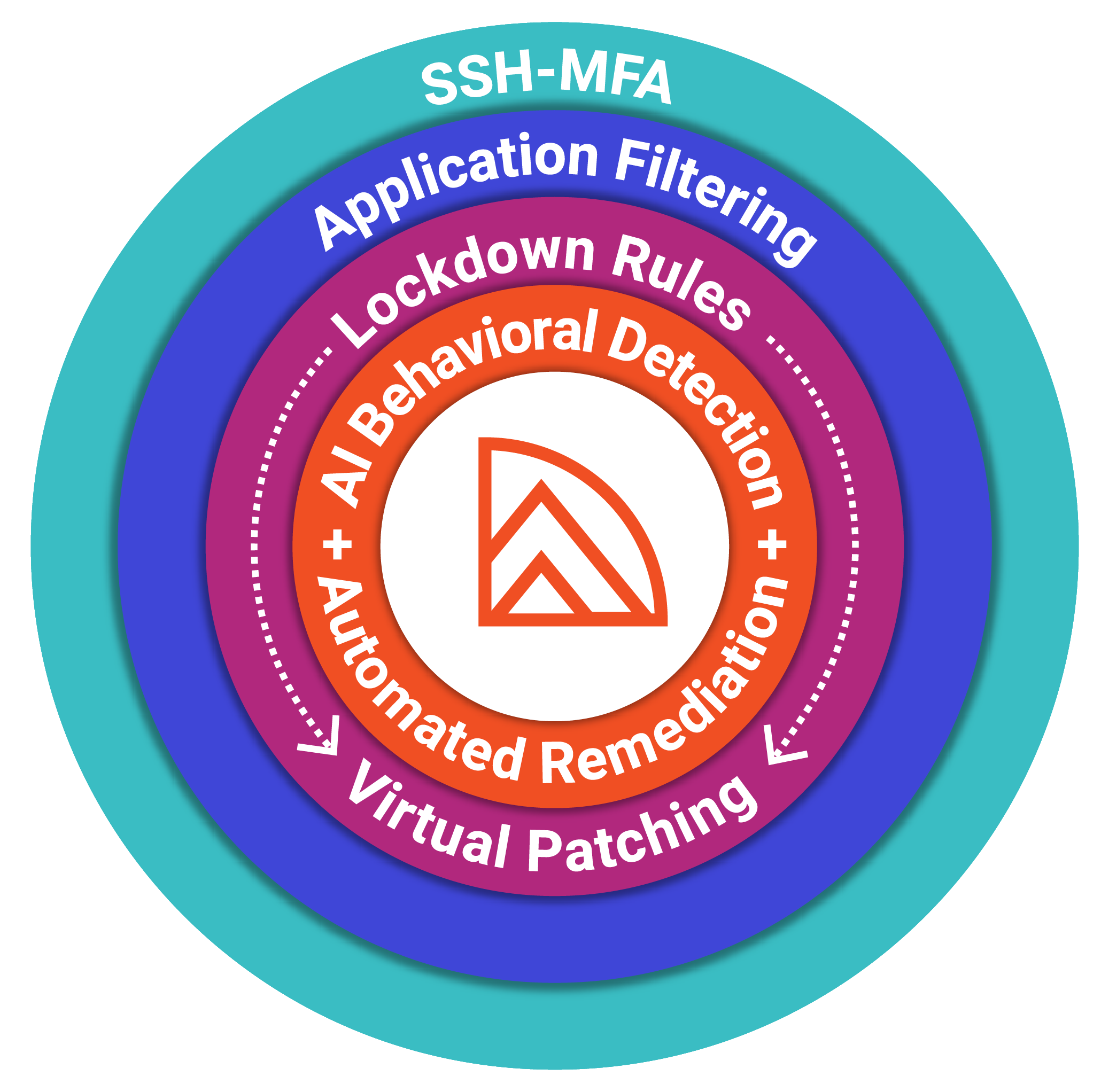
As the only runtime protection built specifically for hypervisors, ZeroLock covers 100% of MITRE ATT&ck v17’s latest ESXi tactics, techniques, and procedures (TTPs), also known as the behavioral patterns adversaries use during attacks, offering:
- SSH Multifactor Authentication (MFA), application filtering, anti-tampering, and virtual patching to harden access and block exploits, providing preemptive defense-in-depth
- AI behavioral detection for real-time threat identification
- Automated rollback for instant recovery and minimal downtime
Together, these capabilities allow security and infrastructure teams to have a proactive stance in their virtualization security, preventing damage for typically less than 1% of what one of those aforementioned Scattered Spider attacks cost.
Making the Case for Infrastructure-Centric Budgeting#
It’s evident that hypervisor compromise is a systemic risk in need of a solution. For CISOs focused on risk-based prioritization, the hypervisor is one of the highest-impact areas.
Failing to address hypervisor risk can lead to prolonged downtime, data loss, regulatory exposure, and board-level consequences. Acting now helps organizations stay ahead of increasing compliance expectations, potential two-month outages, and nine figure losses.
In most cases, hypervisor runtime protection can be deployed for a fraction of the potential impact of an attack.
Want to see for yourself? Learn how ZeroLock protects your virtualization layer by scheduling your personalized demo.
