BRICKSTORM is a custom-made malware family recently being used by suspected state-aligned threat actors out of China. Some of the binary files associated with BRICKSTORM appear to have been made specifically to target vCenter servers and VMware virtualized environments. These pieces of malware exhibit strong persistence capabilities, along with sophisticated means of obfuscating their own traffic, and hiding in plain sight. Command and Control (C2) traffic to and from BRICKSTORM is encrypted and behaves as if it were a benign web-server, and not a malicious service. The designers of BRICKSTORM took great care in ensuring that it would not be easy to notice, and if it were noticed, in ensuring that it would not be easy to remove. The threat actors using BRICKSTORM had full control of the vCenter environment once infected and could use this access to steal VM disks/snapshots as well as creating rogue VMs.
CISA’s recent disclosure of the BRICKSTORM campaign highlights a critical shift in attacker tactics: the virtualization layer is now a primary target. These operations leverage compromised credentials, deploy persistent backdoors, and even create rogue VMs to maintain long-term access. Traditional perimeter controls and jumpboxes alone are insufficient. Vali Cyber’s ZeroLock provides hypervisor-native security designed to address these exact challenges.
Preventing SSH Abuse
One of BRICKSTORM’s key techniques is exploiting SSH access to ESXi hosts. ZeroLock provides a key control for this technique, the enforcement of multi-factor authentication (MFA) for SSH sessions. This approach helps to ensure that credential theft alone cannot grant attackers entry. ZeroLock applies runtime security directly at the hypervisor layer, monitoring and enforcing policies where BRICKSTORM implants its backdoor. This approach closes the gap left by traditional network segmentation. SSH-MFA significantly reduces the risk of lateral movement into hypervisor environments, from threats like BRICKSTORM.
The Challenge with Jumpboxes
Jumpboxes are often used to provide a controlled access point into hypervisor environments. However, they do not protect the hypervisor itself. Once a jumpbox is compromised, attackers can still pivot into ESXi. Breaches that target network appliances such as those targeting F5 Network’s Big-IP often circumvent network level controls such as jumpboxes. Once an attacker breaks into or circumvents the jumpbox, they have free reign to conduct further operations in the virtualization environment.
Application Filtering
Like many other threat actors, BRICKSTORM leverages foreign executables it brings into the hypervisor environment. Bringing in malware allows the group to produce persistent backdoors for long-term data theft and espionage, as well as possible follow-on system degradation. ZeroLock also provides the capability to filter application execution. This means that when a foreign executable mysteriously appears on a protected system, it’s not allowed to execute. Below, you will find a screenshot of ZeroLock actively preventing the deployment of one of BRICKSTORM’s Golang-written backdoors. This backdoor was identified in CISA’s recent report on BRICKSTORM.
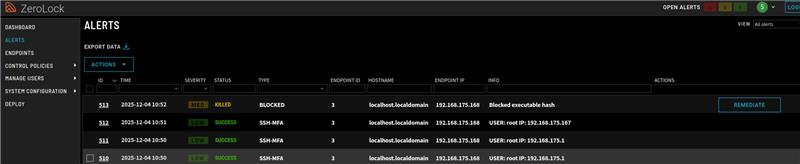
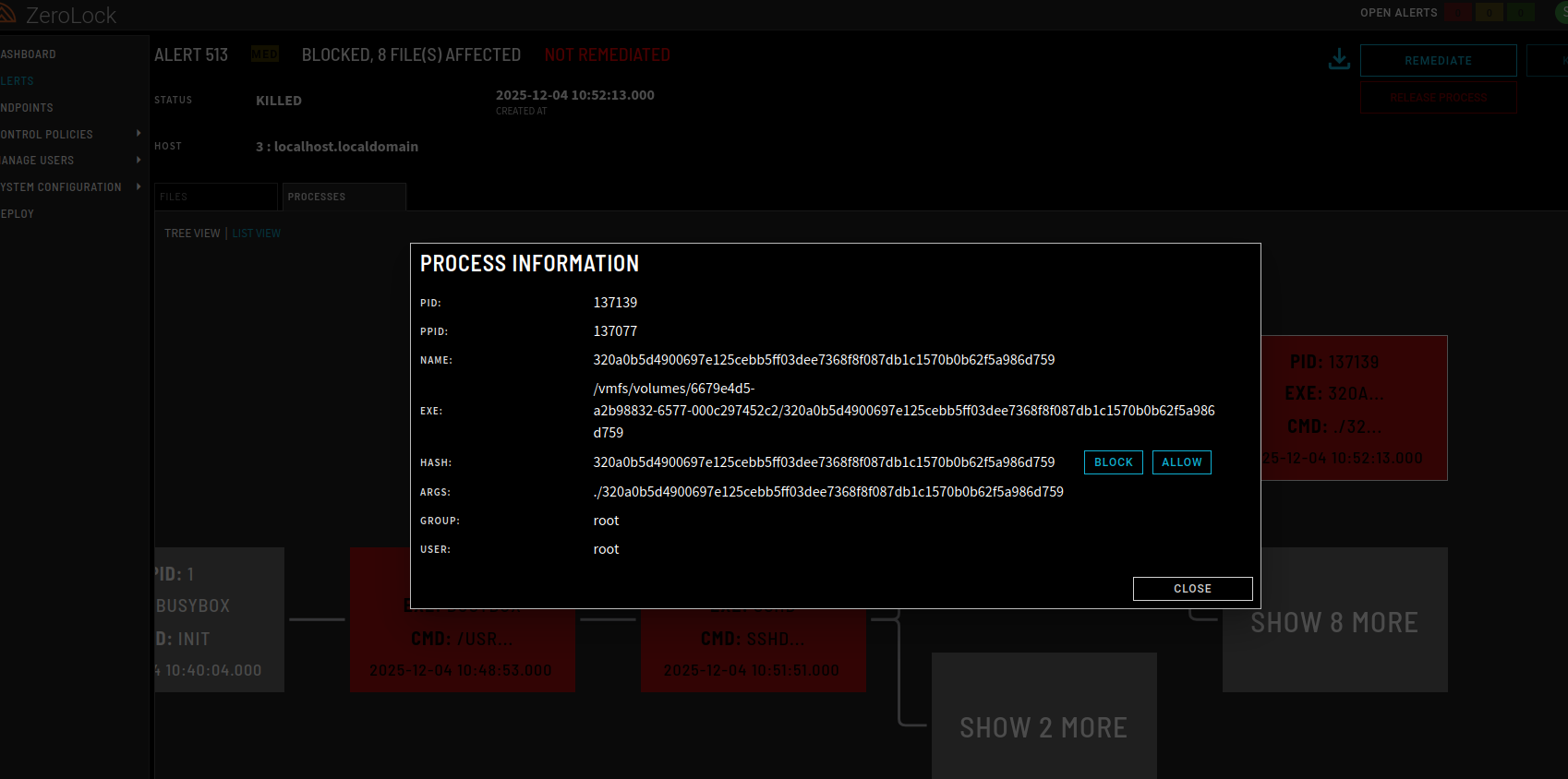
As it catches BRISCKTORM in the act, Zero Lock also provides a wealth of forensic data surrounding the attack. A small subset of this data is pictured below.
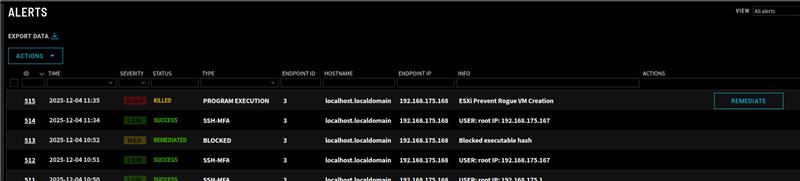
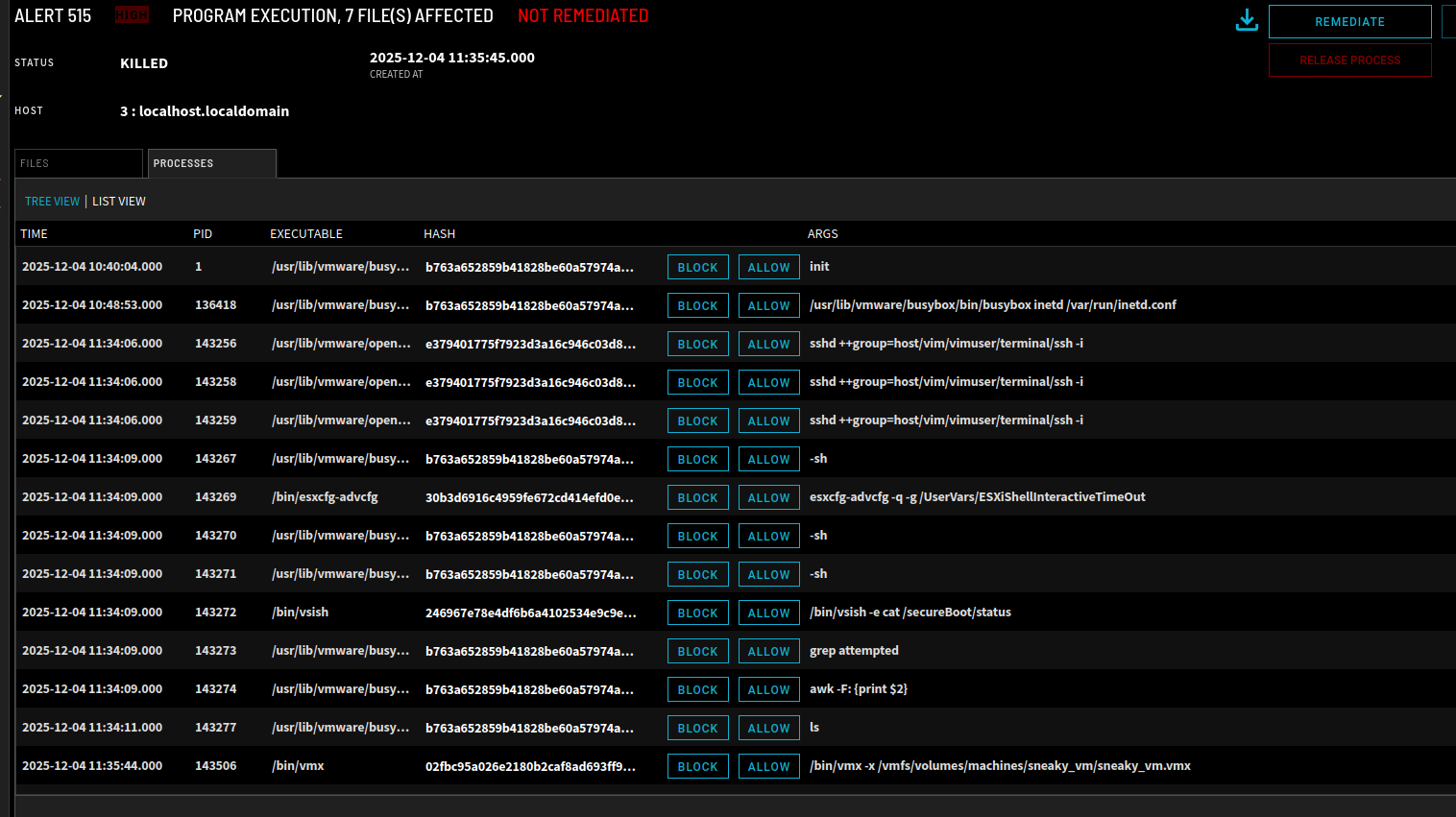
Rogue VM Creation Prevention
One of the more concerning techniques used by BRICKSTORM is the creation of hidden rogue VMs for persistence and data exfiltration. ZeroLock continuously monitors hypervisor activity and flags unauthorized VM creation or configuration changes. Cutting edge-behavioral detection is one of very few ways to detect and protect against advanced malicious behaviors like these. This proactive detection ensures that attackers cannot establish covert infrastructure within your virtual environment.
Conclusion
BRICKSTORM demonstrates that attackers are targeting the virtualization layer with precision. ZeroLock delivers comprehensive protection through SSH-MFA, application filtering, rogue VM detection, and runtime controls. These capabilities provide security where it really matters, the hypervisor.
1 – BRICKSTORM Backdoor | CISA
2 – F5 Breach Exposes BIG-IP Source Code — Nation-State Hackers Behind Massive Intrusion
