As organizations continue to adopt VMware Cloud Foundation (VCF) 9, security remains a top priority. Hypervisors are an increasingly critical layer which—if compromised—can give attackers complete control over the environment. VCF 9 has introduced several advanced protections designed to safeguard these workloads against modern threats. While these capabilities are highly effective at protecting virtual machines and applications, they must be complemented by ZeroLock to fully address risks at the hypervisor level. This is where ZeroLock comes in, delivering what Gartner has recently identified as a 2026 priority: Preemptive Cybersecurity that can help prevent attackers from accessing critical infrastructure.
ZeroLock: A Preemptive Approach to Hypervisor Security
ZeroLock represents a shift in security philosophy. Rather than relying solely on detection and response, it focuses on prevention at the earliest possible stage. By operating directly at the hypervisor layer, ZeroLock ensures that threats targeting the foundation of virtualization are neutralized before they can impact workloads or infrastructure. This proactive approach complements VCF 9’s workload centric protections, creating a more comprehensive security posture. ZeroLock uses advanced behavioral detection and prevention to ensure that even threats which have never been seen before can be mitigated. This unique technical capability allows ZeroLock to implement protections like multi-factor authentication for SSH sessions, strong process filtering, highly configurable behavioral detection in the form of lockdown rules and virtual patches, and even AI-based ransomware detection.
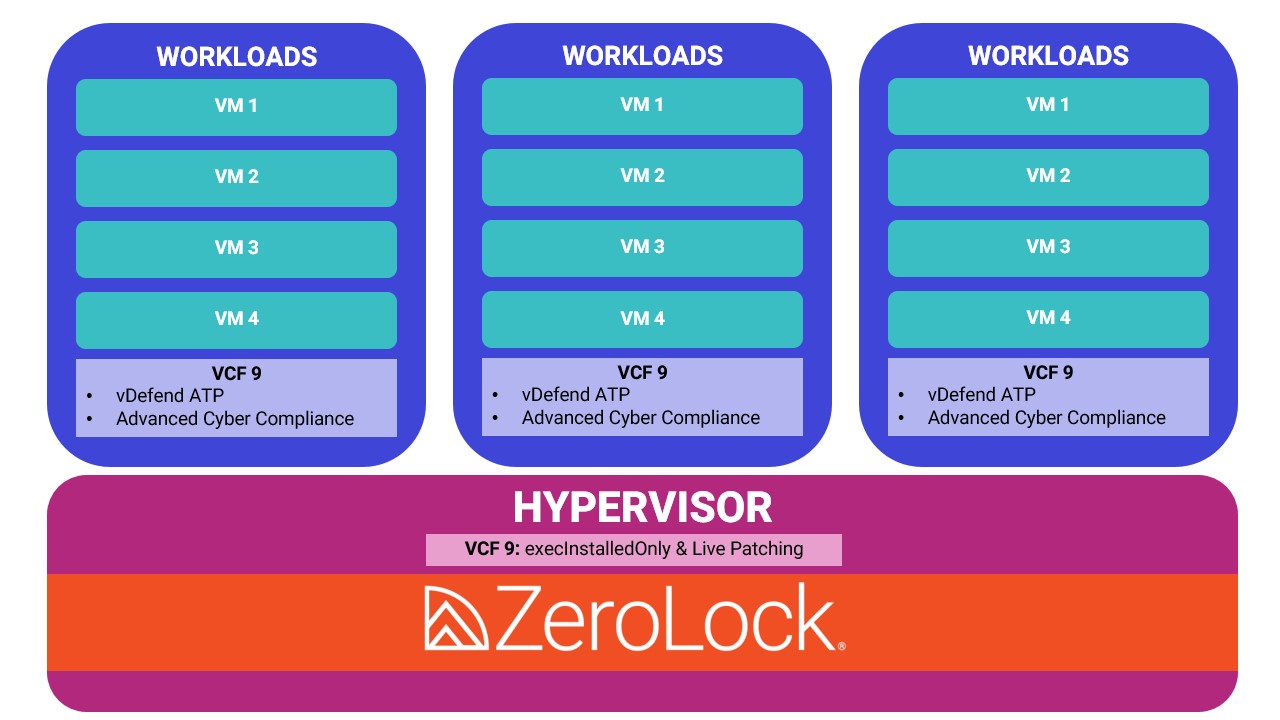
VCF 9 Security: Designed for Workloads, Strengthened by Preemptive Hypervisor Protection
VCF 9 includes features such as vDefend Advanced Threat Prevention, which provides deep inspection and threat prevention for virtual machines and Advanced Cyber Compliance, which enforces security configuration, provides disaster recovery in the event of ransomware attacks, hardened container images, and secure computing enclave support for workloads.
While these capabilities are essential for protecting application workloads, organizations seeking a truly comprehensive security posture should also consider the hypervisor—the foundational layer of virtualization—to ensure business continuity through a thorough, painless patching strategy and prevent living-of-the-land attacks. By extending protection to this layer, solutions like ZeroLock complement VCF 9’s strengths and help address emerging risks.
Why Protecting the Hypervisor Is Critical
Live Patching: Operational Efficiency and Reactive Security
Live patching is an exciting capability in VCF 9 that enables infrastructure operations teams to patch hypervisors without reboots. While this approach can significantly increase the speed at which patches are rolled out, patching as a security approach is inherently reactive. Patching requires a vulnerability to be known and fixed.
During Pwn2Own in May of 2025, several significant CVEs were identified in VMware products, enabling escape-to-host exploits. Escape-to-host exploits allow attackers with access to workload VMs to run code directly on the hypervisor, bypassing virtualization sandboxes. Patches for these CVEs were not released until July of 2025, three months after disclosure. The delay in patch creation left VMware environments exposed to the vulnerabilities during this time. When patches are released, it can take time to safely roll them out even with live patching. Infrastructure operators often test patches on a few systems before deploying them at scale to ensure there are no adverse effects within their own environment.
Live patching also has some technical limitations. For example, systems using a Trusted Platform Module (TPM) cannot be live patched even though TPM usage is recommended in Broadcom’s hardening guides.
How ZeroLock can help: ZeroLock addresses the reactive nature of patching and technical limitations of live patching by providing preemptive zero-day protection from exploits at the hypervisor level. Even if a new vulnerability is lurking in the hypervisor, ZeroLock’s continuous monitoring constantly searches for behavior associated with CVE exploitation and ransomware execution and stops these operations before they cause damage. In the case of the Pwn2Own CVEs, ZeroLock users were already protected with existing lockdown rules, ensuring no business disruption.
Advanced Cyber Compliance: Configuration Management At Scale
VMware’s Advanced Cyber Compliance suite includes a configuration management capability using Salt. Salt is a VMware product that ensures all systems in an environment maintain a consistent configuration. Standardizing configuration is important and helps prevent vulnerabilities caused by configuration drift, which can result in some systems lacking desired security settings. However, configurations can only be as secure as the underlying controls that they define and manage.
Often, threat actors will try to tamper with configuration settings on hosts to enable additional operations such as ransomware execution and lateral movement between hypervisors. A prime example of this behavior is demonstrated by Scattered Spider’s ransomware attacks, where threat actors changed SSH configuration settings for many hypervisors within the cluster and moved laterally across virtualization infrastructure.
How ZeroLock can help: ZeroLock complements the workload configuration capabilities of VMware’s Salt by providing real-time prevention of changes to critical security settings. ZeroLock also prevents ransomware execution and lateral movement through its behavioral detection.
execInstalledOnly: Bypassed by Living Off the Land Attacks
The execInstalledOnly feature in ESXi is intended to block execution of non-installed binaries and is enabled in VCF 9 configurations by default. This control is a strong safeguard against certain intrusion techniques, but it can be bypassed as it has two significant limitations:
- It does not stop Living-Off-the-Land (LotL) attacks, where adversaries leverage native ESXi tools such as openssl, nc, and rm, or interpreters like shell and Python, to carry out malicious actions without introducing new binaries. LotL attacks are a growing threat against hypervisors, with more threat actors adopting LotL techniques as security controls crack down on foreign binaries. A recent article by threat researchers at Huntress identified a 700% increase in ransomware attacks against ESXi, many of which leverage LotL techniques.
- Visibility into these events is often dependent on log data, which happens after the fact, can be tampered with easily by threat actors, and can be overwhelming in large environments. ESXi can forward syslog events to SIEMs, that can be autonomously analyzed for malicious activity. This syslog data includes significant amounts of non-security relevant data which can overload SIEMs, slow down networks, and increase costs for log ingestion tools. Security teams are often left sifting through massive volumes of logs to identify relevant alerts, slowing response times, and increasing the risk of missed indicators. Without 3rd party data aggregation tools and significant setup/configuration steps, many actions blocked by execInstalledOnly are likely to go unnoticed. This issue steals valuable time from incident response. Defenders benefit from streamlined workflows, not additional constraints on their time.
In the following sections, we demonstrate how execInstalledOnly stops attacks, and how it can be bypassed. For these examples, we use an ESXi 9 systems configured following Broadcom’s configuration and hardening guides as shown in the screenshot below.
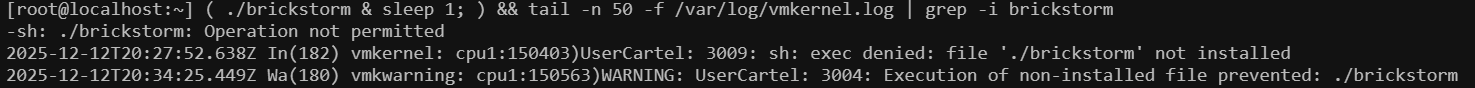
Below is an example of execInstalledOnly being used to block the execution of a malicious binary called ‘brickstorm’. Note that when an attempt to run the binary is made, the user receives a notification from ESXi of “Operation not permitted”. In this instance, we also search through the vmkernel.log to see where ‘brickstorm’ is mentioned. No other feedback is provided to alert the administrator that someone attempted to execute a non-installed executable. Any further alerting or automation must be set up in advance or manually activated.
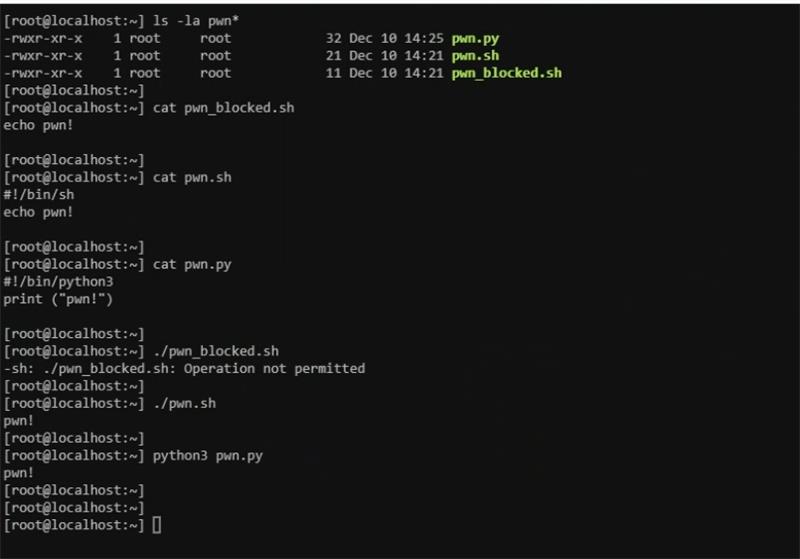
The below screenshot illustrates the limits of execInstalledOnly as a security control when considering LotL attacks. One of ‘pwn’ scripts cannot be executed manually because of the protection. However, when the scripts are called through an interpreter such as Python or sh, they are allowed to execute.
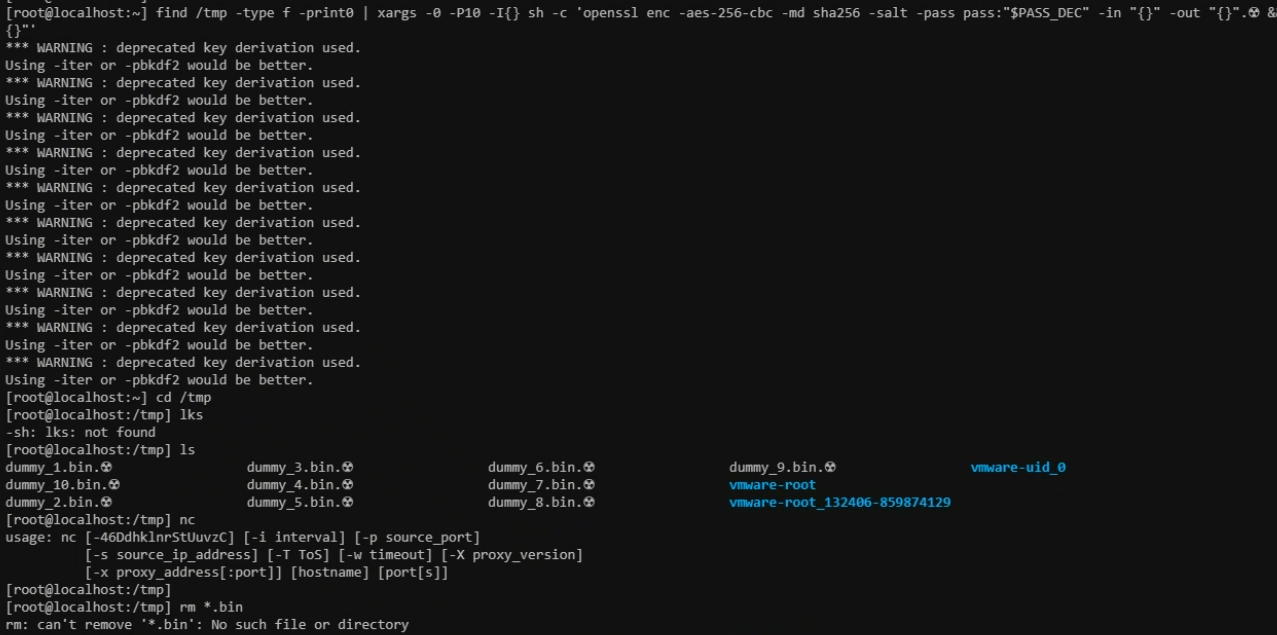
Finally, below is an example of a Living-off-the-Land ransomware attack. This attack takes the form of a fileless script, copied all as one line into the CLI. It leverages only native tools such as ‘rm’, ‘openssl’ and ‘grep’. Unfortunately, it also fully encrypts directories it is targeted at. execInstalledOnly does not prevent this attack, since it leverages only installed utilities.
How ZeroLock can help: ZeroLock addresses these challenges head-on. Its security-focused alerting eliminates the noise associated with raw syslog data, providing clear, actionable insights in real-time that enable rapid decision making. Importantly, ZeroLock delivers preemptive behavioral protection, detecting and stopping LotL attacks before they execute. By focusing on behavior rather than static binaries, ZeroLock closes the gap left by execInstalledOnly and ensures that attackers cannot exploit native tools to compromise the hypervisor. This capability is critical for organizations seeking to harden their virtualization infrastructure against sophisticated threats.
The screenshot below shows how alert data is presented in ZeroLock. The WebUI provides a wealth of forensic data for alerts and events on protected ESXi hosts with no further configuration. If desired, ZeroLock has native utilities to package this data and send it to SIEMs or other data/alert aggregation mechanisms to simplify defender workflows.
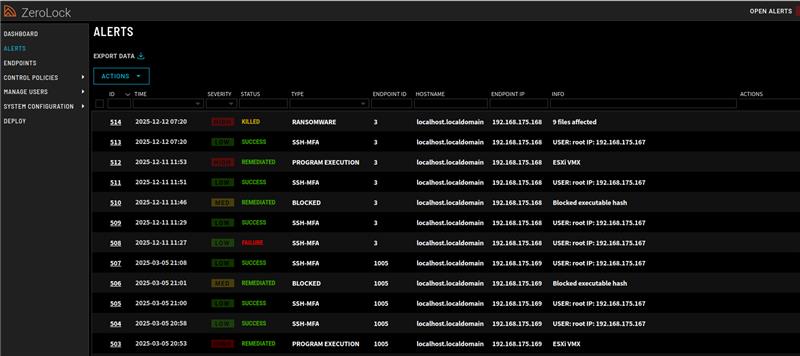
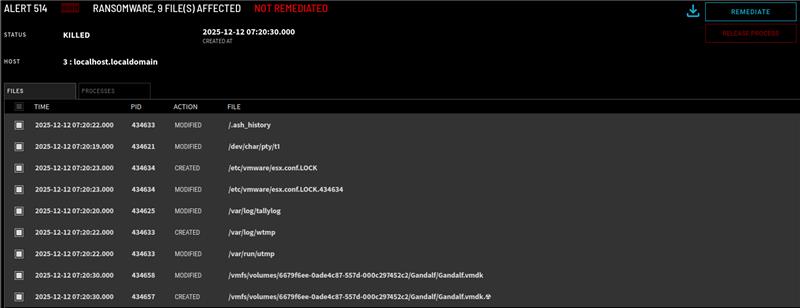
Additionally, ZeroLock provides a more refined and robust set of protections than those available by default on ESXi. The alert shown below was generated from the same LotL ransomware attack that evaded execInstalledOnly. ZeroLock can not only detect this malicious action, but stop it and remediate all file damage done, without any human intervention.
Conclusion
VCF 9 offers exceptional security capabilities for workloads and can be part of a comprehensive virtualization security solution if preemptive hypervisor level protection is also included. While execInstalledOnly is effective at blocking foreign binaries, it leaves blind spots for LotL techniques and creates operational challenges with log management. ZeroLock fills these gaps by providing preemptive defense and streamlined alerting, ensuring that the hypervisor, which is the foundation of every virtualized environment, remains secure. Together, VCF 9 and ZeroLock deliver a layered security strategy that protects both workloads by defending the infrastructure they depend on.
