Aliases
- Akira is the only known alias.
- Associated with other groups known as Storm-1567, Howling Scorpius, Punk Spider, and Gold Sahara
Get Threat Intel and Security Updates Delivered to Your Inbox.
Profiling
Threat Actor Type: Ransomware-as-a-Service (RaaS) targeting Windows, Linux, and virtualization platforms with double‑extortion.
Demographics:
- Suspected Lineage: Overlaps in TTPs, tooling, and wallet usage suggest links to the defunct Conti syndicate (not formally confirmed).
Affiliate Structure: RaaS-style model with affiliates leveraging shared tooling (Akira, Akira_v2, Megazord) and common playbooks across sectors and regions.
Communications & Infrastructure
- Tor-based data leak site plus a distinct Tor negotiation site gated by victim-specific credentials; some leaks distributed via BitTorrent.
- Public brag posts and mass “victim dump” waves observed to amplify pressure.
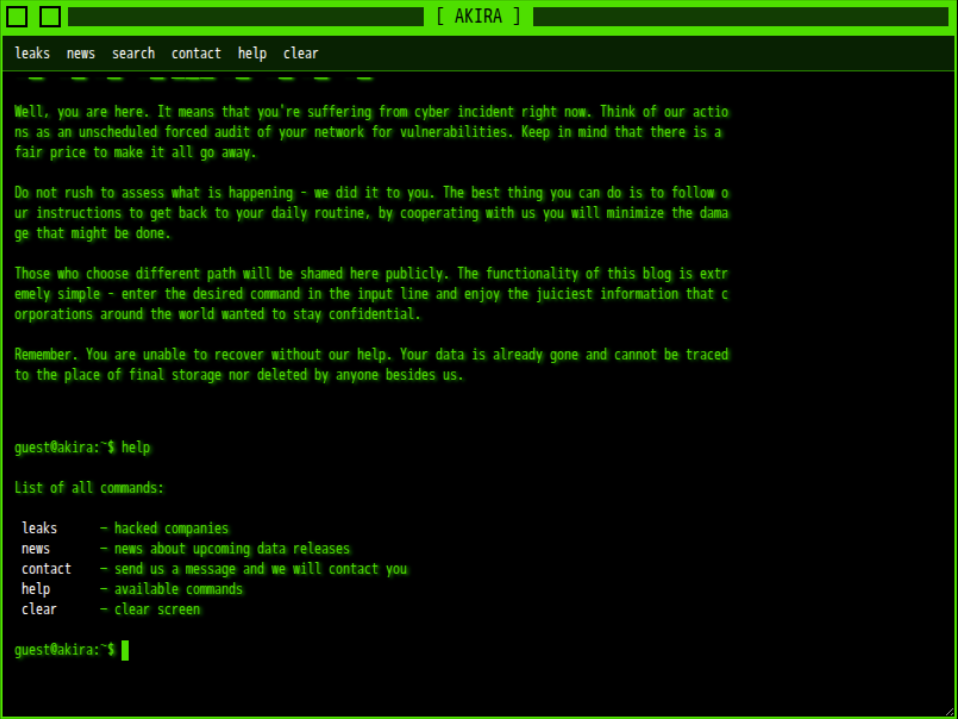
Akira Ransomware leak site in a Tor browser.
Expertise:
- Multi-platform ransomware (Windows/Linux) with a strong focus on ESXi hypervisors; 2025 expansion to encrypt Nutanix AHV VM disk files.
- Rapid encryptors (Akira_v2 / Rust-based) and toolchains for defense evasion and data exfiltration.
Motivations
- Primary driver: Financial gain; FBI/CISA estimate approx. $244.17M extorted by late Sep 2025.

Image from Akira’s leak site.
- Secondary: Notoriety and market share in RaaS ecosystem, evidenced by monthly victim postings and public leak “dumps.”
Timeline & Victimology
March 2023 – Emergence
- Akira appears, initially Windows focus; quickly adds Linux encryptor for ESXi.
2023–2024 – Expansion & Variant Development
- Early C++ variant (.akira); Rust-based “Megazord” (.powerranges) introduced; Akira_v2 emerges targeting ESXi via Rust.
- Campaigns increasingly leverage VPN access without MFA (notably Cisco VPNs).
2024 – Government Advisory
- Joint #StopRansomware advisory (FBI/CISA/EC3/NCSC‑NL) details TTPs and IOCs; >250 orgs and ~$42M by Jan 1, 2024 baseline.
2025 – Escalation & Tooling Maturity
- Updated joint advisory (Nov 13, 2025) warns of imminent threat; documents Akira_v2, BYOVD/driver abuse, new loaders (STONETOP/POORTRY), and expanded use of remote tools (Ngrok/SystemBC).
- First confirmed Nutanix AHV VM disk encryption incidents (June 2025) via campaigns that also exploited SonicWall CVE‑2024‑40766.
Current Status (as of Jan 2026)
- Highly active RaaS with sustained volume (2025 monthly spikes) and broadened hypervisor targeting (ESXi, Hyper‑V procedures, AHV disk encryption). Continue to treat as a credible, high‑impact threat to SMEs and enterprises.
Tactics & Techniques
Initial Access
- External Remote Services (VPN/RDP/SSH) — T1133 (frequent use of stolen/brute‑forced credentials; Cisco/SonicWall focus)
- Exploit Public-Facing Applications — T1190 (edge devices, backup servers incl. Veeam; SonicWall CVE‑2024‑40766)
- Valid Accounts — T1078 (compromised VPN/SSH)
Execution
- Command & Scripting Interpreter (PowerShell/CMD) — T1059 / T1059.001 / .003
- Deployment via loaders (e.g., STONETOP) / remote tools (Ngrok) — T1105 (ingress tool transfer / C2 tunneling)
Persistence & Privilege Escalation
- Create/Abuse Accounts — T1136 / T1078
- BYOVD / Abuse Elevation Control Mechanism — T1548 (POORTRY to tamper with drivers)
Defense Evasion
- Impair Defenses (disable AV/EDR, uninstall EDR) — T1562.001
- Masquerading / Living-off-the-land tools — T1036.005
Lateral Movement
- Remote Services (RDP/SMB/SSH) — T1021.001 / .002 / .004
Command & Control
- Encrypted Tunnels (Ngrok), SystemBC RAT — T1573 / T1105
Exfiltration
- Exfiltration to Cloud/FTP/SFTP (rclone, WinSCP, cloud storage) — T1567.002 / T1048
Impact
- Data Encrypted for Impact (incl. ESXi/AHV VM disk files) — T1486
Victim Experience
- Victims receive a ransom note (e.g., akira_readme.txt) with a unique ID and Tor portal links; negotiation occurs in a separate Tor chat.
- The Tor leak site uses a command-style interface (e.g., news, leaks, contact); if deadlines lapse, data is posted publicly (often in large “dumps”).
- Akira commonly claims full backup deletion and offers “test decryption”; some leaks are served via BitTorrent to increase pressure.
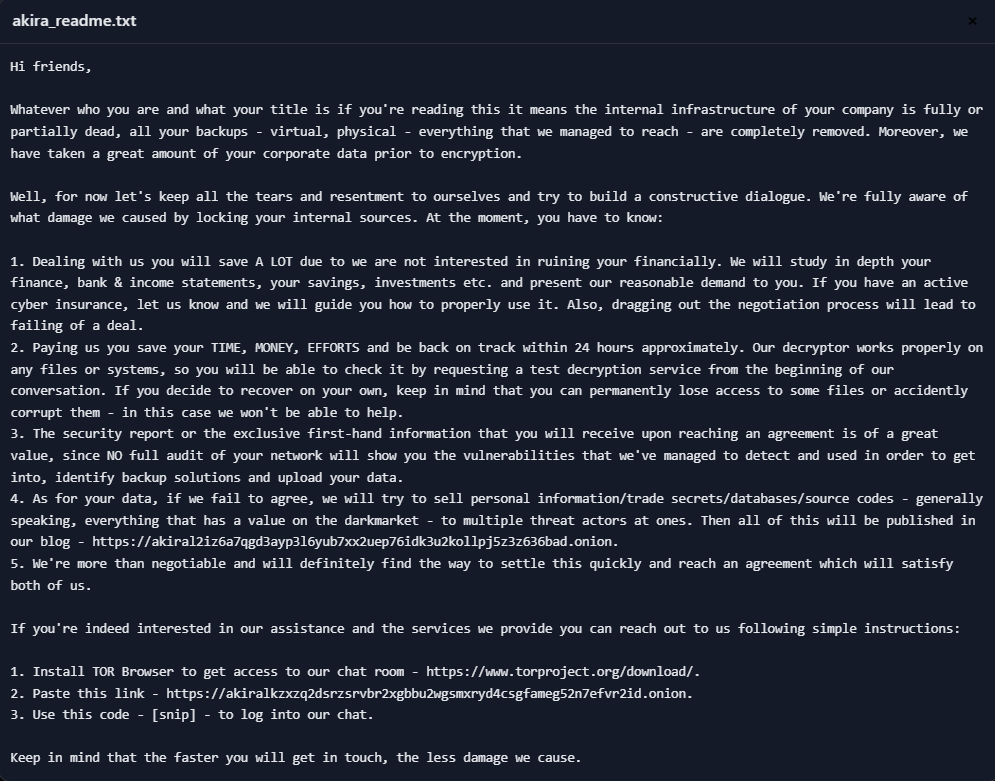
Ransom note from Akira.
Defensive Recommendations Against Akira
- Harden Remote Access: Enforce phishing‑resistant MFA on all VPN/SSH/RDP; disable single‑factor VPN access (notably Cisco/SonicWall).
- Patch Edge & Backup Systems First: Prioritize SonicWall CVE‑2024‑40766, Veeam CVE‑2023‑27532 / CVE‑2024‑40711, and similar edge/backup CVEs.
- Segment & Monitor Virtualization: Monitor ESXi/Hyper‑V/AHV admin CLIs (e.g., esxcli, vim-cmd) and watch for .qcow2 encryption attempts; restrict hypervisor management from the internet.
- Detect EDR Evasion/BYOVD: Hunt for driver tampering (POORTRY patterns), unexpected EDR service uninstall events, and Ngrok/SystemBC beacons.
- Backup Strategy: Maintain offline, immutable backups; test restoration regularly; protect Veeam/backup consoles with MFA and network isolation.
- Credential Hygiene: Monitor for unusual VPN logins; rotate and vault high‑value credentials; audit for new/rogue admin accounts
References
Cisco Talos Intelligence Group. (2024). Akira ransomware continues to evolve. https://blog.talosintelligence.com/akira-ransomware-continues-to-evolve/
Cybernews. (2025). Akira extorts $244 million, becomes major threat. https://cybernews.com/security/major-threat-akira-ransomware-crosses-250m-dollars/
Cybersecurity & Infrastructure Security Agency, Federal Bureau of Investigation, & International Partners. (2025, November 13). #StopRansomware: Akira Ransomware (Updated Advisory). https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-109a
Federal Bureau of Investigation. (2025). #StopRansomware: Akira Ransomware [PDF]. https://www.fbi.gov/file-repository/cyber-alerts/stopransomware-akira-ransomware.pdf
IBM Security X‑Force. (2025). A spotlight on Akira ransomware. https://www.ibm.com/think/x-force/spotlight-akira-ransomware-x-force
MITRE Corporation. (2025). Akira (G1024). MITRE ATT&CK. https://attack.mitre.org/groups/G1024/
Moody, R. (2025). Akira ransomware: Stats on attacks, ransoms & data breaches. Comparitech.
https://www.comparitech.com/news/akira-ransomware-stats-on-attacks-ransoms-data-breaches/
RansomLook. (2026). Akira ransomware group profile. https://www.ransomlook.io/group/akira
Toulas, B. (2023). Linux version of Akira ransomware targets VMware ESXi servers. BleepingComputer.
https://www.bleepingcomputer.com/news/security/linux-version-of-akira-ransomware-targets-vmware-esxi-servers/
Umerley, R. (2025). Akira attacks in a nutshell: Understanding and detecting the threat. Veeam.
https://www.veeam.com/blog/akira-ransomware.html
Zemah, Y. (2024). Threat assessment: Howling Scorpius (Akira ransomware). Unit 42, Palo Alto Networks.
https://unit42.paloaltonetworks.com/threat-assessment-howling-scorpius-akira-ransomware/
