Imagine locking your front door after a burglar has already walked through your house.
Now imagine doing that with your critical infrastructure.
That’s how reactive cybersecurity operates. You get alerted after something bad has already happened: a file executed, a credential was abused, or a virtual machine spun up that shouldn’t exist. By the time the alert fires, the attacker is already inside and moving laterally.
Preemptive security flips that model entirely. Instead of reacting to damage, it focuses on stopping threats before they ever get the chance to act. And in today’s environment where attacks move at machine speed, that distinction matters more than ever.
Gartner has warned that security products without preemptive capabilities will lose relevance by 2028. Not because they’re broken, but because attackers have simply moved faster than detection can keep up.
What is Preemptive Security?
Preemptive security is the ability to stop malicious activity before compromise occurs, rather than detecting and responding after the fact. Preemptive security assumes attacks will be attempted and designs controls to deny execution, interrupt behavior at runtime, and remove attacker opportunity altogether.
This concept is especially critical in environments where a single compromise can cascade across dozens or hundreds of systems, like virtualization platforms.
Why Reactive Detection Fails at the Hypervisor
Hypervisors are a major blind spot in modern security architecture because most defenses are built inside the systems they’re meant to protect like endpoints, servers, and guest operating systems. Hypervisors like VMware ESXi sits beneath those layers. So, when attackers move to the hypervisor, they’re no longer interacting with the places most traditional controls (like firewalls and EDR/XDR) can reliably see or stop.
2025: The Year Hypervisor Risk Became Impossible to Ignore
If there was any lingering doubt about whether hypervisors had become a primary attack surface, 2025 erased it. Across the year, five signals emerged:
- Attackers moved directly into the hypervisor layer, with ransomware groups abusing ESX environments at scale and nation-state actors implanting backdoors into vCenter and hypervisors themselves.
- These attacks can persist undetected for months due to lack of runtime monitoring at the hypervisor layer.
- The impact is severe, with groups like Scattered Spider inflicting over $1 billion in damages through ESX-focused attacks against organizations including Marks & Spencer and Co-op.
- The industry formally acknowledged the shift when MITRE ATT&CK v17 introduced a dedicated ESXi matrix, recognizing hypervisors as a distinct and independent attack surface.
- Attack volume and scope accelerated, with ESX ransomware incidents increasing by roughly 700% from the first half of 2025 to the second, and expanding beyond VMware with the first publicly known Nutanix AHV ransomware sample attributed to the ransomware group Akira.
Together, these developments made one thing clear: hypervisors are no longer peripheral infrastructure. They are high-value targets, and reactive detection alone is no longer sufficient to defend them.
ZeroLock®’s Preemptive Hypervisor Security Model
Most organizations still protect hypervisors the same way they always have: a mix of hardening guides, network segmentation, and monitoring tools layered together. While these controls reduce risk, they are reactive by design.
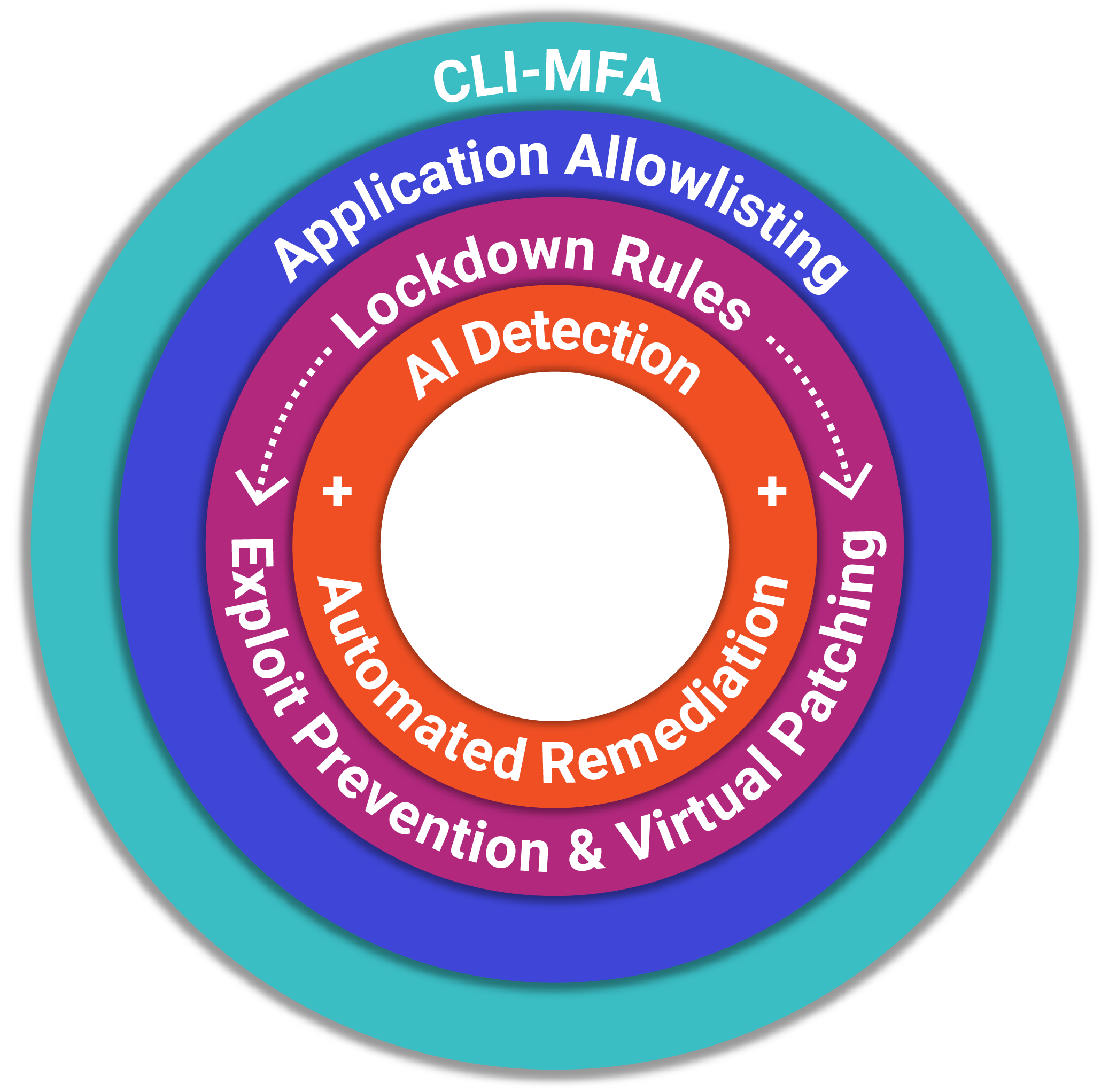
ZeroLock® takes a fundamentally different approach—one built around preemptive, hypervisor-native prevention:
- Automated preventative controls—including CLI MFA, exploit prevention, anti-tampering, and virtual patching—enforced continuously without manual effort.
- Runtime visibility and enforcement that complements segmentation by detecting tactics like lateral movement as they happen.
- Multiple prevention points, with real-time automated remediation as a last resort—not the primary defense.
- Broad attack coverage, stopping ransomware, living-off-the-land techniques, zero-days, and tampering attempts.
The result is a fundamentally different security posture, one that favors prevention over recovery.
Final Thoughts
Preemptive security is all about removing attacker opportunity. When security operates at the hypervisor level, intercepts threats in real time, and blocks execution before compromise, modern threats like Scattered Spider lose their advantage.
In a world of zero-days, sophisticated ransomware, and infrastructure-level attacks, stopping threats before they execute with preemptive hypervisor security is the only way forward.
