BLOG POSTS

From Vision to Reality: Inside the Minds of Founders with Austin Gadient
In an interview with Oliver Paull, CEO and Founder of Rec Gen, Austin Gadient, the CTO and Co-Founder of Vali Cyber, provided insights into the genesis of our company. Originating from a personal mission to rectify a critical...
Vali Cyber™ Announces Early Access to the First Ever Runtime Security Platform for ESXi
Vali Cyber, Inc., a next-generation provider of Linux cybersecurity solutions, announces that its autonomous zero-trust security platform, ZeroLock™ has been expanded to protect ESXi hypervisors, 6.7+. With no other runtime security...

ZeroLock Featured in WhiteHawk’s Top 10 Innovative Cyber Solutions of 2024
We are excited to share that ZeroLock has been recognized by WhiteHawk in their prestigious list of the Top 10 Innovative Cyber Solutions of 2024! This honor highlights our dedication to pushing the boundaries of cybersecurity, offering...

Advancing Linux and ESXi Security: An Interview with TAG Infosphere
In an enlightening interview with Edward Amoroso, CEO of TAG Infosphere, our CTO and co-founder, Austin Gadient, delves right into the heart of Linux and ESXi security, unveiling the challenges that drove the creation of ZeroLock. From...

Breaking Down ESXi
The XL Security Elephant in the Room Usage of ESXi servers is increasingly popular for organizations with a need for effective virtualization and continuous access to their Virtual Machine (VM) management. Unfortunately, this also makes...

Fortifying Finance: Navigating the Cybersecurity Landscape in the Financial Sector
The finance sector has become increasingly reliant on technology to streamline operations, provide innovative financial services, and enhance customer experiences. However, this increased digitalization has expanded the attack surface for...

Words Matter (Part 2): Redefining Accountability
Those who attempt to blur the lines regarding cybersecurity capabilities should be very afraid. On October 6th, 2021, Deputy Attorney General Lisa O. Monaco announced a new Civil Cyber-Fraud initiative, bringing a new legal tool to hold...

Words Matter (Part 1): Unveiling the Illusion of Protection
Imagine installing a new home security system that includes cameras, door alarms, window alarms, and maybe even one of those new robots that patrol your house. If someone breaks into your home, the system captures the intruder. If it aims...

TAG 2023 Security Annual: Special Reprint Edition
Revisit Vali Cyber CTO Austin Gadient’s interview with TAG Infosphere in this special reprint edition, accompanied by thought-provoking insights from TAG Infosphere CEO and Founder, Dr. Edward Amoroso, on navigating the intricate realm of...

The Urgent Need for Effective Cybersecurity in Healthcare
In this white paper, we examine the threats the healthcare sector faces, emphasizing the crucial need for enhanced cybersecurity measures.

Exploring Advanced Linux Security and Multi-Cloud Benchmarking Solution
In “Cyber and the Board,” TAG’s 4th quarter 2023 report, Vali Cyber’s CTO, Austin Gadient illustrates how ZeroLock® safeguards Linux environments by identifying and remediating malicious activity. In addition to ZeroLock's features, gain...

Breaking New Ground: Advancing Linux Security and Resilience in the Enterprise
With great power comes significant vulnerability. “Breaking New Ground: Advancing Linux Security and Resilience in the Enterprise,” a report by TAG, explores the necessity of modernizing our approach to Linux security and how Vali Cyber...

Ransomware in the Education Sector
Over recent years, unrelenting cyber-attacks bombard the education sector. As a result of the pandemic, the shift to remote learning environments created an attractive target out of organizations within higher education. The education...
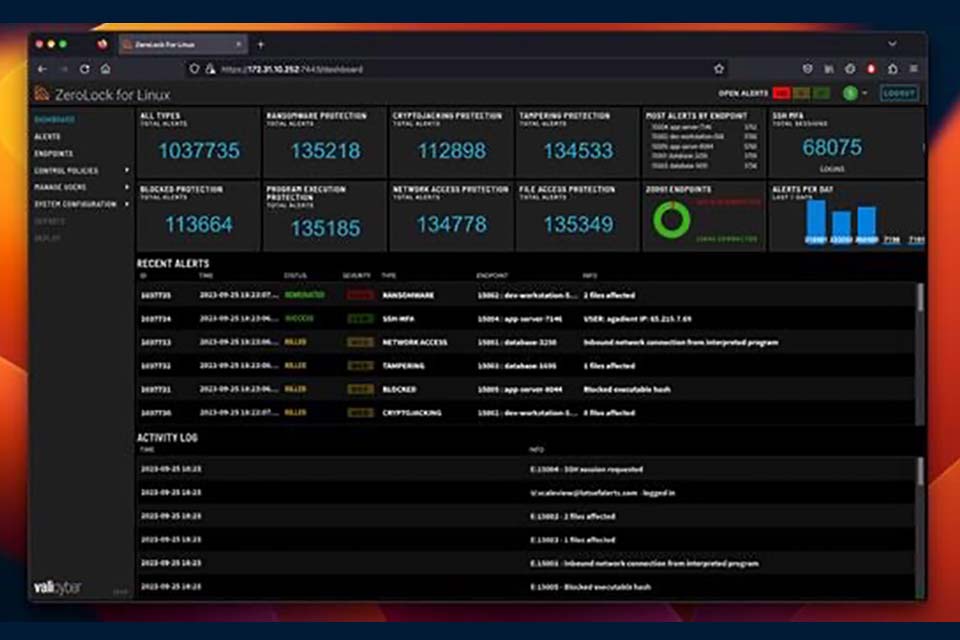
Vali Cyber® Secures $15M in Seed Funding to Revolutionize Linux Cybersecurity
Vali Cyber, Inc., a next-generation provider of Linux cybersecurity solutions, announces the successful completion of its seed funding round, raising USD 15 million. The funding round was co-led by Grotech Ventures and the 412 Venture...

Unraveling the Jargon: Understanding Endpoint Security and Beyond
Back in 2013, a game-changing technology called EDR burst onto the scene, revolutionizing our approach to safeguarding our digital domains. This “new” tech sought to supercharge digital forensics on endpoint systems, eliminating the need...

AI Kills Hash Based Detections
Whether it is ChatGPT, GPT4, Bard, or any of the other AI systems competing for public attention, these systems represent a significant leap forward in Malware as a Service (MaaS) capabilities. While it is true there are supposed to be...
