YOUR LINUX ENVIRONMENT IS PRIVATE FOR A REASON. PROTECT IT.
GET UP AND RUNNING FAST WITH ONE-LINE DEPLOYMENT.
- Public, Private, or Hybrid Cloud (Bare Metal/VMs, Containers, Kubernetes)
- On-premises / Private Data Center
- Embedded Systems and Controllers
- Air-gapped Environments
ENSURE UPTIME WITH AI AND AUTOMATED FILE ROLLBACK.
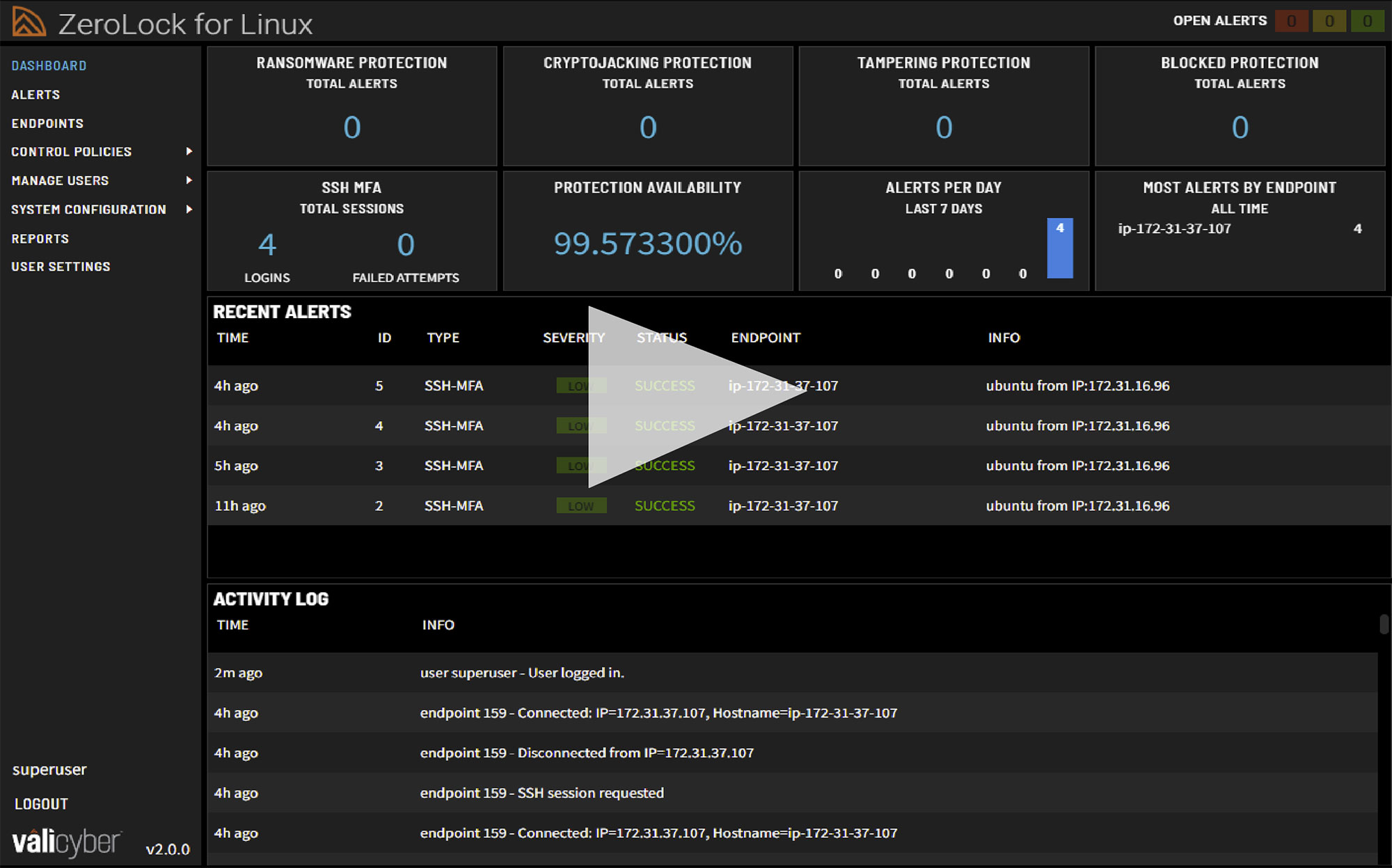
ZeroLock’s patent-pending AI/ML-based behavioral capability detects malware by the actions it performs, not scanning for easily defeated file hashes. Our proprietary algorithms detect and stop traditional and fileless attacks in real-time with >98% efficacy and offer the ability to automatically remediate file damage with no user intervention required—helping you to ensure zero downtime.
- Ransomware Protection
- Wiperware Protection
- Cryptojacking Protection
- Automated Attacker Persistence Removal
- Real-time Threat Remediation
- Automated file rollback
- Fully Automated Process Tree Creation
Read the report from TAG Cyber about advancing Linux Security and Resilience in the Enterprise.
PREVENT ATTACKS WITH REAL-TIME VIRTUAL PATCHING.
ZeroLock goes beyond traditional mandatory access control capabilities. In contrast to SELinux and AppArmor, ZeroLock offers easily configured and universally applied rules and policies that can be deployed across all your Linux and cloud environments from a single console. Examples of our control capabilities include:
- SSH Multifactor Authentication (MFA)
- Process Behavior Controls
- Network Access Controls
- File Access Controls
- Canary Files
- Tamper Protection
API-FIRST ARCHITECTURE FOR SIEM/SOAR INTEGRATIONS.
For teams that have existing platforms in place that they don’t want to disrupt—for their Windows endpoints for instance—ZeroLock has an API-first architecture with SIEM/SOAR integration capabilities to work into your environment, so you can have the best Linux security without sacrificing ease of management.
24-7 SUPPORT, EVERY STEP OF THE WAY.
TECH SPECS
ZeroLock® Endpoint Agent Requirements
OS
Linux, kernel v3.5 or higher. Distribution agnostic.
Processor
x86-64, ARM-64 (coming soon)
Memory
50MB
Disk Space
100MB
Kernel Mods.
No kernel modification or modules required
VM/Container Support
ZeroLock runs on Bare Metal, VMs, and containers—including public / private / hybrid cloud instances
Installation Methods
- Curl-based command installer
- Wget-based command installer
- Tar.gz file-based installer
- Bash script self-extracting file-based installer
- Deploy via containers (e.g. Docker)
- Deploy via orchestrated containers (e.g. Kubernetes or OpenShift)
ZeroLock® Server Requirements
RAM
8GB
Disk Space
100GB (dependent on number of endpoints and data retention duration)
CPU Cores
4 or more recommended
Installation Reqs.
Latest version of Docker installed.
CONTACT US
"*" indicates required fields