Aliases
- ShinyCorp
- UNC6240
- Sometimes referenced as “Scattered Lapsus$ Hunters” in recent collaborations.
Get Threat Intel and Security Updates Delivered to Your Inbox.
Profiling
Threat Actor Type: Financially motivated data-theft and extortion collective (not encryption-focused ransomware). Primary tradecraft since 2024–2025: social-engineering (vishing) to obtain access to SaaS/cloud apps followed by mass data exfiltration and extortion.
Communications & Infrastructure:
- Group members are active in Telegram and English-speaking cybercrime forums like BreachForums, OGUsers and DarkForums.
- Leak/claim sites used to pressure victims; 2025 extortion sites listed dozens of Fortune 500 firms.
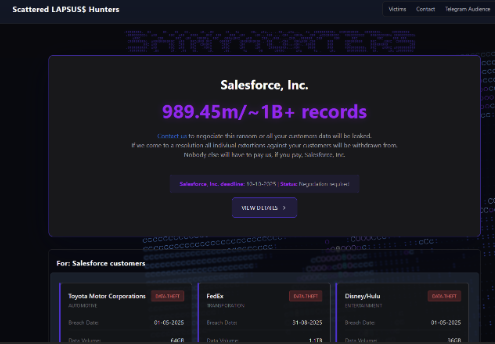
Figure 1: ShinyHunters Salesforce leaks.
Expertise
- SaaS/OAuth abuse (Salesforce “Data Loader” lookalikes; OAuth device-code flow).
- Classic credential theft/reuse; session/token abuse; cloud discovery; automated bulk export.
Motivations
- Primary: Profit via sale/leak/auction of large customer datasets; extortion without encryption.
- “Mr. Raoult’s motive was pure greed. He sold hacked data. He stole people’s cryptocurrency. He even sold his hacking tools so that he could profit while other hackers attacked additional victims.” – Criminal Chief Sarah Vogel
- Secondary: Reputation building in the cybercriminal ecosystem, forum administration, and sale of stolen data.
Timeline & Victimology
2020–2023 – Database Breach Spree
- ShinyHunters emerges and sells/leaks large user databases (e.g., Tokopedia, Wattpad; multiple 2020 breaches).
- Claims around Microsoft GitHub/private repos and a 2021 AT&T dataset appear during this period (AT&T initially denied origin; later litigation/coverage ties data back to earlier exposure).
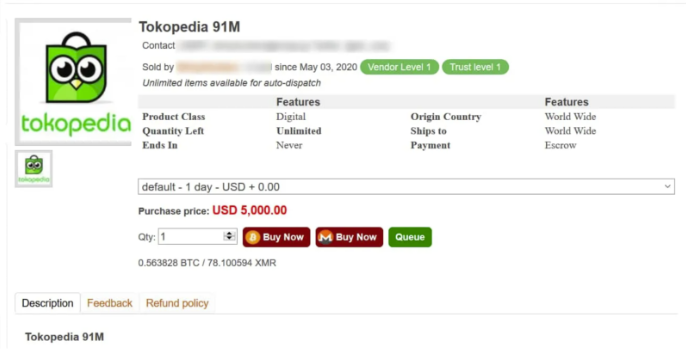
Figure 2: Sale of data allegedly belonging to Tokopedia.
January 2024 – Sentencing (Related Member)
- French national Sébastien Raoult (linked to ShinyHunters activity) is sentenced to 3 years in the U.S., $5M+ restitution.
May–June 2024 – Ticketmaster & Santander Data For Sale
- ShinyHunters advertises data tied to Ticketmaster (~500–560M users claimed) and Santander (millions of customers/staff).
June 2025 – Salesforce Campaign (Vishing + OAuth Abuse)
- Google Threat Intelligence details UNC6040 using voice phishing to get victims to approve a malicious “Data Loader” connected app, enabling mass Salesforce exfiltration and extortion.
- Reuters corroborates targeting across Europe/Americas; social engineering at play.
- Public victim lists in industry reporting include Google, Adidas, LVMH brands (Louis Vuitton, Tiffany & Co.), Pandora, Qantas, Air France–KLM, Allianz Life, Cisco and others.
June 23–25, 2025 – French Arrests (BreachForums Core)
- French authorities arrest four alleged BreachForums/ShinyHunters administrators; operations continue despite arrests.
August–September 2025 – Collaboration/Overlap Assessments + ESXi Targeting
- Multiple researchers describe operational overlap with Scattered Spider (UNC3944) and related personas; reporting cites AI-enabled vishing and supply-chain angles in some intrusions.
- Assessments emerge linking a new ransomware family — shinysp1d3r — to the ShinyHunters ecosystem. Analysts report that shinysp1d3r is designed to target VMware ESXi hosts and datastores (enumerating VMs, disabling snapshots, and encrypting VMDK files), and that an affiliate control panel provides datastore selection and throttling options.
Figure 3: ShinyHunters breach message.
October 2025 – Leak Site & Ongoing Extortion
- A public leak site threatens to publish data from ~39 companies tied to the Salesforce wave; media documents mass record counts and continued extortion.
Tactics & Techniques
Initial Access
- Exploit Public-Facing Application — T1190
- Phishing / Spearphishing (voice/vishing) — T1566.004
- Valid Accounts — T1078 (T1078.004 for Cloud Accounts)
- Trusted Relationship — T1199
Execution
- Command and Scripting Interpreter — T1059 (T1059.006 for Python)
- System Services: Service Execution — T1569.002 (where applicable for server-side execution)
Persistence & Privilege Escalation
- Account Manipulation / Additional Cloud Credentials — T1098 (T1098.001)
- Abuse Elevation Control Mechanism — T1548
Defense Evasion
- Impair Defenses: Disable/Modify Tools — T1562.001
- Indicator Removal: Clear Event Logs — T1070.001
- Snapshot / VM state manipulation (hypervisor defense evasion) — (behavior analogous to defense-evasion techniques)
Credential Access
- Steal Application Access Token (OAuth tokens) — T1528
- Multi-Factor Authentication Request Generation (MFA-approval social engineering) — T1621
Lateral Movement
- Remote Services (Cloud console / APIs) — T1021. (cloud-native lateral movement via admin consoles and API calls)
Collection & Exfiltration
- Automated Collection / Bulk Export — T1119
- Exfiltration to Cloud Storage / Web Services — T1567.002
Impact
- Data Encrypted for Impact (includes VMware/ESXi hypervisor-level encryption observed/assessed) — T1486
Defensive Recommendations Against ShinyHunters
- Enforce strict MFA and verify all IT-support calls before approving resets.
- Audit and restrict OAuth apps in Salesforce and other SaaS platforms; revoke unverified or high-scope tokens.
- Monitor for unusual activity (mass exports, new connected apps, or API spikes).
- Harden ESXi hosts: disable direct root/SSH, patch promptly, watch for snapshot deletions or datastore encryption.
- Maintain offline, immutable backups of VMs and SaaS data.
References
Baran, G. (2025). How ShinyHunters Breached Google, Adidas, Louis Vuitton and More in Ongoing Salesforce Attack Campaign. In Cyber Security News. https://cybersecuritynews.com/shinyhunters-breaches/
Dark Web Profile: ShinyHunters. (2024). In SOCRadar® Cyber Intelligence Inc. https://socradar.io/dark-web-profile-shinyhunters/
Dutta, T. S. (2025). New ‘shinysp1d3r’ Ransomware-as-a-service in Active Development to Encrypt VMware ESXi Environments. In Cyber Security News. https://cybersecuritynews.com/new-shinysp1d3r-ransomware-as-a-service-in-active-development/
Live Nation reveals data breach at its Ticketmaster subsidiary. (2024). In AP News. https://apnews.com/article/ticketmaster-live-nation-data-breach-a756d803c686e07f3b73444b3ca42c74
Poireault, K. (2025). French Authorities Arrest Four Hackers Tied to Notorious BreachForums. Infosecurity Magazine. https://www.infosecurity-magazine.com/news/french-authorities-arrest-four/
R, A. (2025). ShinyHunters. In Threat Actor – CyberMaterial. https://cybermaterial.com/shinyhunters-threat-actor/
Salesforce-Related Data Breach Affecting Multiple Companies. (2025). In SOCRadar® Cyber Intelligence Inc. https://socradar.io/salesforce-data-breach-affecting-multiple-companies/
ShinyHunters Calling: Financially Motivated Data Extortion Group Targeting Enterprise Cloud Applications. (n.d.). In blog.eclecticiq.com. Retrieved October 16, 2025, from https://blog.eclecticiq.com/shinyhunters-calling-financially-motivated-data-extortion-group-targeting-enterprise-cloud-applications
ShinyHunters Threat Campaign and Activity Update. In Obrela. https://www.obrela.com/advisory/shinyhunters-threat-campaign-and-activity-update/
The Cost of a Call: From Voice Phishing to Data Extortion. (n.d.). In Google Cloud Blog. Retrieved October 16, 2025, from https://cloud.google.com/blog/topics/threat-intelligence/voice-phishing-data-extortion
Ticketmaster’s Encore: How “ShinyHunters” Hacked the Show. (n.d.). In Skyhigh Security. Retrieved October 16, 2025, from https://www.skyhighsecurity.com/about/resources/intelligence-digest/ticketmasters-encore-how-shinyhunters-hacked-the-show.html
Vicens, A. J., & Vicens, A. J. (2025). Hackers abuse modified Salesforce app to steal data, extort companies, Google says. In Reuters. https://www.reuters.com/sustainability/boards-policy-regulation/hackers-abuse-modified-salesforce-app-steal-data-extort-companies-google-says-2025-06-04/?
Western District of Washington. (2024). In United States Department of Justice. https://www.justice.gov/usao-wdwa/pr/member-notorious-international-hacking-crew-sentenced-prison?
Who are ShinyHunters? The hacking group that targeted Google. (2025). In The Independent. https://www.independent.co.uk/tech/google-data-breach-shinyhunters-cyber-attack-b2821097.html
Wood, Z. (2024). Santander customers’ private data put up for sale for $2m by hackers. In The Guardian. https://www.theguardian.com/business/article/2024/may/31/santander-customers-private-data-sale-hackers-shinyhunters-bank-credit-card-numbers
