When attackers reach the virtualization layer, they gain control of the systems that run the entire business. This unfortunate scenario has occurred exponentially in recent years as threat actors discover that the hypervisor remains the least monitored, least protected, and most consequential point of failure in the modern technology stack.
Hypervisor Risk In 2026 Cybersecurity Forecasts#
The efficiency of virtualization becomes dangerous when attackers breach the hypervisor:
- One compromise can freeze entire business functions at once.
- Recovery is harder and slower due to the highly interconnected nature of virtualized infrastructure.
- Backups are often compromised because attackers maintain persistence for months before striking—so every backup in that window is infected.
Google’s 2026 Cybersecurity Forecast
warns that adversaries will continue targeting virtualization because it offers maximum disruption with minimal effort. With ransomware families targeting virtualization increasing 5x since 2022, Mandiant emphasizes that reducing this risk requires “establishing capabilities that protect the infrastructure layer itself.”
Failure to secure the hypervisor heightens financial, operational, and regulatory risk to a degree that traditional defenses can no longer mitigate.
Virtualization Breaches Over the Years#
By looking at recent virtualization attacks, we can better understand the operational consequences of a breach at this layer.
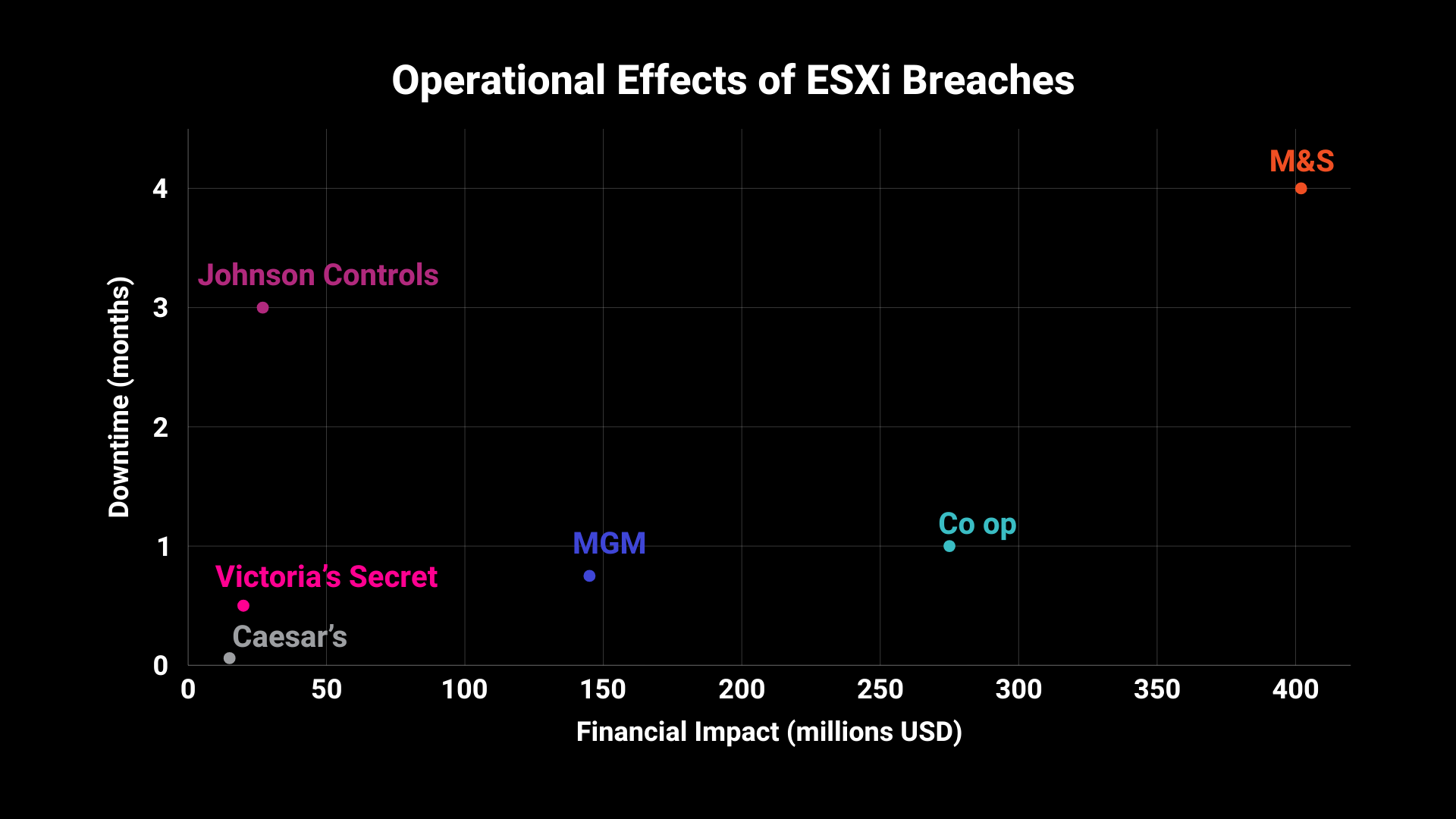
Visualization of recent ESXi breaches’ downtime and financial impact.
Retail#
Marks & Spencer (2025)#
In April 2025, UK retailer Marks & Spencer suffered a ransomware attack that crippled its VMware ESXi environment, exposed the personal data of up to 10 million customers, and shut down core systems for six weeks.
- 4 months until full-service restoration
- $402 million in lost sales
- $1+ billion wiped from market value
Co-op (2025)#
In the same month, Co-op also experienced a hypervisor attack that forced IT systems offline and resulted in data theft of 6.5 million members.
Hospitality & Entertainment#
MGM (2023)#
Attackers encrypted approximately 100 of MGM Resorts’ ESXi hypervisors, exfiltrating 6 TB of sensitive customer data, taking critical hotel, casino, and guest-facing systems offline across multiple properties.
- 10 days of operational disruption
- $100 million in lost profits
- $10 million in response costs
- $45 million class action lawsuit
Building Automation & Critical Infrastructure#
Johnson Controls (2023)#
Federal contractor and global automation leader Johnson Controls was hit by Dark Angels ransomware, breaching its ESXi environment. Attackers maintained prolonged access and stole 27 TB of highly sensitive data, including Social Security numbers, financial account details, building floor plans, and physical security configurations, impacting 76+ million households and 7 million businesses.
- 3 months of downtime, 8 months of undetected access
- $27 million in incident response and remediation costs
- ~22 months before customer notification of breach
The New Risk & Compliance Landscape: Why C-Suites are Exposed#
On top of disrupting operations, cyberattacks at the virtualization layer create governance and disclosure problems for executive leadership.
SEC Cyber Disclosure Rules#
In the US, the SEC’s cybersecurity disclosure rules now require public companies to:
- Disclose material cybersecurity incidents within four business days
- Detail cyber risk governance at the board level
If your organization can’t answer how the virtualization layer is secured, you’re exposed to potential disclosure and governance failures.
Fiduciary Duty and Oversight#
Cyber risk is now a mission-critical legal risk. Boards ignoring hypervisor security face oversight liability—especially in industries built on virtualized infrastructure. If leadership isn’t actively overseeing that risk, they’re increasingly vulnerable to claims that the board failed in its duty of oversight.
Class Actions and Data-Privacy Liability#
In the first half of 2025, US organizations paid $155M in class action lawsuits related to data breaches, with inadequate security measures leading to 50% of the filings.
- Most ESXi attacks involve data exfiltration in addition to downtime, posing extreme risk of lawsuits and regulatory scrutiny.
- MGM, Marks & Spencer, Johnson Controls all faced legal fallout after hypervisor breaches.
As Panaseer CEO Jonathan Gill put it, “While people can be understanding when a company falls victim to an attack, they’re far less forgiving when it looks like the organization failed in its duty of care around data.”
Hypervisor gaps are increasingly viewed as governance failures. The best defense? Demonstrate due diligence with preemptive security.
Fill the Hypervisor Security Gap with ZeroLock#
Every executive prioritizes three outcomes: keep the business running, protect revenue, and avoid preventable losses. Hypervisor breaches threaten all three.
Vali Cyber’s ZeroLock® prevents hypervisor risk before it materializes:
- Risk Reduction: Reduce ransomware exposure by up to 99.9%, protecting revenue and preventing costly outages.
- Compliance Assurance: Stay audit-ready and avoid penalties by meeting key regulatory and industry standards like SOC 2, NIST 800-171, and NIST CSF 2.0.
- Operational ROI: Maintain business continuity with a fast, low-impact deployment that minimizes disruption and reduces recovery costs.
- Reputation Protection: Demonstrate proactive risk management to boards, investors, and regulators.
ZeroLock prevents the kind of hypervisor-level damage seen in recent attacks for a fraction of the cost, typically under 1% of the losses these breaches create.
See what hypervisor security looks like in your environment.
