Vali Cyber Threat Intelligence Report
Ransomware is one of the most severe threats in cybersecurity today. After an intruder gains access to the target network or device, they then use malware called “ransomware” to systematically encrypt some or all the data they find. The attacker will usually attempt to target the most valuable or critical data available. Modern encryption standards will render the targeted data virtually unrecoverable without the attacker’s cooperation if correctly applied. The attacker will then hold this data for ransom, leaving a message on the victimized devices explaining methods the target organization can pay the attacker to recover the encrypted data.
Many organizations end up paying the ransom to recover their files. It is worth noting that in some cases, even the attacker cannot recover the data because their ransomware was not written in a way that allows recovery. In this scenario, the victim may pay the ransom and still be left without access to their data. Such instances are more the exception than the rule, but they illustrate the acute need for mitigation and prevention.
No network is impervious to intrusion. Any organization with a network or cloud presence is at risk of profound loss to ransomware actors.
Attack Testing
We tested the speed at which some of the most prevalent Linux ransomware strains encrypt data. The tested samples were found in the real-world networks of businesses, educational institutions, health care facilities, and even domestic users. Each ransomware sample tested was a Linux variant and was run inside a docker container on Ubuntu 20.04. The host machine had 32 GB of memory and an Intel i9-11900H processor running 2.50GHz. See Figure 1 for an illustration of the test.
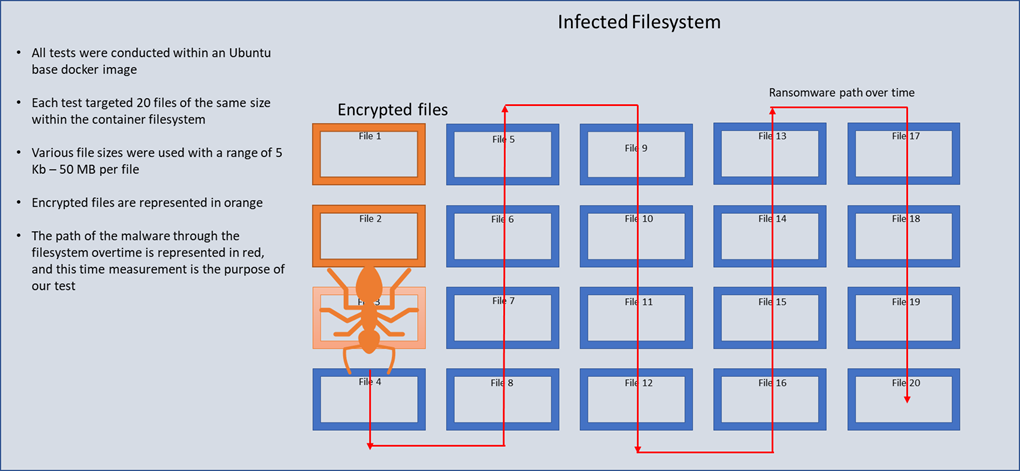
Figure 1 Ransomware Testing Visualization
| Name | 100 KB (20 * 5KB) |
20 MB (20 * 1MB) |
100 MB (20 * 5MB) |
1 GB (20 * 50MB) |
| DarkRadiation | 0.077s | 0.086s | 0.087s | 0.102s |
| Defray777 | 0.002s | 0.005s | 0.006s | 0.011s |
| QnapCrypt | 0.031s | 0.036s | 0.046s | 0.050s |
| Darkside | 0.019s | 0.022s | 0.058s | 0.171s |
| Lilocked | 0.004s | 0.052s | 0.099s | 0.399s |
| Tycoon | 0.048s | 0.063s | 0.135s | 0.292s |
| TellYouThePass | 0.129s | 0.131s | 0.144s | 0.150s |
| Erebus | 0.0045s | 0.095s | 0.138s | 0.156s |
| EXX | 0.019s | 0.019s | 0.022s | 0.086s |
| REvil | 0.049s | 0.069s | 0.085s | 0.129s |
These encryption times are somewhat fast. The different choices in the encryption algorithm and file access strategy used by the malware account for variations in time. Additionally, the mode of delivery for the malware impacts its timing. Some of the malware samples tested are scripts, while others are compiled executables.
Most samples tested could encrypt over a gigabyte of data in under 15 seconds. One gigabyte could be the entirety of an organization’s website, spanning hundreds of web pages. It could also be hundreds of thousands of text-based messages in email or Instant Messaging. A gigabyte is more than their entire code repository for many smaller organizations. In far less than 15 seconds, all that data and associated labor hours could be lost forever.
Ransomware is a potent threat. Usually, it takes far longer than 15 seconds for a system administrator to become aware of malware in their network. After the admin learns that the ransomware exists, every second is crucial. Human response time is woefully inadequate for fundamental defensive measures across large enterprises regarding ransomware.
How to protect yourself
A robust ransomware prevention and response plan is necessary to prevent the worst of ransomware attacks. Hardening your network by conducting regular vulnerability scans and penetration tests is one crucial aspect of any such program. A sound intrusion detection/prevention system and well-configured firewall alongside dedicated information security personnel will prevent attacks at your network perimeter. Even with the best perimeter defenses, there is a chance an intruder may gain unauthorized access to your network.
When the worst happens, it is essential to have internal defenses. One of the best solutions to the ransomware problem in the Linux environment is Vali Cyber’s ZeroLock software. ZeroLock runs with extremely low overhead and protects against all the ransomware variants tested above. It not only detects and stops ransomware but restores any files altered or removed while the ransomware is running. This results in zero data loss and speedy remediation.
When ZeroLock was tested against the same ransomware samples we used above, it was able to stop each in its tracks, restore all encrypted files, and keep the targeted system running smoothly throughout. Below is a table and illustration showing the time it took ZeroLock to stop ransomware after beginning execution in the same testing environment used above.
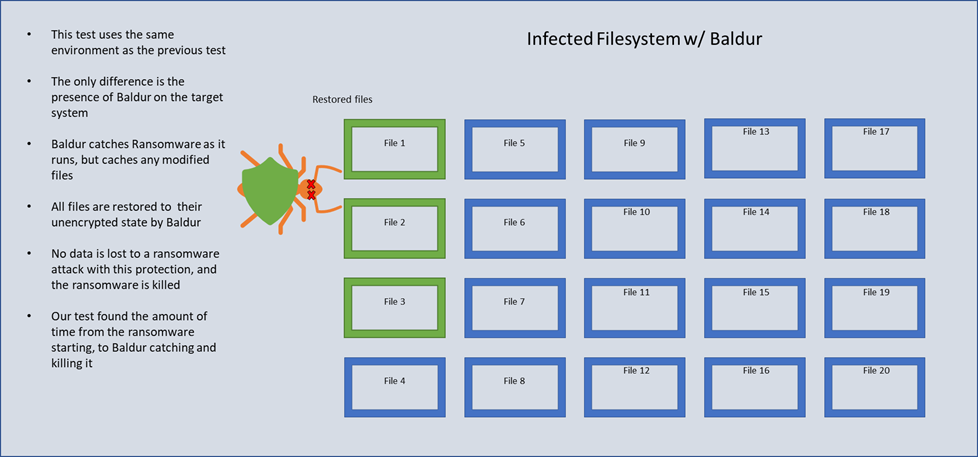
Figure 2 Ransomware Execution on a Protected System
| Name | 100 KB (20 * 5KB) |
20 MB (20 * 1MB) |
100 MB (20 * 5MB) |
1 GB (20 * 50MB) |
| DarkRadiation | 0.077s | 0.086s | 0.087s | 0.102s |
| Defray777 | 0.002s | 0.005s | 0.006s | 0.011s |
| QnapCrypt | 0.031s | 0.036s | 0.046s | 0.050s |
| Darkside | 0.019s | 0.022s | 0.058s | 0.171s |
| Lilocked | 0.004s | 0.052s | 0.099s | 0.399s |
| Tycoon | 0.048s | 0.063s | 0.135s | 0.292s |
| TellYouThePass | 0.129s | 0.131s | 0.144s | 0.150s |
| Erebus | 0.0045s | 0.095s | 0.138s | 0.156s |
| EXX | 0.019s | 0.019s | 0.022s | 0.086s |
| REvil | 0.049s | 0.069s | 0.085s | 0.129s |
Each one of the samples was stopped in less than 0.4 seconds. For ransomware encrypting smaller file sizes, these times were significantly less. All of them were detected quickly and without any data loss. ZeroLock identified the malignant process and was able to restore all affected files to a pre-ransomware state. These results are crucial for proper protection from ransomware threats. ZeroLock is a highly effective last line of defense in the critical post-intrusion moments when every second counts.
ZeroLock’s advanced behavioral algorithmic detection leverages AI and formal methods to stop ransomware. A behavioral approach ensures ransomware is stopped no matter what form it comes. Fileless attacks, file-based attacks, python scripts, C programs, GoLang programs, and any other instantiation of ransomware are detected with equally high efficacy. The obfuscation techniques attackers use to hide files fail when used against ZeroLock’s defenses. Thus, ZeroLock’s detection is robust against the ever-changing threat landscape.
Conclusion
As cyber threats continue to evolve, it is vital that defensive software changes to meet new challenges. ZeroLock uses cutting-edge technology to detect novel ransomware without human assistance. This means that it is finely tuned to identify zero-day strains of ransomware and protect users from paying the price of being the first victim. Without burdensome computational overhead on the protected system, it leaves power for getting work done.
For more information, contact [email protected].
