Imagine a financial institution where all virtual machines—responsible for everything from customer transactions to trade executions—suddenly go dark. As a result, operations freeze, data is locked, and millions are at stake. This is not hypothetical. Ransomware operators increasingly target hypervisors, the backbone of virtualized infrastructure. With over 65% of financial organizations reporting ransomware incidents in 2024, the need for robust hypervisor security has never been more critical.
Get Threat Intel and Security Updates Delivered to Your Inbox.
Why Hypervisors Are a Prime Target
Financial institutions rely on virtualization to manage large data loads efficiently. At the core of this setup are hypervisors, which enable institutions to consolidate servers, optimize resource use, and maintain seamless service delivery. But with this reliance on virtualization comes a new vulnerability: hypervisors have become prime targets for ransomware attacks. A successful breach of a hypervisor can set off a chain reaction of disruptions, compromising critical services and risking financial losses that could devastate any institution.
Ransomware Attacks on Hypervisors are Surging
Ransomware groups have adapted their tactics, increasingly targeting hypervisors to maximize the impact of their attacks. Microsoft reports that threat actors are actively focusing on ESXi hypervisors for their ability to mass-encrypt all hosted virtual machines in a single strike. Alarmingly, attacks on ESXi hypervisors have more than doubled over the past three years.
Common attack vectors include:
- Outdated or unpatched hypervisors
- Compromised administrative credentials
- Social engineering and phishing campaigns
Once inside, attackers deploy ransomware to lock down critical virtual machines, forcing institutions to choose between paying hefty ransoms or enduring prolonged operational outages. Despite the rising threat and cybersecurity being a top concern in 2025, fewer than 50% of organizations have a formal ransomware response plan, leaving them dangerously exposed.
Attackers are adapting their methods, targeting hypervisors like VMware ESXi with customized ransomware variants such as ESXiArgs. Some groups have even developed tools like “MrAgent” to automate attacks on ESXi hypervisors, enabling faster, more coordinated ransomware campaigns. For financial institutions reliant on virtualized infrastructure, this trend poses a significant and immediate risk that demands a robust and proactive response.
RansomHub, a fast-rising RaaS group that emerged in early 2024, has already claimed 38 financial-sector victims within April 2024 and April 2025. Known for phishing and exploiting unpatched systems, they’re part of a growing wave of attackers zeroing in on virtualized infrastructure.
The latest MITRE ATT&CK v17 framework reinforces the urgency of this threat, introducing new TTPs specifically designed to exploit hypervisors like VMware ESXi. It is evident that without proactive defenses like virtual patching, institutions remain increasingly vulnerable to these emerging attack paths.
Why Financial Institutions Are Top Targets
Banks, insurance companies, and investment firms manage highly sensitive data—from customer financial records to proprietary trading algorithms. For ransomware groups, this information is a goldmine, and even brief disruptions can cause catastrophic damage.
-
$2.58 million: Average ransomware recovery cost for financial institutions in 2024
-
Thousands of transactions disrupted per minute of downtime
-
Loss of customer trust and potential regulatory penalties
Case in Point: Patelco Credit Union (July 2024)
In July 2024, a ransomware attack—triggered by a phishing email—struck Patelco Credit Union, a California-based nonprofit financial cooperative. The attack forced Patelco to proactively shut down many of its core banking systems, leaving over 450,000 members unable to access essential services, including online banking, mobile app functions, and wire transfers. Debit and credit card transactions were only partially functional, and members faced ongoing ATM outages. While Patelco worked with cybersecurity experts to restore systems safely, customers encountered significant delays and uncertainty in accessing their funds and accounts.
How to Defend Against Hypervisor Ransomware
Protecting against these rising threats requires a multi-layered approach to hypervisor security, beginning with preventive measures.
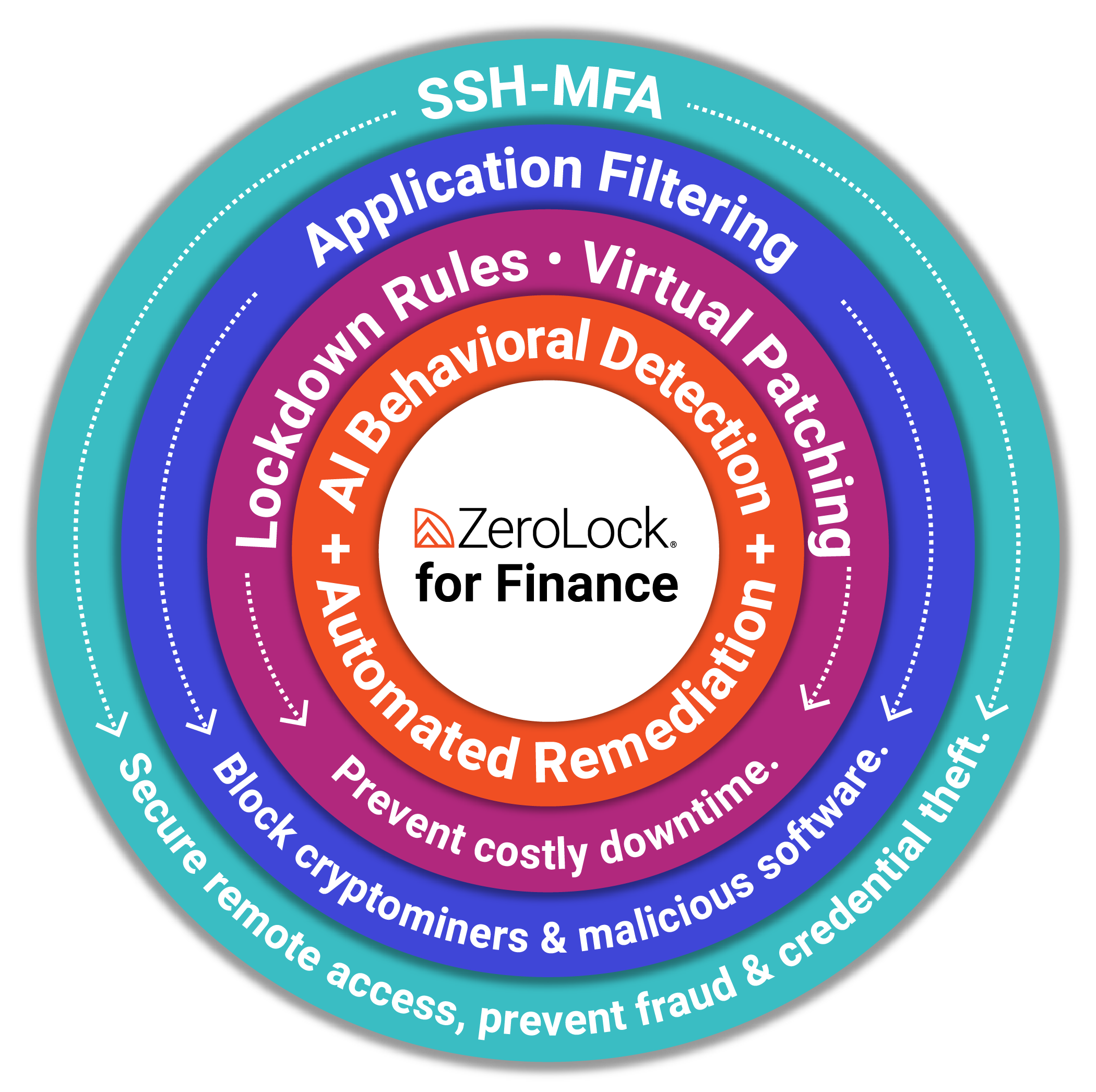
ZeroLock was engineered with hypervisor security in mind, providing additional layers of protection with features:
- AI Detection to proactively identify and block ransomware activity.
- Application Filtering to prevent unauthorized or malicious applications from executing.
- Virtual Patching to mitigate vulnerabilities without requiring immediate system downtime.
- Automated Rollback to quickly restore systems to a safe, pre-attack state.
A ransomware attack targeting hypervisors is a formidable threat with the potential for widespread disruption. Taking proactive steps to secure virtualized environments is more than a defensive strategy; it’s a critical investment in the stability and trustworthiness that customers rely on.
