Securing WordPress with ZeroLock® for Linux®
WordPress is one of the most popular content management systems in the world, enabling non-technical users to create beautiful, effective websites. Powering millions of websites, it’s a frequent target of hackers. While most are powered by professional hosting services who provide security, many sites choose to manage their own servers—and that can be challenging to do securely. Default settings for WordPress are insecure, and inexperienced users commonly misconfigure their sites with security vulnerabilities. The troubling truth of today’s cyber environment is that new vulnerabilities are being found frequently, and even what are considered secure sites get breached with novel exploits.
In this whitepaper we show how ZeroLock® for Linux®, a new cybersecurity solution from Vali Cyber, can add a strong layer of protection for WordPress sites. ZeroLock is installed onto the Linux server hosting WordPress and can protect all sites running on that server. We present a couple of ways an attacker tries to infect a vulnerable website with malware, and how ZeroLock thwarts the attacker’s best efforts.
In this scenario, our hacker has a simple goal: to launch a cryptominer on computing resources that are not their own and reap the profits while someone else pays the electricity bill. Web hosting providers using WordPress are an ideal target for this attack because finding vulnerabilities in WordPress websites is simple. Furthermore, many WordPress websites do not take the time to monitor their servers, allowing a cryptominer to go undetected for days, weeks, or even months.
Phase 1 Malicious Plugin Upload:
In the first phase of our attack, the hacker attempts to gain access to the WordPress website through the wp- login.php console page. Unfortunately, the user that set up their website did not select a strong password, and the attacker was able to gain access using a simple brute force attack.
From this stage, the attacker needs to upload a malicious plugin that gives them a webshell on the host system. They opt for the popular “Wordpress-webshell-plugin”. This plugin will allow the hacker to run arbitrary commands on the operating system running WordPress.
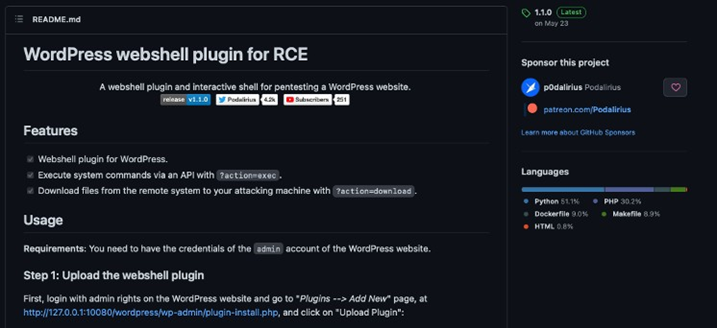
The attacker attempts to upload the plugin. Thankfully, the server is protected by ZeroLock, and the attempt to upload a malicious plugin is detected immediately.
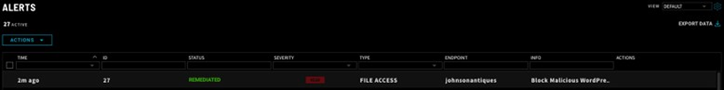
Not only does ZeroLock detect the attempt to upload a malicious WordPress plugin, ZeroLock deletes the files that were attempted to be uploaded, leaving the WordPress website clean and free of malicious PHP files.
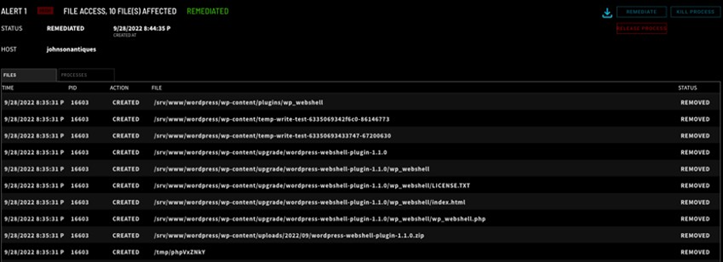
Phase 2 Webshell Interaction:
For Phase 2, we disabled ZeroLock’s plugin protection to allow the attacker to continue their efforts. In Phase 2, the hacker successfully uploaded their malicious webshell plugin. They will now attempt to leverage this malicious plugin to start a webshell.
The attacker leverages the WordPress-webshell- plugin’s console.py tool to run commands. console.py establishes a network connection to the WordPress-webshell-plugin. This terminal session allows the attacker to run arbitrary commands on the target system.
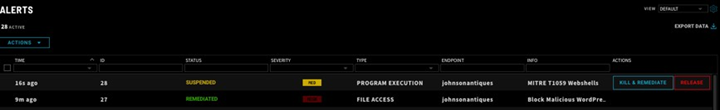
Not so fast! ZeroLock detects webshells too! A new alert is opened in the ZeroLock console. The “INFO” column of the alert mentions MITRE technique T1059. In addition to webshells,
![]()
ZeroLock contains detection capabilities for numerous techniques within the MITRE framework.
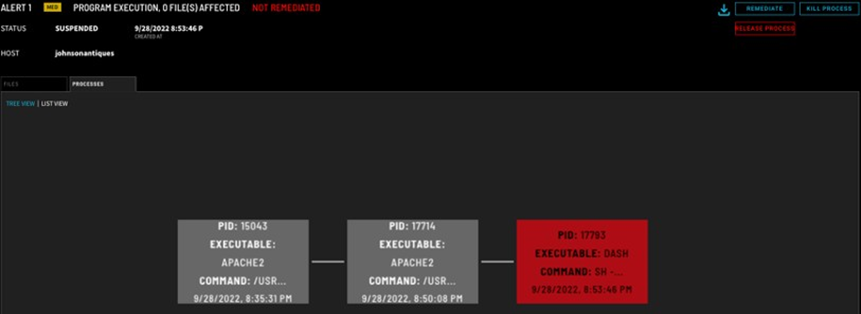
ZeroLock provides detailed indicators of compromise that are useful for threat hunting after an attack is detected. One such piece of data is a process tree of all the programs involved in the attack. The process tree contains details about the parent-child relationships of processes involved in an attack. As you can see, this attack leveraged Apache to launch the program Dash, our webshell.
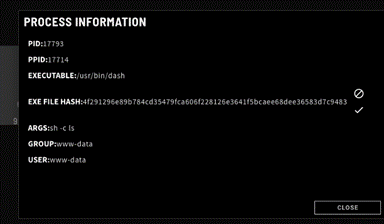
Additional detail about processes is available by clicking on them. As you can see, the dash process attempted to run the command “ls”.
Phase 3 Malware Payloads:
To allow the attack to proceed to phase 3, we disable yet another of ZeroLock’s protections and allow the attacker to use their webshell. Now that the attacker has shell access, they face another dilemma. They must launch their attack as the unprivileged www-data user.

Fortunately (or unfortunately) for their purposes, the attacker is launching a cryptojacking attack. Thus, privileged access is not required, because cryptominers do not require admin permissions to burn through the CPU on the quest for cryptocurrency.
The attacker attempts to download and run the popular cryptominer, XMRig. Once again, they are thwarted by ZeroLock. ZeroLock uses AI to detect cryptominers by inspecting the stream of instructions they execute. This advanced technique allows ZeroLock to detect cryptomining no matter the cryptocurrency or specific miner used. It avoids the pitfalls of using IOCs and IOAs that are easy for an attacker to change. Instead, it targets behavior that all cryptomining malware exhibits, no matter its form. This makes the detection future proof to new iterations of malware and crypto mining algorithms that attackers develop.
![]()
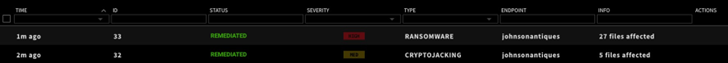
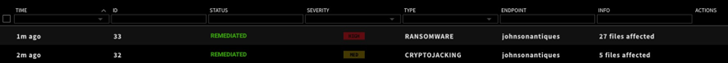
Unable to use the system for cryptomining, the attacker launches a ransomware attack that would disable the website until a ransom is paid using the malware Defray777.
The ransomware attack is detected by ZeroLock’s unique behavioral detection engine within milliseconds and automatic remediation kicks in to clean restore the system to it’s normal state.
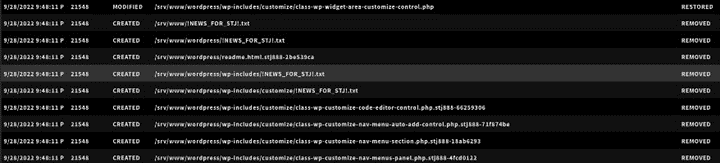
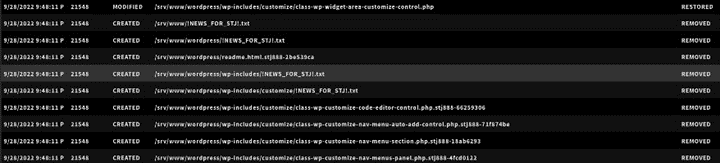
ZeroLock displays the list of any files affected by the ransomware. Thanks to ZeroLock’s patent-pending rollback capabilities for Linux, any encrypted files are restored to their original version in less than a second, ransom notes are cleaned up, attempts to make ransomware persistent are rolled back, any network connections the attacker was leveraging to launch their payload are severed, and the website is restored to full operational status.
Conclusion:
ZeroLock defeated the would-be hacker of this WordPress site at multiple points in the attack chain. ZeroLock provides one of the strongest protection options for securing WordPress sites, and other Linux based systems as well. ZeroLock provides comprehensive security for any Linux system, from on-premise, to cloud, and even IoT and edge devices, in an easy to install and manage package. This package inlcudes fine-grained access rules, multifactor authentication for SSH, ransomware and cryptojacking protection, automated remediations, and more.
To learn more about ZeroLock, email [email protected] and schedule a demonstration.
