Cybersecurity has become a critical concern across industries, but Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) are facing mounting pressure to secure not only their own operations, but also the vast networks they manage for their clients. As businesses increasingly rely on technology, Managed Partners (MPs) have emerged as valuable targets for cyberattacks. Service providers hold privileged access to numerous client networks, making them susceptible to a wide range of threats.
A 2024 survey revealed that 54% of MSPs reported their clients’ main reason for services was increasing concerns about cybersecurity risk. As cyber threats grow more sophisticated and destructive, so does the global cost of cybercrime, projected to reach $23.84 trillion by 2027. As MPs continue to cite cybersecurity threats as a top challenge, the implications are clear: they are on the front lines of this battle, responsible for safeguarding the IT infrastructures of hundreds, if not thousands, of clients.
There are several reasons why Managed Partners are prime targets.
Their ability to access numerous client environments makes them particularly valuable targets. Compromising a single MP can allow hackers to infiltrate multiple businesses in one fell swoop, giving them the opportunity to cause widespread damage, whether through ransomware, supply chain attacks, or other sophisticated methods.
In addition to having broad access to client networks, MPs manage complex, often virtualized environments that are ripe for exploitation. Hypervisors, which allow multiple virtual machines to run on a single physical server, have become both a cornerstone of efficiency and a glaring vulnerability. These systems create a critical single point of failure: if compromised, an attacker can bypass traditional security layers entirely. A breach at this level doesn’t just jeopardize a single machine—it hands over control of an entire virtualized environment, effectively exposing every machine, application, and network that depends on the hypervisor. The consequences are catastrophic, turning a single weakness into an entry point for widespread system control, data theft, or network destruction.
Among the most pressing threats Managed Providers face are ransomware and supply chain attacks, which have both escalated in scale and sophistication in recent years.
A large threat impacting the clients of Managed Providers today is ransomware, and these types of attacks are not isolated incidents but are part of a broader and growing trend of cyberattacks affecting industries across the board. Hypervisor attacks, like the infamous Johnson Controls attack, have become more frequent as cybercriminals recognize the vulnerability of these systems. Ransomware operations, like Eldorado and SEXi, have recently gained notoriety by specifically targeting vulnerable VMware ESXi systems. Additionally, many ransomware threat actors like Storm-0506, Storm-1175, Octo Tempest, Manatee Tempest, and others support or sell ESXi encryptors like Akira, Black Basta, Babuk, and Lockbit. By exploiting the virtualized infrastructure that hypervisors support, attackers can infiltrate not only individual virtual machines but potentially the entire client network hosted on the platform.
In addition to ransomware, MPs must contend with other significant cybersecurity risks, chief among them being supply chain attacks. These occur when attackers compromise third-party vendors that MPs rely on to manage and integrate software and hardware for their clients. A single vulnerability in a third-party service can create a ripple effect, impacting all of a Managed Provider’s clients. These attacks expose MPs to a dual threat: while they work to secure diverse client systems, they remain vulnerable to a single breach through the third-party vendors they rely on.
What can be done?
Service providers need to adopt a proactive, multi-layered approach to security that extends beyond basic defenses. By implementing advanced threat detection and real-time network monitoring, providers can catch potential breaches early and respond before threats escalate. AI detection is a key strategy against supply chain attacks, as it identifies suspicious behavior in software regardless of its origin. Likewise, securing hypervisors against ransomware attacks is critical, as vulnerabilities at this layer can give attackers control over entire virtual environments.
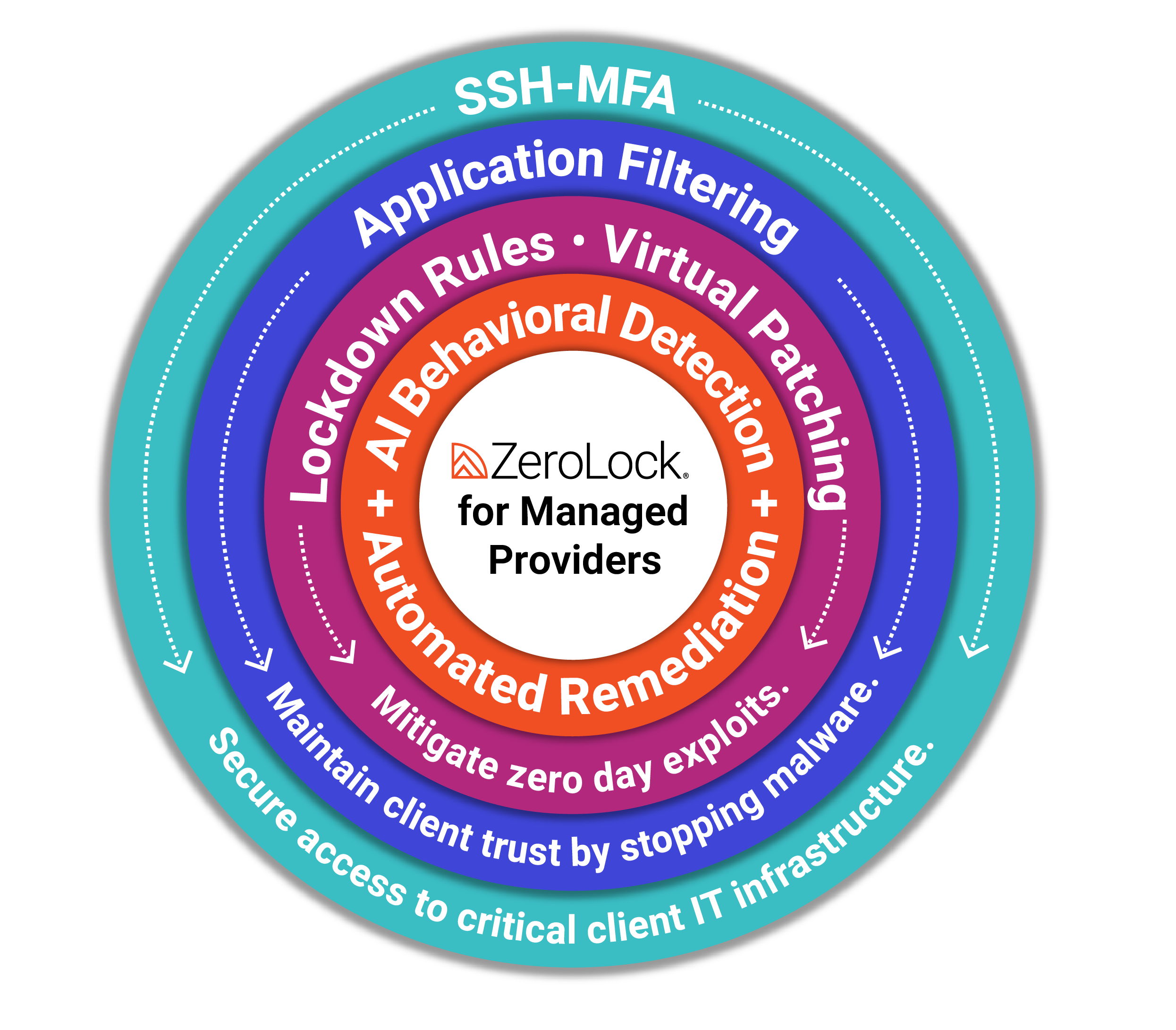
ZeroLock addresses these challenges by offering a solution specifically designed to protect hypervisors and prevent supply chain breaches. ZeroLock goes beyond traditional access control by implementing features such as SSH Multifactor Authentication (MFA) and application filtering, which ensure only authorized applications can run in the environment. Moreover, its process behavior controls and network access controls further lock down critical layers of infrastructure, making it incredibly difficult for attackers to exploit weaknesses.
ZeroLock’s AI detection system adds another critical layer by identifying malware in real time based on behavior, rather than relying on known malware signatures. This approach allows it to detect and stop even fileless ransomware with over 98% accuracy. In the event of an attempted breach, ZeroLock can automatically roll back file changes and remove attacker persistence without user intervention, minimizing downtime and disruption. These capabilities enable service providers to shift from reactive to proactive, closing gaps in real-time and locking down every layer of the network. The threat landscape isn’t waiting for anyone to catch up, and ZeroLock offers the foundation to stay ahead.
Final Thoughts
Modern business relies on service providers’ ability to outpace the growing sophistication of cyber threats. Organizations must redefine cybersecurity as a core service offering, where the ability to anticipate threats and adapt to them is just as important as direct protection itself. The next major breach won’t simply expose vulnerabilities—it will call into question the viability of those who are unprepared. Managed Providers must adopt a mindset that sees every day without an incident as a narrowing window of opportunity to strengthen their defenses. In our world of relentless cyber threats, complacency may be the biggest vulnerability.
