Aliases#
- DragonForce Malaysia (early hacktivist identity)
- DragonForce Ransomware Gang
- DragonLeaks (leak site)
- DFRansom
Figure 1: DragonForce data leak site.
Get Threat Intel and Security Updates Delivered to Your Inbox.#
Profiling#
Threat Actor Type: Initially a hacktivist collective (2021–2022), DragonForce evolved into a financially motivated ransomware-as-a-service (RaaS) cartel by late 2023. Current operations center on double extortion (encryption + data leak) and affiliate-driven campaigns.
Communications & Infrastructure:
- Active on Telegram (DragonForce Malaysia channel) and Russian-language forums like RAMP for affiliate recruitment.
- Maintains a Tor-based leak site DragonLeaks for victim shaming and ransom negotiations.
- Offers affiliates white-label ransomware kits, negotiation portals, and encrypted storage.
Expertise
- Customizable ransomware payloads based on LockBit 3.0 and Conti V3 leaked builders.
- Advanced encryption targeting Windows, Linux, ESXi, NAS, BSD systems.
- Exploits critical vulnerabilities (e.g., CVE-2024-21412, CVE-2024-21887) and uses Living Off the Land techniques for persistence.
Motivations#
- Primary: Profit via ransomware extortion and data leaks. Ransom demands range from hundreds of thousands to millions.
- Secondary: Residual ideological motives from hacktivist roots, occasionally influencing target selection.
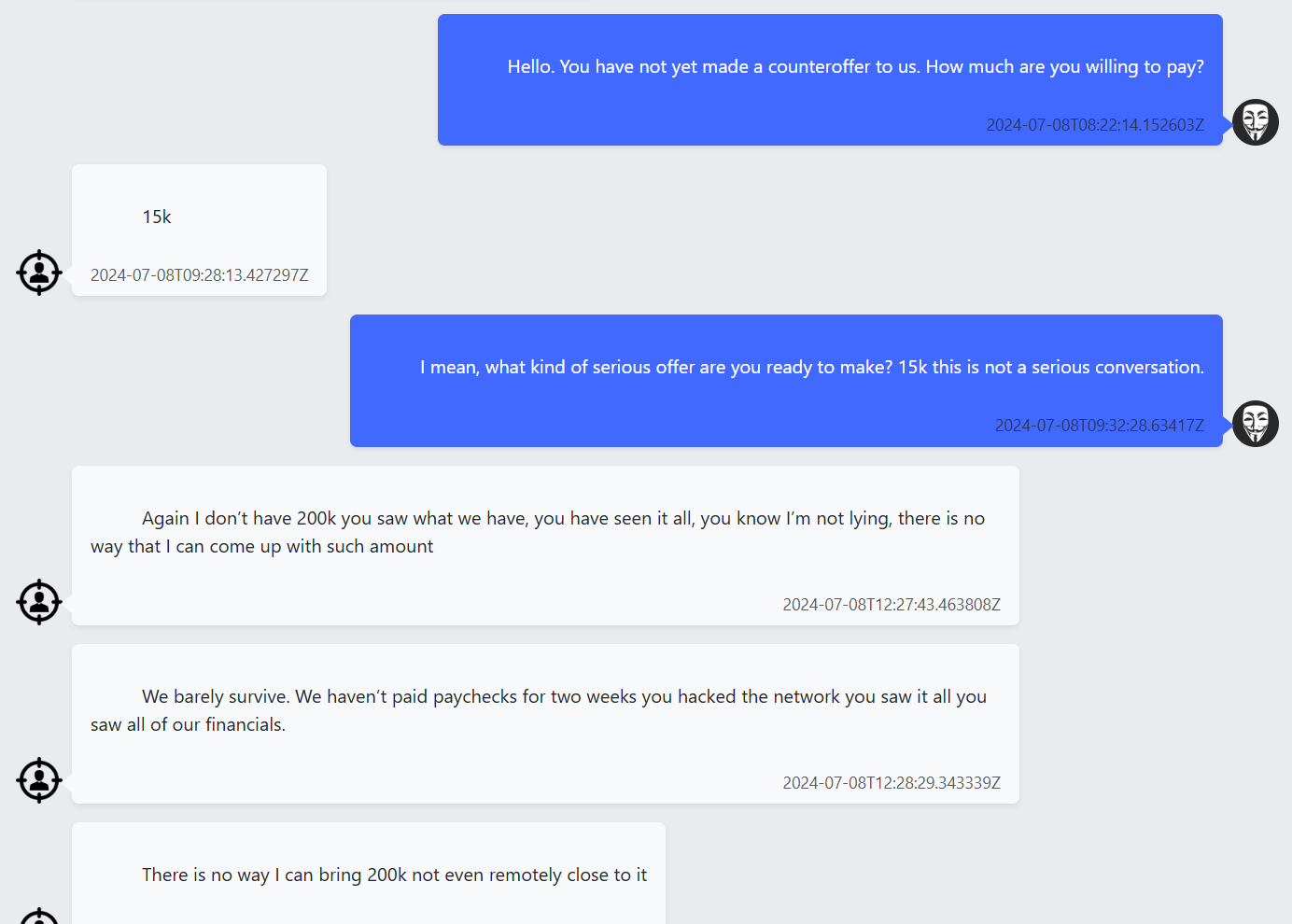
Figure 2: Negotiation chats with DragonForce.
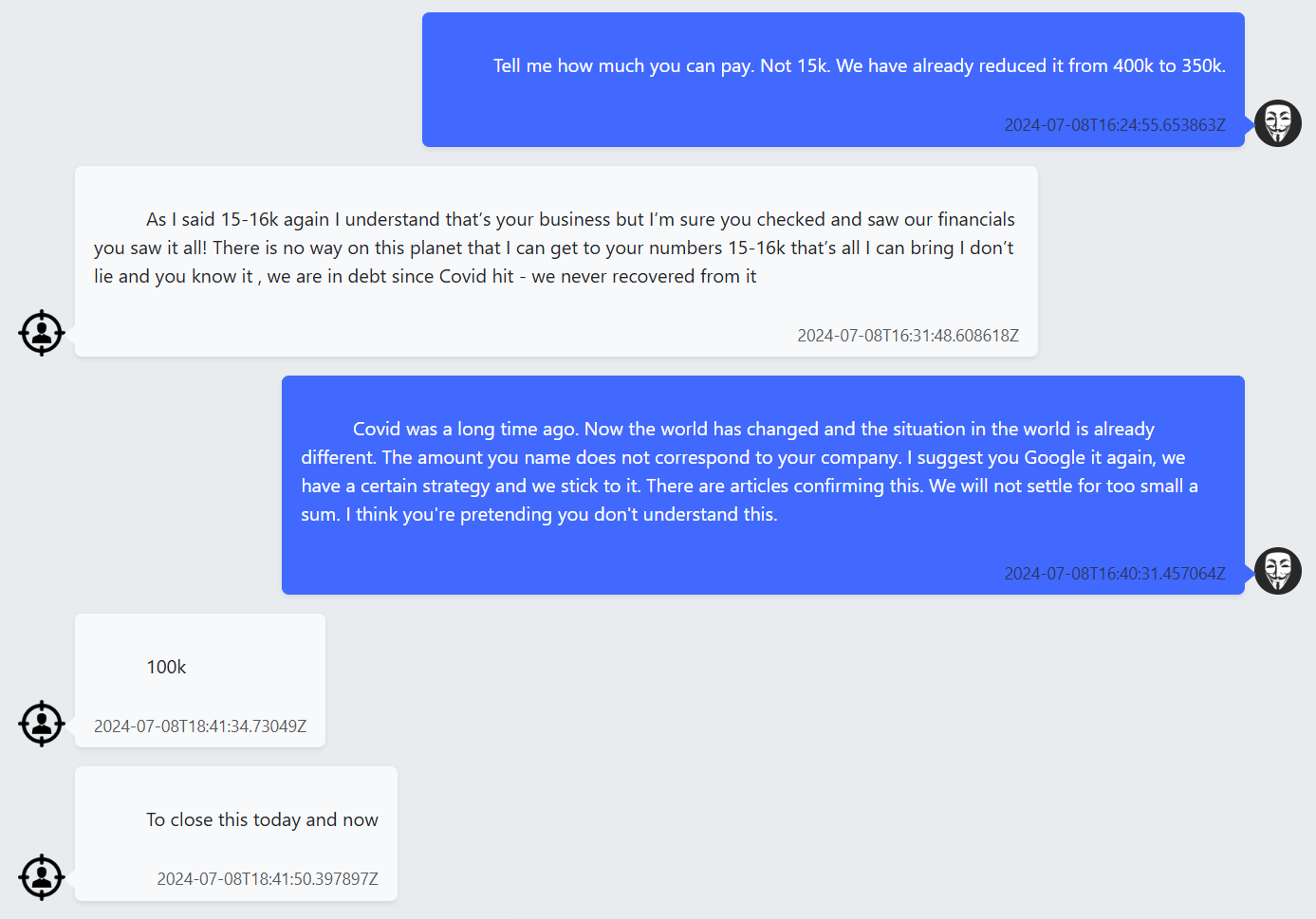
Figure 3: Victim agrees to pay 100K to DragonForce to release their data.
Timeline & Victimology#
2021–2022 – Hacktivist Phase #
DragonForce Malaysia launches #OpsBedil campaigns targeting Israel and India.
Aug 2023 – First Ransomware Indicators #
Early sightings of DragonForce ransomware variants based on LockBit 3.0 builder.
Dec 2023 – Launch of DragonLeaks Portal #
Public leak site goes live; first victims posted.
Jan–Jun 2024 – Affiliate Program Expansion #
DragonForce introduces RaaS model with 80% affiliate profit share. Victims include manufacturing and real estate firms in the U.S. and Asia-Pacific.
Summer 2024 – Conti-Based Variant Released #
Second ransomware strain deployed; enhanced encryption and customization.
Feb 2025 – Supply Chain Attack #
DragonForce exploits SimpleHelp RMM vulnerabilities (CVE-2024-57727/28/26) to compromise MSP environments, impacting multiple downstream customers.
Mar 2025 – Cartel Rebrand #
DragonForce announces “Cartel” structure; absorbs affiliates from collapsed RansomHub.
Apr–May 2025 – UK Retail Campaign #
Marks & Spencer, Co-op, and Harrods hit in coordinated ransomware spree:
- Marks & Spencer: ESXi encryption, 150GB data stolen, outages lasting weeks totaling $402M.
- Co-op: Customer/member data exfiltrated; supply chain disruption.
- Harrods: Breach contained quickly; precautionary internet restrictions.
Aug 2025 – Government & Lottery Targets #
Ohio Lottery and Government of Palau compromised; operations disrupted.
Current status (Nov 2025) – UAE Telecom Breach #
Du targeted; 44GB of sensitive data exfiltrated.
Victimology Overview:
- Sectors: Retail, government, manufacturing, healthcare, transportation, legal.
- Regions: U.S., U.K., Australia, Middle East, Asia-Pacific.
- Over 300 victims claimed since late 2023; 120+ confirmed in 2025 alone.
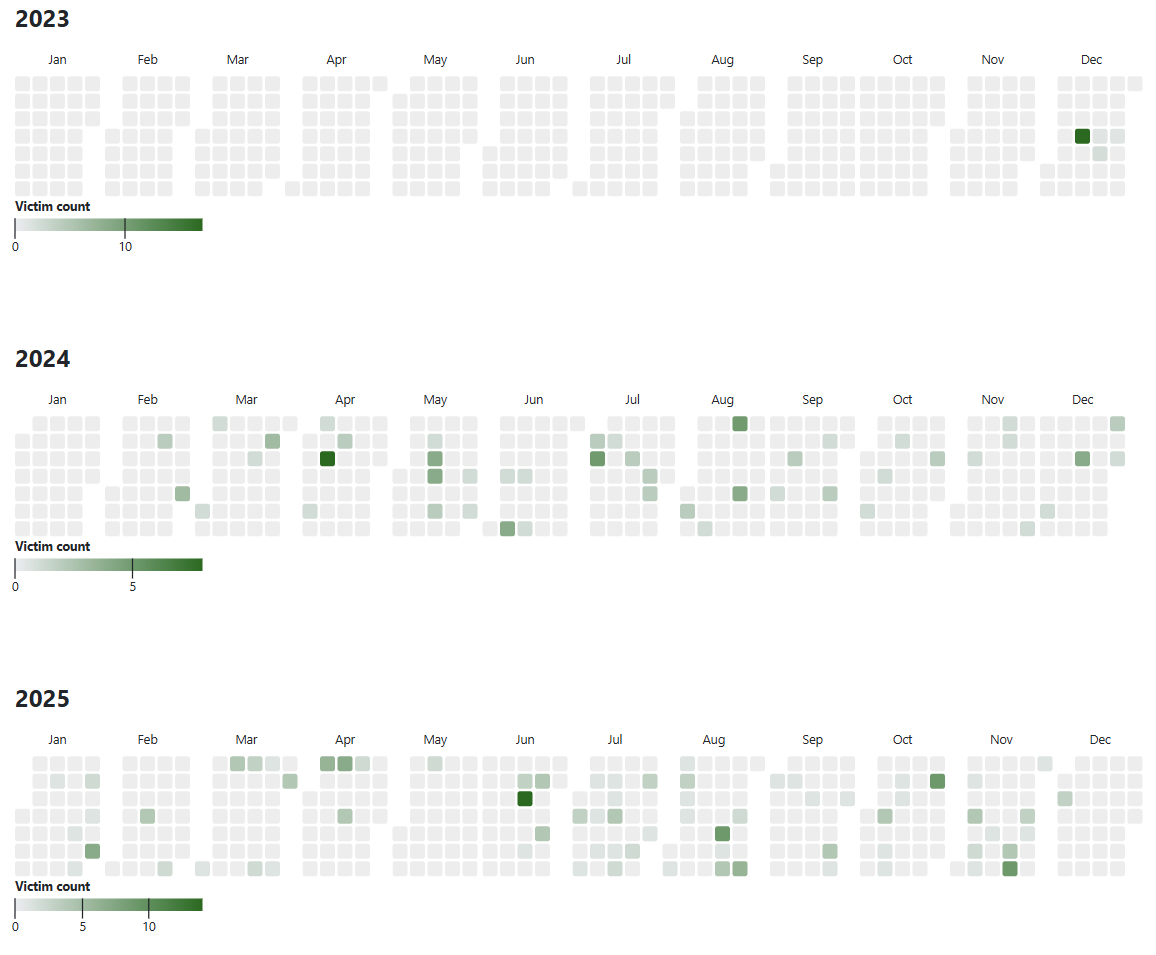
Figure 4: Victim heat map over the years.
Tactics & Techniques#
Initial Access #
- Exploit Public-Facing Application — T1190
- Phishing / Social Engineering — T1566
- Valid Accounts — T1078
- Trusted Relationship — T1199
Execution #
- Command and Scripting Interpreter (PowerShell) — T1059.001
Persistence & Privilege Escalation #
- Remote Access Tools (AnyDesk) — T1543.003
- Abuse Elevation Control Mechanism — T1548
Defense Evasion #
- Impair Defenses — T1562.001
- Indicator Removal — T1070.001
Credential Access #
- Credential Dumping — T1003
- MFA Fatigue / Social Engineering — T1621
Lateral Movement #
- Remote Services — T1021
Collection & Exfiltration #
- Automated Collection — T1119
- Exfiltration Over Web Services — T1567.002
Impact #
- Data Encrypted for Impact — T1486
- Double Extortion (Leak + Encryption)
Defensive Recommendations Against DragonForce#
- Enforce MFA and validate all IT-support requests.
- Patch vulnerabilities (CVE-2024-21412, CVE-2024-21887) promptly.
- Monitor for AnyDesk or unauthorized remote tools.
- Harden ESXi hosts; maintain offline backups.
- Track leak site mentions and affiliate chatter on forums.
References#
Botcrawl. (2025, November 21). Du data breach exposes sensitive telecommunications infrastructure and customer records. Retrieved from https://botcrawl.com/du-data-breach/
Botcrawl. (2025, November 30). Division 10 data breach exposes 126 GB of construction project files. Retrieved from https://botcrawl.com/division-10-data-breach/
BleepingComputer. (2025, July 8). M&S confirms social engineering led to massive ransomware attack. Retrieved from https://www.bleepingcomputer.com/news/security/mands-confirms-social-engineering-led-to-massive-ransomware-attack/
BleepingComputer. (2025, May 2). Co-op confirms data theft after DragonForce ransomware claims attack. Retrieved from https://www.bleepingcomputer.com/news/security/co-op-confirms-data-theft-after-dragonforce-ransomware-claims-attack/
BleepingComputer. (2025, May 27). DragonForce ransomware abuses SimpleHelp in MSP supply chain attack. Retrieved from https://www.bleepingcomputer.com/news/security/dragonforce-ransomware-abuses-simplehelp-in-msp-supply-chain-attack/
CyberSecurityNews. (2025, June 6). DragonForce ransomware claimed to compromise over 120 victims in the past year. Retrieved from https://cybersecuritynews.com/dragonforce-ransomware-claimed/
CyberSecurityNews. (2025, August 21). DragonForce ransomware attack analysis – targets, TTPs and IoCs. Retrieved from https://cybersecuritynews.com/dragonforce-ransomware-attack/
Dark Reading. (2025, July 31). DragonForce ransom cartel profits off rivals’ demise. Retrieved from https://www.darkreading.com/threat-intelligence/dragonforce-ransom-cartel-profits-rivals-demise
Dark Reading. (2025, May 27). DragonForce ransomware strikes MSP in supply chain attack. Retrieved from https://www.darkreading.com/application-security/dragonforce-ransomware-msp-supply-chain-attack
Infosecurity Magazine. (2025, May 6). Inside DragonForce, the group tied to M&S, Co-op and Harrods hacks. Retrieved from https://www.infosecurity-magazine.com/news/dragonforce-goup-ms-coop-harrods/
Infosecurity Magazine. (2025, February 27). DragonForce ransomware hits Saudi firm, 6TB data stolen. Retrieved from https://www.infosecurity-magazine.com/news/6tb-data-stolen-saudi-cyber-attack/
Infosecurity Magazine. (2025, November 4). DragonForce cartel emerges as Conti-derived ransomware threat. Retrieved from https://www.infosecurity-magazine.com/news/dragonforce-cartel-conti-derived/
Quorum Cyber. (2025, May). DragonForce ransomware report. Retrieved from https://www.quorumcyber.com/wp-content/uploads/2025/05/QC-DragonForce-Ransomware-Report.pdf
Quorum Cyber. (2025, March). Understanding the DragonForce ‘Cartel’: The cybercriminals targeting retailers with ransomware. Retrieved from https://www.quorumcyber.com/insights/understanding-the-dragonforce-cartel-the-cybercriminals-targeting-retailers-with-ransomware/
Ransomware.live. (2025). DragonForce ransomware group profile. Retrieved from https://www.ransomware.live/group/dragonforce
The Hacker News. (2025, May 29). DragonForce exploits SimpleHelp flaws to deploy ransomware across customer endpoints. Retrieved from https://thehackernews.com/2025/05/dragonforce-exploits-simplehelp-flaws.html
