Industry 4.0 is transforming manufacturing, making operations smarter, faster, and more efficient. But with increased connectivity comes increased risk. Hypervisor threats are evolving fast—especially for organizations relying on VMware ESXi to power their virtualized environments.
Many companies invest heavily in endpoint and network protection, yet overlook one of their most critical vulnerabilities: the hypervisor. Systems like VMware ESXi often go unprotected, creating massive hypervisor vulnerabilities that ransomware operators are eager to exploit. Without strong hypervisor ransomware protection, a single breach at this layer can result in complete infrastructure shutdown, corrupted data, and millions in operational losses.
The Ransomware Epidemic in Manufacturing
Ransomware is considered a top cybersecurity threat in manufacturing:
- 65% of manufacturers were hit by ransomware in 2024—a 41% increase since 2020.
- 21% of all ransomware attacks in 2024 targeted manufacturing, with 281 successful breaches in just the first six months.
- 55% surge in ransomware costs: manufacturing now loses an average of $1.67M per attack in 2024, up from $1.08M just a year prior.
- 11.6 days: The average downtime per attack, costing manufacturers $1.9M per day.
- 80% of manufacturers have at least one critical unpatched vulnerability, leaving them exposed to ESXi ransomware threats.
Despite these risks, most manufacturers don’t have proper hypervisor patch management in place—making ESXi virtual patching and hypervisor incident response critical to defense.
Hypervisors: The Industry’s Biggest Blind Spot
Hypervisors like VMware ESXi are the backbone of modern manufacturing—enabling virtualized environments, optimizing IT resources, and streamlining operations. But without hypervisor security, they become the ultimate attack vector.
If an ESXi hypervisor is compromised, attackers can:
- Move laterally across virtual machines—gaining full control over production systems, SCADA environments, and OT networks.
- Encrypt entire environments—locking down every virtual machine, bringing operations to a standstill, and demanding massive ransoms.
- Steal sensitive intellectual property—including proprietary manufacturing processes, blueprints, and trade secrets, leading to competitive losses.
A single hypervisor breach can cripple production, devastate supply chains, and cost millions. Yet many manufacturers still lack both visibility and hypervisor ransomware prevention strategies.
Attackers are specifically targeting ESXi vulnerabilities—knowing that traditional endpoint tools won’t detect or stop these hypervisor-level threats.
How to Protect ESXi from Ransomware
Traditional security tools aren’t enough. Firewalls can’t stop all hypervisor attacks, and endpoint protection won’t detect them. To build a resilient foundation, manufacturers should adopt a dedicated hypervisor security tool and follow hypervisor security best practices to prevent ESXi ransomware attacks.
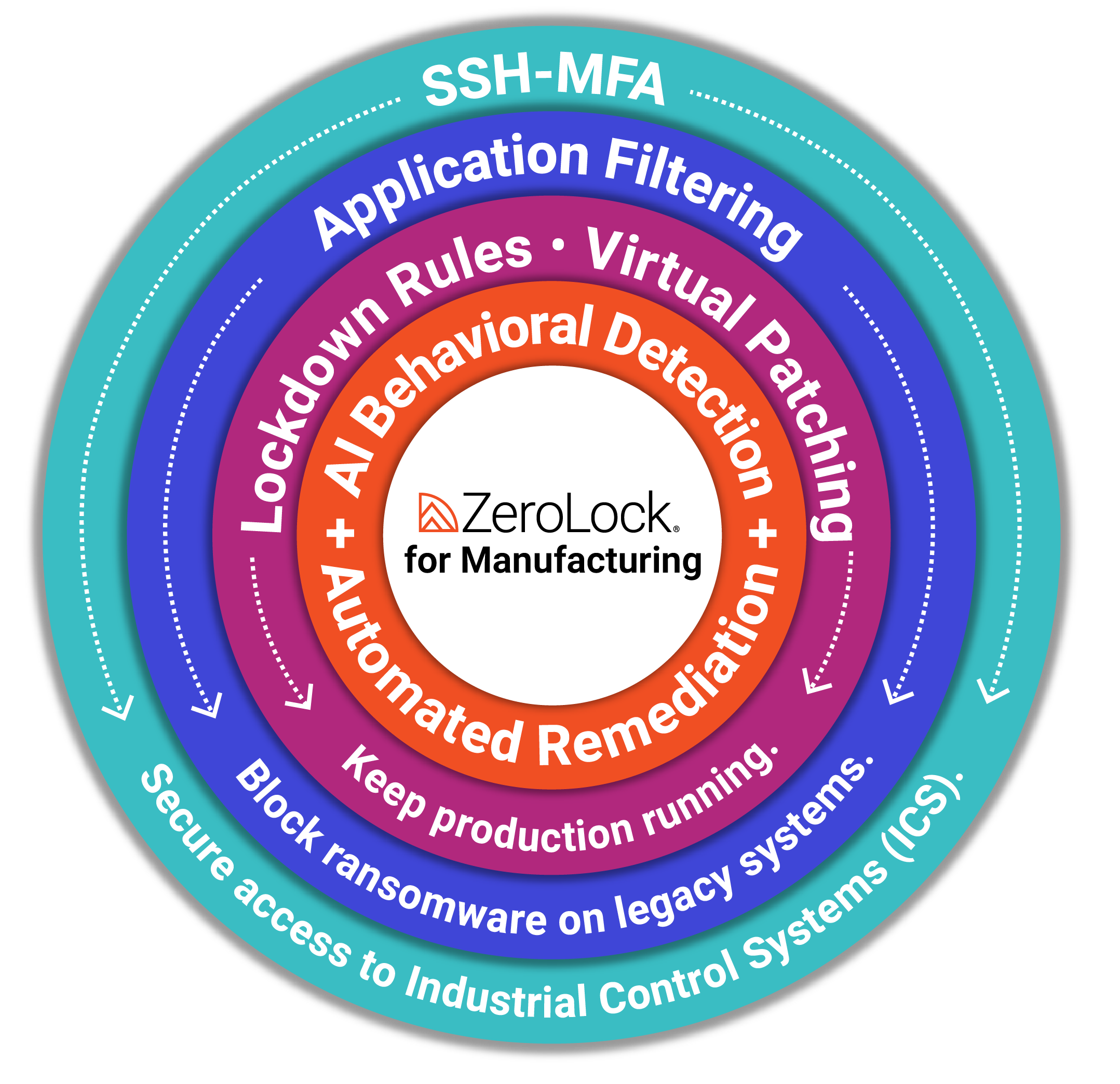
Hypervisor Security Tips for Ransomware Prevention
- Deploy an ESXi security tool: Use a purpose-built solution like ZeroLock®, designed specifically for VMware ESXi security and hypervisor ransomware prevention.
- Use AI Detection: Monitor for unusual activity that could indicate an attack on hypervisor layers.
- Enforce MFA: Secure ESXi consoles and hypervisor access points with multi-factor authentication.
- Implement Application Filtering: Stop ransomware before it launches by blocking unapproved software across virtual machines.
- Automate Recovery: Use instant file rollback to restore infected hypervisors and reduce downtime.
- Adopt Hypervisor Patch Management Strategies: Leverage hypervisor virtual patching to shield systems from known and zero-day vulnerabilities—even when official updates are delayed.
Final Thoughts: Don’t Wait to Secure Your ESXi Hypervisors
Hypervisor ransomware isn’t a future threat—it’s already here. And ESXi ransomware protection is no longer optional. With attackers actively exploiting hypervisor vulnerabilities, manufacturers must secure their virtualized environments before it’s too late.
From hypervisor security tools to ESXi virtual patching, manufacturers need a proactive strategy built around hypervisor security best practices and real-time threat detection. Don’t wait for disaster to strike—secure your VMware ESXi hypervisors with tools and tactics designed to prevent hypervisor-level breaches.
How secure are your hypervisors?
